Cybercriminals are increasingly leveraging subject customization tactics to deliver malware through highly personalized phishing campaigns, according to new threat intelligence analysis covering Q3 2023 to Q3 2024.
This sophisticated approach involves crafting email subjects, attachment names, and embedded links with recipient-specific information to create an illusion of authenticity and urgency.
Travel and Finance Themes Dominate Customized Attacks
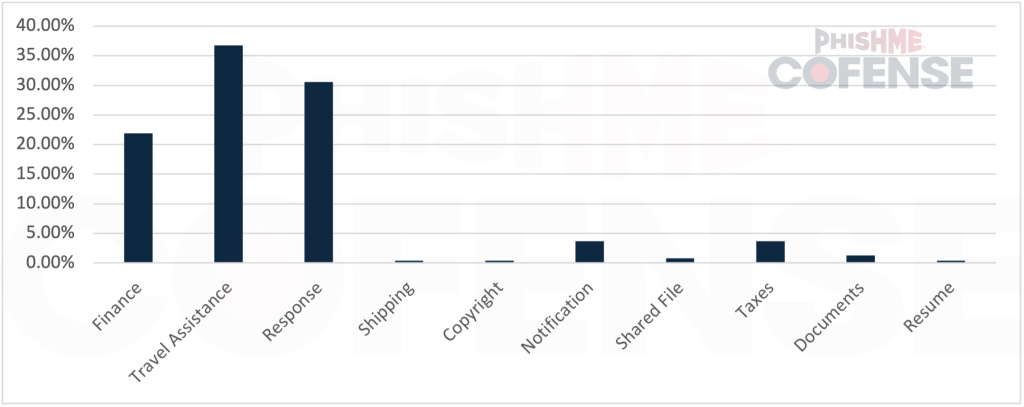
Travel Assistance emerged as the most prevalent theme, accounting for 36.78% of malware delivery emails requiring subject redaction due to personally identifiable information (PII).
These campaigns predominantly deliver Vidar Stealer, an information-stealing malware capable of harvesting login credentials, banking data, cryptocurrency wallet information, and browser cookies.
The theme’s effectiveness stems from recipients’ natural expectation of personalized travel-related communications.
Response-themed emails followed closely at 30.58%, typically masquerading as replies to equipment orders or meeting cancellations.
These campaigns frequently deploy PikaBot, a sophisticated malware family that emerged prominently in 2023, featuring advanced sandbox evasion techniques and secondary payload delivery capabilities.
Finance-themed attacks represented 21.90% of customized campaigns, with threat actors exploiting the natural inclusion of PII in financial communications.
These campaigns showed a notable preference for jRAT, a cross-platform Remote Access Trojan written in Java that enables attackers to operate across multiple operating systems.
Malware-Specific Customization Patterns
Intelligence analysis revealed a strong correlation between specific malware families and customization tactics. When jRAT or Remcos RAT appeared in campaigns with customized download file names, the emails were almost exclusively Finance-themed.
jRAT accounted for 20% of emails containing PII in downloaded file names, while Remcos RAT represented 26.7% of such campaigns.
Remcos RAT campaigns typically employed password-protected archives hosted on file-sharing platforms to bypass Secure Email Gateways. The malware subsequently executes keyloggers, exfiltrates sensitive files, and deploys additional malicious payloads.
Escalating Ransomware Risk
The implications extend beyond initial compromise, as Remote Access Trojans and information stealers provide cybercriminals with credentials and system access that can be brokered to ransomware operators.
Recent industry analysis indicates that the majority of Q2 2025 ransomware incidents originated from either remote access compromise or phishing attacks.
While international law enforcement continues disrupting ransomware groups, the brokered access model remains resilient.
Tax and Notification themes, though representing smaller percentages at 3.72% each, demonstrate threat actors’ willingness to exploit seasonal opportunities and routine business communications.
The research underscores how personalization transforms generic phishing attempts into targeted social engineering campaigns, significantly increasing the likelihood of successful infections and subsequent organizational compromise.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates