A dramatic escalation in cyberattacks has been observed with the emergence of ClickFix, a novel social engineering technique that has quickly become the second most prevalent attack vector after phishing.
According to recent threat telemetry, detections of ClickFix attacks tracked as HTML/FakeCaptcha have soared by an astonishing 517% between the second half of 2024 and the first half of 2025, now accounting for nearly 8% of all blocked cyber incidents.
This rapid proliferation positions ClickFix as one of the fastest-growing threats in the current cybersecurity landscape.
Technical Modus Operandi
ClickFix attacks exploit the ubiquity and user familiarity with online verification mechanisms, such as CAPTCHAs and error prompts.
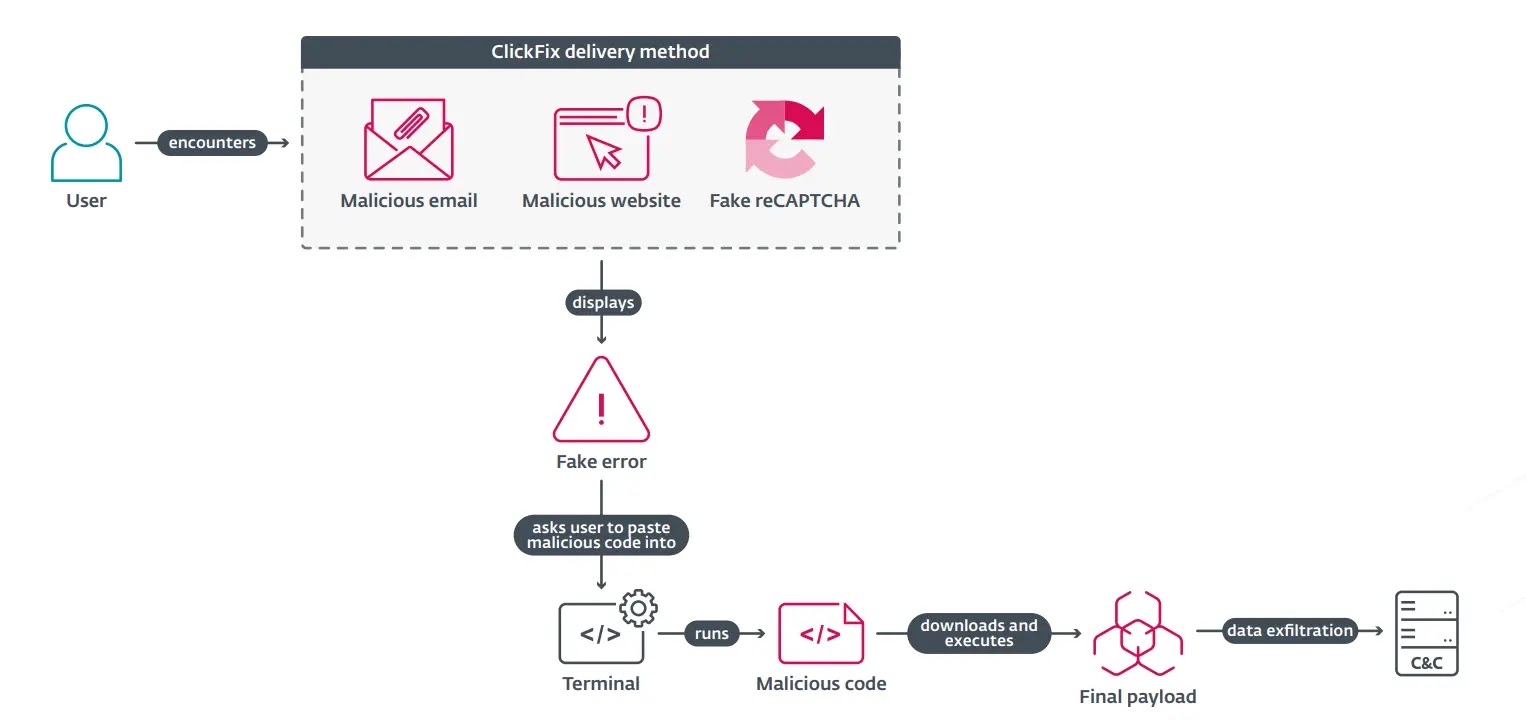
Attackers craft convincing fake error or verification messages often mimicking trusted brands like Microsoft Word, OneDrive, Booking.com, or Google Meet which instruct users to resolve a fabricated issue by clicking a “Fix it” button.
This action surreptitiously copies a malicious PowerShell command or script to the victim’s clipboard.
The user is then directed to open a terminal or command prompt and paste the contents, unknowingly executing code that initiates a multi-stage infection chain.
The payloads delivered via ClickFix are diverse and increasingly sophisticated, including infostealers (such as Lumma Stealer, VidarStealer, StealC, and Danabot), ransomware (notably Interlock, formerly Rhysida), remote access trojans (VenomRAT, AsyncRAT, NetSupport RAT), cryptominers, post-exploitation frameworks (Havoc, Cobalt Strike), and custom malware attributed to nation-state actors.
The attack chain is often obfuscated, with multiple detection names covering the various scripts, executables, and payloads, suggesting the actual prevalence of ClickFix is likely underreported.
Threat Actor Adoption
According to the Report, ESET telemetry highlights that the highest volumes of ClickFix detections have been reported in Japan (23%), Peru (6%), with Poland, Spain, and Slovakia each registering over 5%.
The technique first surfaced in March 2024 in campaigns attributed to groups such as ClearFake and TA571, initially distributed through phishing emails with malicious HTML attachments.
Since then, the approach has been widely adopted, with threat actors compromising legitimate websites, deploying fake browser update prompts, and distributing ClickFix links via email and even through issues in popular GitHub repositories.

The effectiveness and simplicity of ClickFix have led to the emergence of builder kits sold on underground forums, enabling a broader spectrum of cybercriminals to weaponize landing pages with minimal technical expertise.
Notably, nation-state-aligned groups including North Korea’s Kimsuky, Lazarus, and DeceptiveDevelopment, as well as Russia’s Callisto and Sednit, Iran’s MuddyWater, and Pakistan’s APT36 have incorporated ClickFix into their initial access toolkits, targeting Windows, macOS, and Linux environments.
The multi-stage nature of ClickFix attacks allows for interception at several points, including malicious URLs, HTML email attachments, HTA and JavaScript files, PowerShell scripts, and command-line programs.
Robust security solutions are advised to block obfuscated payload “envelopes,” monitor for anomalous PowerShell usage, and detect suspicious in-memory or network activity indicative of data exfiltration.
Security experts warn that users should exercise heightened vigilance against unsolicited “one-click” or “copy-and-paste” fixes, particularly those originating from untrusted sources.
In enterprise environments, endpoint detection and response (EDR) tools are recommended to flag unusual script executions, especially on systems where such activity is rare.
Given the technique’s alarming growth and effectiveness, industry analysts anticipate that major operating system vendors and the open-source community may soon implement security warnings similar to those for macro execution in office documents to alert users before running potentially dangerous scripts copied from the web.
As ClickFix continues to evolve, its success underscores the urgent need for user education, advanced threat detection, and coordinated industry response to counter this rapidly escalating cyber threat.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant updates