Cybersecurity researchers at Horizon3.ai have uncovered two critical zero-day vulnerabilities in Xerox FreeFlow Core, a widely used print orchestration platform deployed across commercial print shops, universities, and government agencies.
The vulnerabilities, designated CVE-2025-8355 and CVE-2025-8356, enable unauthenticated remote attackers to achieve complete system compromise through XML External Entity (XXE) injection and path traversal attacks.
Discovery Through Customer Support Investigation
The discovery of these vulnerabilities began with an unusual support ticket from a Horizon3.ai customer who reported what appeared to be a false positive detection.
The customer’s NodeZero security platform had identified an XXE injection vulnerability on a host that supposedly didn’t contain the targeted software.
However, the system was receiving clear callbacks indicating successful exploitation, prompting researchers to investigate further.
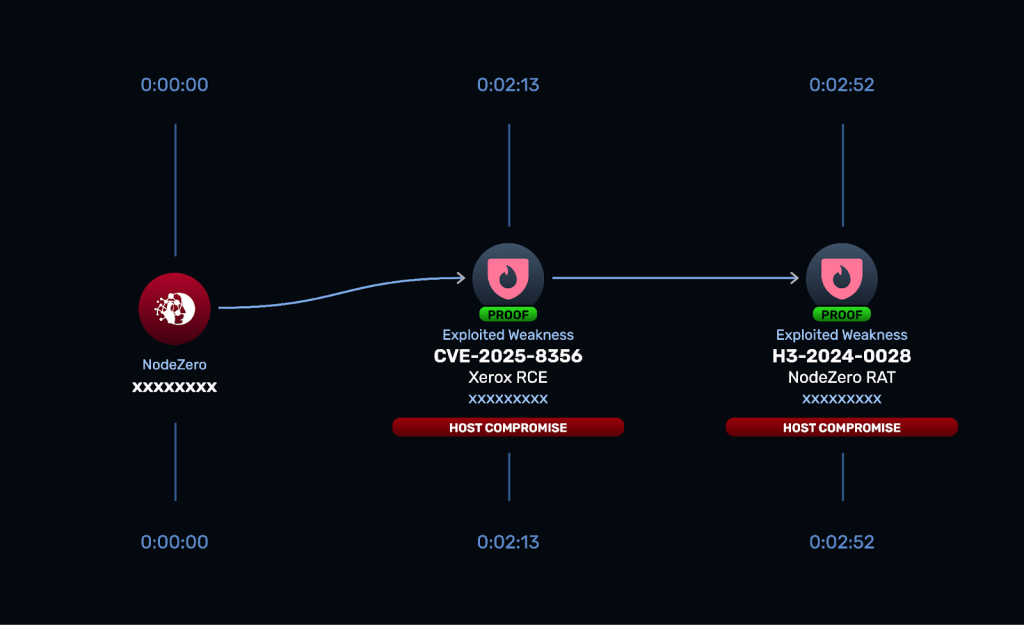
Upon deeper analysis, researchers identified that the vulnerable component was Xerox FreeFlow Core’s JMF Client service, which operates on port 4004 and handles Job Message Format messages for print job management.
The service’s XML parsing utility failed to properly sanitize or limit XML External Entities, creating the XXE injection vulnerability tracked as CVE-2025-8355.
This flaw allows attackers to perform server-side request forgery attacks against vulnerable systems.
Severe Path Traversal Enables Remote Code Execution
During their investigation of the XML parsing routines, researchers discovered a second, more critical vulnerability in the file processing mechanism.
CVE-2025-8356 represents a path traversal vulnerability that allows attackers to upload malicious files to publicly accessible locations on the server.
The researchers demonstrated that this vulnerability could be exploited to place webshells in accessible directories, providing full remote code execution capabilities.
The combination of these vulnerabilities is particularly concerning given the sensitive nature of FreeFlow Core deployments.
These systems typically handle pre-publication marketing materials and require relatively open network access for their print orchestration functions, making them attractive targets for cybercriminals.
Xerox has responded promptly to the disclosure, releasing patches for both vulnerabilities in FreeFlow Core version 8.0.5 on August 8, 2025.
The responsible disclosure process began in June 2025, with Horizon3.ai working closely with Xerox’s security team throughout the summer to develop and test appropriate fixes.
Security experts strongly recommend that all FreeFlow Core users upgrade to version 8.0.5 immediately to protect against potential exploitation.
The vulnerabilities highlight the ongoing security challenges facing enterprise print infrastructure, an often-overlooked component of organizational IT security that can provide significant attack vectors for malicious actors seeking to infiltrate corporate networks and access sensitive pre-publication content.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates