Security researchers uncovered a sophisticated malware campaign leveraging the AutoIT scripting language to deploy malicious payloads and establish persistence on Windows systems.
AutoIT, traditionally a legitimate tool for Windows automation, continues to play a notable role in the malware ecosystem due to its versatility and ease of interaction with the operating system’s components.
The latest campaign stands out for its use of multiple AutoIT layers and elaborate obfuscation techniques to evade detection and maintain a foothold on infected machines.
Obfuscated Entry Point
The attack begins with the distribution of an AutoIT-compiled executable titled “1.Project & Profit.exe” (SHA256: b5fbae9376db12a3fcbc99e83ccad97c87fb9e23370152d1452768a3676f5aeb).
Once executed, the binary reveals several hardcoded paths and URLs within its decompiled code, indicating its stepwise behavior.
The script is programmed to download an additional AutoIT interpreter and another AutoIT script, saving them in the public user profile directory.
Specifically, it fetches “Guard.exe” and a script named “Secure.au3” from remote servers, along with a PowerShell script (“PublicProfile.ps1”), which is immediately generated and executed.
In this phase, the malware establishes persistence through a subtle yet effective technique.
It creates a specially crafted “.url” shortcut in the Windows Startup folder, ensuring that every user login triggers a JavaScript file (“SwiftWrite.js”).
This JavaScript, in turn, reignites the AutoIT interpreter with its second-stage script (“G”), keeping the malicious processes running even after system reboots or user logouts.
Advanced Obfuscation
The second layer of AutoIT code exhibits heavy obfuscation, making analysis challenging.
All operational strings within the script are encoded using a custom function named “Wales”, which decodes strings stored as sequences of character codes.
Security analysts were able to replicate the decoding logic in Python, revealing that these strings control operations like process checks and further execution flow.
An example demonstrates the obfuscation: the encoded sequence “80]114]111]99]101]115]115]69]120]105]115]116]115]40]39]97]118]97]115]116]117]105]46]101]120]101]39]41” decodes to “ProcessExists(‘avastui.exe’)”, illustrating the script’s checks for antivirus processes to potentially alter its behavior or avoid detection.
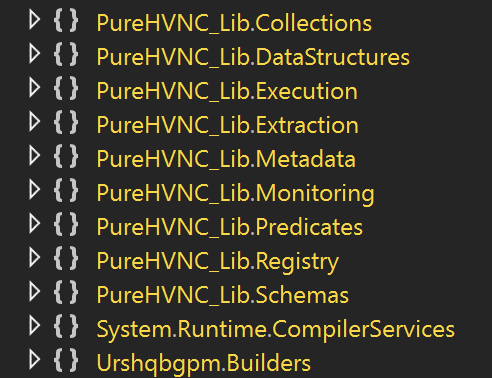
The campaign’s final stage involves execution of a malicious DLL-Urshqbgpm.dll-by injecting it into a newly spawned “jsc.exe” process.

Examination of the DLL suggests a connection to known malware strains such as PureHVNC, a popular remote access tool often employed for covert control and data exfiltration.
Network analysis of the affected systems shows attempts to communicate with a command-and-control (C2) server at 139[.]99[.]188[.]124 on port 56001, which has previously been linked to AsyncRAT operations.
According to the ISC Report, this implies that the attackers might be combining multiple off-the-shelf tools to maximize control and flexibility during their campaigns.
This campaign underscores how attackers increasingly use legitimate scripting environments like AutoIT to bypass traditional security controls.
By chaining multiple scripting languages-AutoIT, PowerShell, and JavaScript-and layering obfuscation, the attackers significantly complicate detection and remediation efforts.
Security professionals are advised to monitor for unusual use of scripting interpreters, scrutinize startup folders for suspicious shortcuts, and deploy behavioral analysis to catch such advanced threats before they can fully compromise Windows environments.
As the use of living-off-the-land binaries and dual-use tools continues to rise, organizations must remain vigilant and adapt their defenses to this evolving threat landscape.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant updates