Cyble Research and Intelligence Labs (CRIL) has uncovered a coordinated campaign involving over 20 malicious Android applications on the Google Play Store designed to steal cryptocurrency wallet mnemonic phrases.
These apps impersonate legitimate platforms like PancakeSwap, SushiSwap, and Raydium, leveraging compromised developer accounts and phishing infrastructure linked to 50+ domains.
Technical Analysis of Phishing Infrastructure
The apps employ two primary attack vectors:
- Median Framework Exploitation: Threat actors used this development framework to convert phishing websites into Android apps. Configuration files embed URLs like hxxps://pancakefentfloyd[.]cz/api.php (hosted on IP 94.156.177[.]209) that load fake wallet interfaces via WebView.
- Direct WebView Loading: Some apps bypass frameworks entirely, directly loading phishing domains such as
hxxps://piwalletblog[.]blogto mimic Raydium’s interface.
Malicious apps reused package naming patterns (e.g., co.median.android.pkmxaj for Pancake Swap clones) and hid Command-and-Control (C&C) URLs in the privacy policy document.
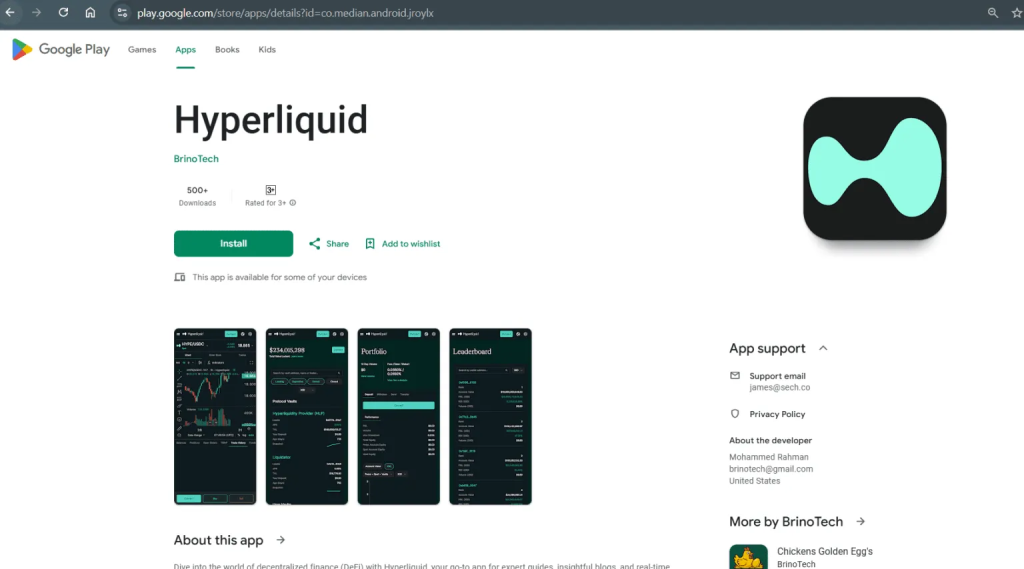
Compromised developer accounts—previously hosting gaming apps with 100,000+ downloads—were repurposed to distribute these threats, evading initial store vetting.
Risk Assessment
| Risk Factor | Impact | Likelihood |
|---|---|---|
| Mnemonic Phrase Theft | Irreversible cryptocurrency loss | High |
| Compromised Dev Accounts | Large-scale distribution via trusted channels | Moderate |
| WebView-based Phishing | Bypasses traditional URL scrutiny | High |
Key Indicators:
- Hashes:
4b35a1ed93ab68f0401de34d4eb5dbb582465ee2a8428e16d0beac8bf87a09af(PancakeSwap clone)1 - Domains:
pancakefentfloyd[.]cz,hyperliqw[.]sbs,raydifloyd[.]cz - IP: 94.156.177[.]209 (hosting 50+ phishing domains)
Mitigation Strategies for Users and Developers
- Verification Protocols:
- Cross-check app permissions and demand biometric authentication for wallet access.
- Enable Google Play Protect and scrutinize privacy policy links.
- Infrastructure Monitoring:
- Developers should monitor for package name squatting (
co.median.android.*) and domain impersonations.
- Developers should monitor for package name squatting (
- Threat Intelligence Integration:
- Deploy IOC-based blocking for known malicious hashes and domains listed above.
The campaign underscores critical vulnerabilities in app store vetting processes and the escalating sophistication of cryptocurrency-targeted social engineering.
With irreversible asset theft as the primary consequence, proactive defense measures are essential to mitigate risks in an increasingly mobile-first crypto ecosystem.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates