A staggering claim of a data breach involving 2.87 billion user records from X has surfaced, allegedly marking the largest social media data leak in history.
The breach, disclosed by a threat actor known as “ThinkingOne” on Breach Forums, has raised significant concerns about user privacy and corporate security practices.
However, questions remain about the authenticity of the dataset, as X’s active user base is far smaller than the reported figure.
The Alleged Breach
According to the post from HackManac, the dataset, reportedly 400GB in size, includes detailed metadata of user profiles, such as account creation dates, screen names, follower counts from 2021 and 2025, tweet timestamps, and profile descriptions.
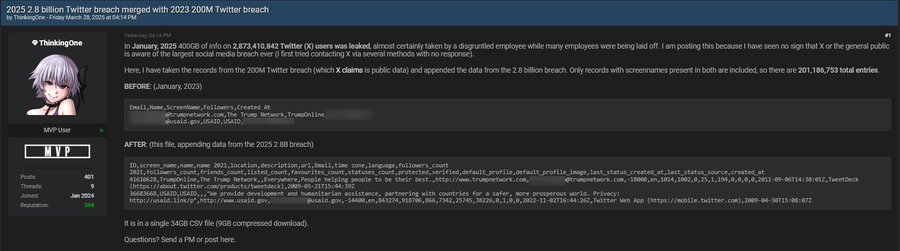
Notably absent are sensitive elements like email addresses or passwords, distinguishing this breach from previous incidents.
ThinkingOne claims the data was exfiltrated during mass layoffs at X in early 2025 by a disgruntled employee—a theory yet to be verified.
Adding to the intrigue, ThinkingOne merged this dataset with records from a January 2023 breach that exposed the email addresses and public profile data of over 200 million users.
The combined file contains 201 million entries in a compressed 9GB CSV format. This fusion of datasets has led to confusion about the scope of leaked information.
Does X Even Have 2.8 Billion Users?
The claim of 2.87 billion user records has sparked skepticism. As of January 2025, X reportedly had approximately 540 million active users globally.
Experts suggest that the inflated figure could include historical data from inactive or banned accounts, bot profiles, or even non-user entities such as API accounts and developer bots.
Another possibility is that the dataset aggregates information scraped from multiple sources beyond X itself.
Technical Analysis of the Data
The leaked data provides a snapshot of user activity over time but lacks critical private information like passwords or financial details.
A sample analysis by cybersecurity researchers confirmed the authenticity of some records but noted inconsistencies in ownership verification for associated email addresses.
This raises concerns about potential misuse for phishing or identity theft through social engineering attacks.
Below is an example code snippet illustrating how such datasets might be processed:
pythonimport pandas as pd
# Load the dataset (example CSV file)
data = pd.read_csv('leaked_data.csv')
# Display key columns
print(data[['user_id', 'screen_name', 'followers_count', 'last_tweet_timestamp']])
# Filter users with high follower counts
high_followers = data[data['followers_count'] > 100000]
print(high_followers)
This kind of analysis could be used by both researchers and malicious actors to extract insights from leaked datasets.
The Role of ThinkingOne
ThinkingOne is not known for conducting breaches but is highly regarded for analyzing leaked data.
Their decision to release this dataset publicly stems from frustration over X’s lack of response to their attempts at disclosure.
This aligns with broader trends where insider threats and organizational restructuring create vulnerabilities for data leaks.
X’s Silence and Implications
Despite the magnitude of these claims, X has not issued any public statements regarding the breach. This silence raises questions about transparency and accountability in handling user data.
The incident underscores the importance of robust cybersecurity measures and proactive responses to potential threats.
Whether or not this breach truly involves 2.87 billion users, it highlights critical vulnerabilities in modern digital ecosystems.
Organizations must prioritize securing sensitive information against both external attacks and insider threats while maintaining clear communication with affected users to mitigate reputational damage.
This incident serves as a stark reminder: in an era where data is currency, its protection must be paramount.
Also Read: