In cyber threat actors have been operating a deceptive phishing website impersonating the trusted DigiYatra Foundation, a digital public infrastructure initiative promoted by the Government of India.
The fraudulent domain, digiyatra[.]in, which at the time of reporting remained accessible, was engineered to harvest personal user data under the false guise of delivering official DigiYatra-related services.
Despite bearing the name of the government-backed application, security analysts observed that the site’s design and operational behavior deviated considerably from legitimate DigiYatra platforms.
Continuous digital surveillance by ThreatWatch360, as part of its Early Warning Threat Detection program, played a critical role in the prompt identification of this high-severity threat.
By monitoring domain registrations containing public-sector keywords such as “DigiYatra,” their system flagged digiyatra[.]in due to its exact keyword match.
Further scrutiny revealed the site to be a clear case of unauthorized and malicious impersonation.
Automated and manual alerts were swiftly dispatched to ThreatWatch360’s brand monitoring clients and national partners, facilitating timely awareness and response coordination.
Data Harvesting in the Guise of Booking Services
Analysis of the fraudulent website revealed a purposeful intent to mislead.
Although the domain directly mirrored the authentic DigiYatra brand, the web content masquerading as a flight ticket booking portal did not correspond to any legitimate offering from the DigiYatra Foundation.
Users visiting the site encountered a flight search interface and a user registration form soliciting sensitive personal details such as name, phone number, and email address.
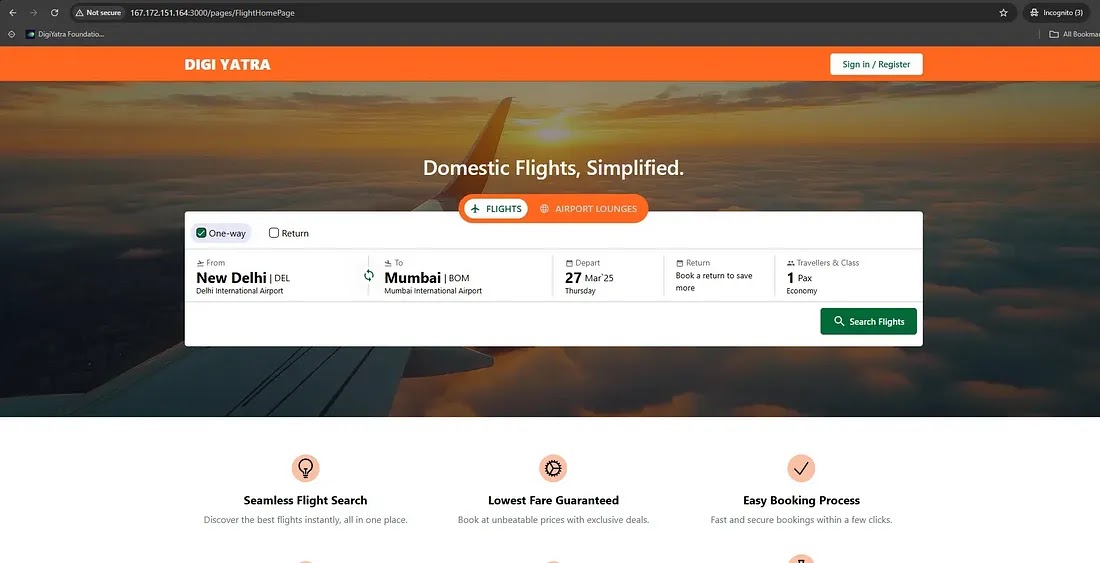
Threat research teams confirmed that, despite presenting a front for booking services, no actual ticketing operations were taking place.
Instead, the infrastructure was optimized exclusively for harvesting personally identifiable information (PII) by exploiting user trust.
The technical investigation uncovered additional indicators of compromise, including the utilization of a Let’s Encrypt SSL certificate a free and automated encryption solution giving unsuspecting visitors a false sense of security.
