A sophisticated global cybercrime campaign, codenamed “ClickTok,” has been uncovered by threat intelligence firm CTM360, impacting TikTok Shop users across continents.
This multi-pronged scam leverages over 10,000 fraudulent domains that convincingly impersonate TikTok Shop, TikTok Wholesale, and TikTok Mall, posing a significant threat to user security and financial well-being.
The operation blends phishing tactics and malware deployment, marking a fresh escalation in the abuse of popular social commerce platforms.
Dual Threat: Phishing and SparkKitty Malware
The ClickTok campaign lures victims by distributing fake Meta advertisements and AI-generated influencer videos on Facebook and TikTok. Users are enticed with “exclusive deals” or access to lucrative affiliate programs.
Once engaged, they are redirected to lookalike domains—frequently using cheap or free top-level domains such as .top, .shop, and .icu designed to capture TikTok login information or prompt the installation of malicious apps.
A critical addition to the threat arsenal is the SparkKitty Trojan, a sophisticated spyware disguised as a seemingly authentic TikTok app.
The Trojan first presents a familiar but outdated TikTok interface, then exploits login mechanisms by allowing only Google OAuth sign-ins.
After authentication, the malware renders a fake “TikTok Shop” dashboard and abuses WebView to trick users into re-entering their credentials, harvesting usernames, passwords, and potentially session cookies for account takeover.
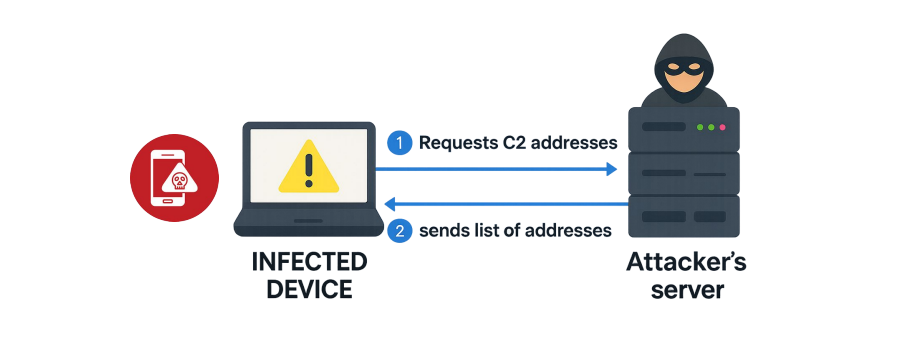
Upon infection, the compromised device connects to a hardcoded command-and-control (C2) infrastructure, such as the domain https://aa.6786587.top, to exfiltrate sensitive data.
SparkKitty’s functionality includes scraping device galleries, fingerprinting device hardware, and stealing crypto wallet data, with exfiltration orchestrated via HTTP PUT requests.
Attack Lifecycle and Monetization
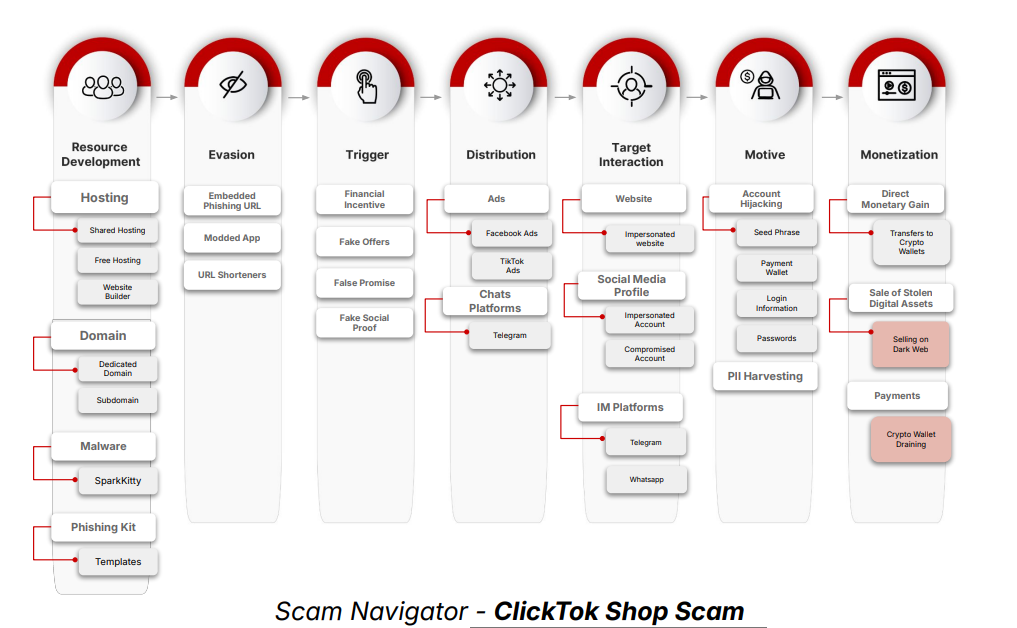
CTM360’s Scam Navigator framework outlines a systematic approach to these scams, beginning with resource development (fake domains, ads, and malware creation), moving through distribution via social platforms and messaging apps, and culminating in direct financial theft. Scammers monetize through multiple channels:
- Credential Harvesting: Phishing pages steal TikTok login details for resale or future fraud.
- Fake Storefront Transactions: Victims transfer cryptocurrency for products or commissions that never arrive.
- Persistent Access: Infected devices are co-opted into further fraud or used for siphoning digital assets.
Implications and Takeaways
The rapid evolution of ClickTok, combined with the technical sophistication of SparkKitty, highlights growing risks to social commerce participants worldwide.
Key defenses include heightened user vigilance, use of official app stores, and robust endpoint security measures, especially as threat actors increasingly weaponize brand trust and exploit platform ecosystems at scale.
As TikTok continues its expansion, both consumers and businesses are urged to scrutinize unexpected offers and remain alert to the tactics of these evolving scam operations.