Security researchers from Cisco Talos in collaboration with The Vertex Project have unveiled a new analytical mechanism designed to more effectively track and profile compartmentalized cyber threats.
This innovation arrives as the cybersecurity community faces a marked shift: modern attack kill chains are increasingly being orchestrated by multiple, discrete threat actors, each responsible for distinct phases-ranging from initial compromise to exploitation and monetization.
This fragmentation complicates traditional threat actor profiling and attribution, highlighting the critical need for updated technical methodologies.
The Limitations of Existing Intrusion Models
Traditionally, the cybersecurity industry has relied on models such as the Diamond Model of Intrusion Analysis and the Cyber Kill Chain to reconstruct attacks and profile adversaries.
The Diamond Model, with its four-quadrant approach-adversary, capability, infrastructure, and victim-has been effective for mapping single-actor intrusions.
However, as Cisco Talos notes, its feature-centric framework can lead to misattribution and analytical blind spots when applied to compartmentalized attacks, where multiple, loosely affiliated groups interact within an overarching intrusion.
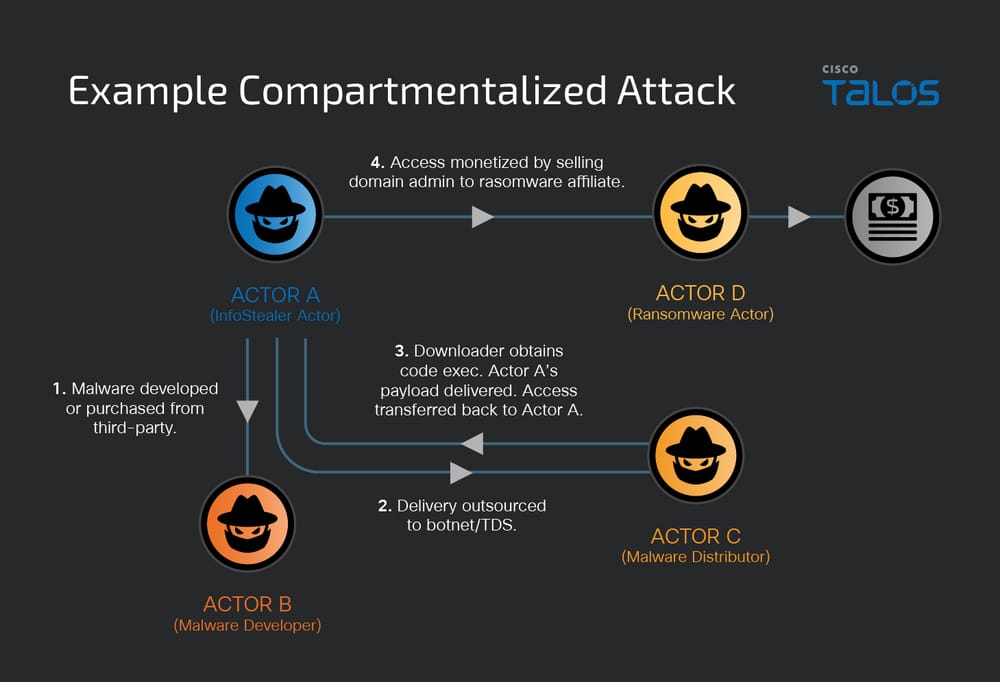
In recent campaigns, adversaries have been observed outsourcing tooling, renting infrastructure, and even selling or transferring compromised access between groups.
In such scenarios, a single victim can be targeted sequentially by different cybercriminals, each with differing motivations and techniques.
This multifaceted collaboration challenges the underlying assumptions of classical models, which were designed under the premise of a single-actor operational chain.
To address these analytical deficits, Cisco Talos and The Vertex Project have extended the Diamond Model to include a “Relationship Layer.”
This addition contextualizes the interplay between the traditional four features of the model, enabling security analysts to articulate and track transactional, commercial, and operational relationships among threat actors and their assets.
For example, the Relationship Layer clarifies situations where infrastructure is “purchased from” a broker, or where access is “handed over” from one actor to another-information critical for accurate threat profiling.
This enhanced model is particularly effective in analyzing campaigns characterized by operational outsourcing, shared tooling, and access brokering, such as the financially-motivated initial access (FIA), ransomware, and state-sponsored actor collaborations.
Case Study: The ToyMaker Campaign
The application of this extended model was demonstrated in the ToyMaker campaign investigation.
In this incident, initial access to a corporate network was obtained by a financially-motivated group, ToyMaker, which subsequently sold or transferred access to the Cactus ransomware group.
Analysis revealed non-overlapping tactics, techniques, and procedures (TTPs) and a clear temporal gap between the phases, refuting the assumption of a single actor.
Shared credentials between the two groups ultimately confirmed the compartmentalized nature of the breach.
By leveraging the Relationship Layer, analysts were able to map out the interactions and transitions between the initial access broker and ransomware operator, significantly improving attribution accuracy and threat actor profiling.
The introduction of the Relationship Layer represents a significant advance for both threat hunting and defensive operations.
It allows defenders to systematically identify, prioritize, and respond to threats in environments where operational control and attack infrastructure may change hands multiple times during a compromise.
Security teams can more effectively hunt for early indicators of compromise, such as unique backdoors or credential theft, and trace the downstream risks posed by compartmentalized actor collaborations.
In an era marked by the commoditization of cybercrime services and the rise of highly specialized threat actor ecosystems, this model extension provides much-needed granularity and clarity.
As threat landscapes continue to evolve, such technical innovations will be crucial in maintaining effective detection capabilities and robust incident response strategies.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant updates