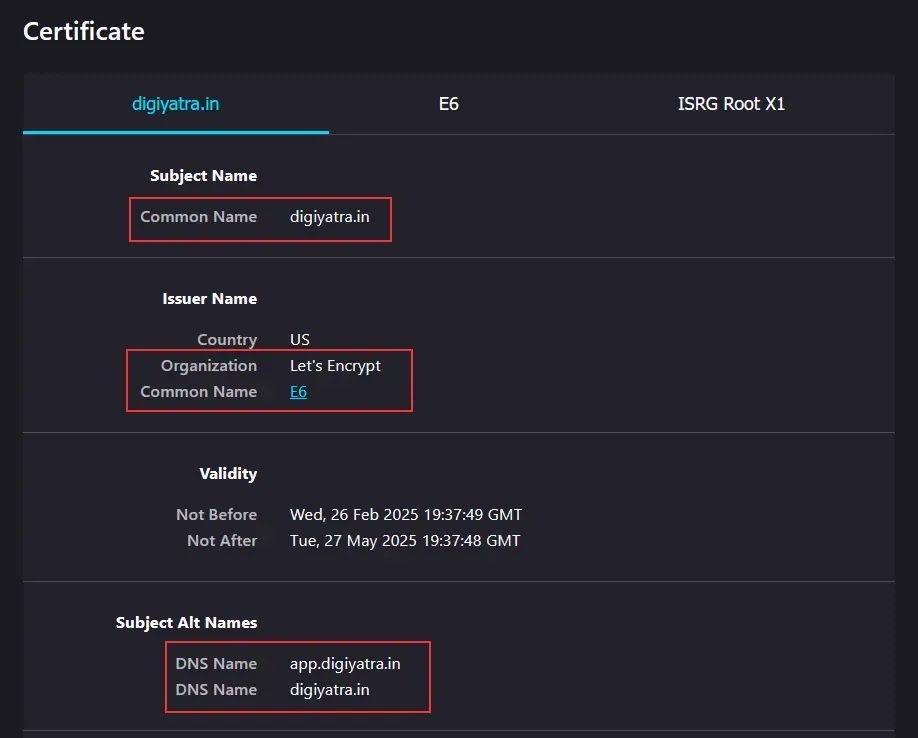
The domain, registered to an individual in Kerala, had been active since July 2022 and was configured to remain operational until at least July 2025.
Direct access to the associated IP address (167[.]172[.]151[.]164) further broadened the threat landscape.
National Security and Public Confidence at Risk
Experts at ThreatWatch360 emphasized the multifaceted risks posed by the operation of this phishing domain.
Aside from the clear data privacy threat, the campaign actively misled the public by appropriating a government program’s trusted identity, eroding public confidence in digital government initiatives.
The convincing yet false interface was sophisticated enough to deceive non-technical users, amplifying the potential impact.
Upon detection, ThreatWatch360 initiated an aggressive containment and mitigation protocol: alerting brand protection clients, notifying CERT-In and relevant government entities, submitting takedown requests to the domain registrar, and advising DNS-level blocks for the malicious domain and its IP.
According to the Report, The company also expanded its surveillance to monitor related domains employing variant keyword patterns, preempting further impersonation attempts.
This incident underscores the urgent need for proactive brand protection and impersonation detection among organizations stewarding public-facing digital initiatives especially those closely aligned with government branding.
In an environment where attackers rapidly exploit trusted names and official imagery, complacency is no longer an option.
ThreatWatch360 continues to deliver 24/7 domain abuse monitoring, real-time phishing detection, and executive brand misuse surveillance, reinforcing the digital safety nets for both institutions and end-users.
Authorities and the public are strongly advised to access DigiYatra services only through the official Foundation portal (hxxps://www[.]digiyatrafoundation[.]com), and to exercise vigilant caution with similarly named or styled websites even those employing HTTPS encryption.
The ongoing commitment to rapid detection, coordinated response, and comprehensive brand protection remains essential in defending the integrity of India’s digital public infrastructure.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates.