Cybersecurity researchers have identified PhantomCard, a sophisticated Android NFC-based Trojan specifically targeting Brazilian banking customers with potential for global expansion.
This malicious software represents the latest evolution in NFC relay attacks, following the discovery of Ghost Tap and NFSkate malware families that have transformed the mobile threat landscape since early 2024.
The emergence of PhantomCard underscores the growing demand among cybercriminals for tools capable of NFC relay fraud, marking a significant escalation in contactless payment security threats.
Technical Operations and Distribution Methods
PhantomCard operates by establishing a relay channel between victims’ physical payment cards and Point-of-Sale (POS) terminals or ATMs controlled by fraudsters.
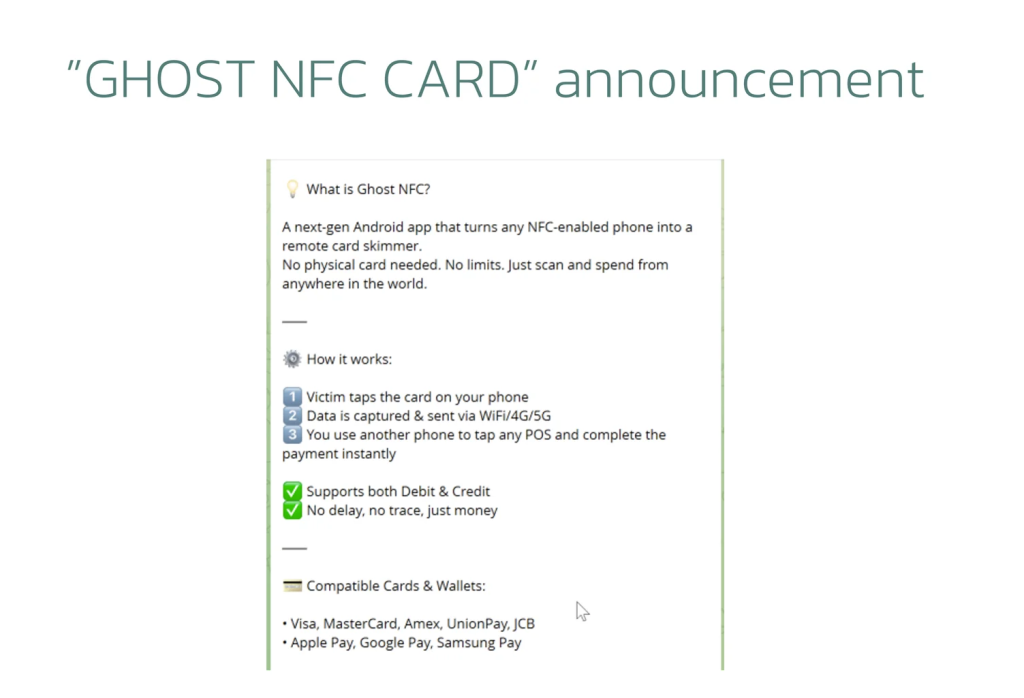
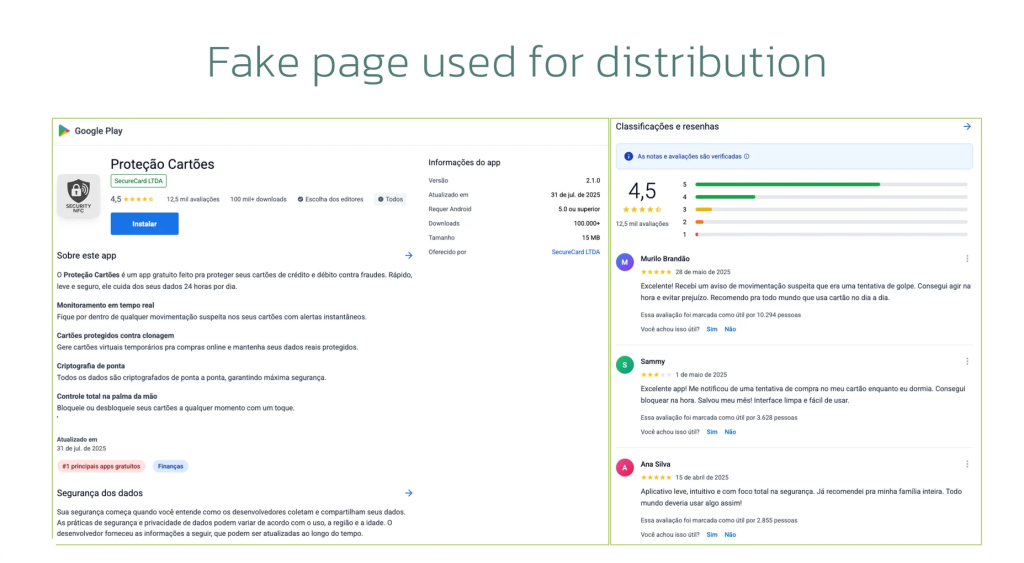
The malware masquerades as “Proteção Cartões” (Card Protection) applications distributed through convincing fake Google Play pages, complete with fabricated positive reviews.
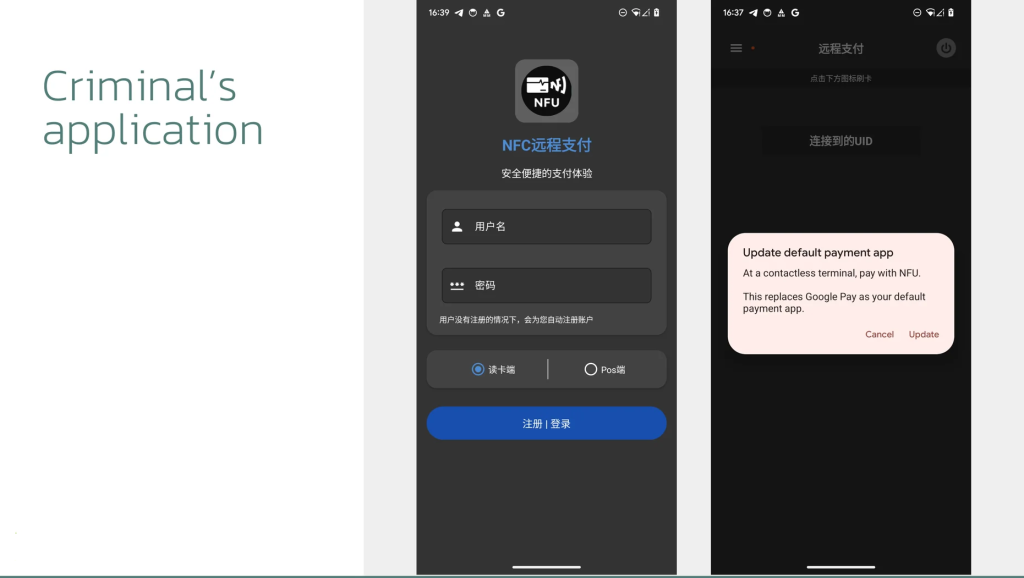
Once installed, the Trojan requires no additional permissions and immediately prompts users to tap their cards against their device for “verification purposes.”
The malware specifically targets EMV cards using the ISO-DEP (ISO 14443-4) standard, leveraging the “scuba_smartcards” library to parse communication data.
When an NFC tag is detected, PhantomCard sends APDU commands to select the Payment System Environment directory, specifically targeting the “2PAY.SYS.DDF01” directory used in EMV payment systems.
This technical approach enables criminals to remotely use victims’ cards, as if they were physically present, thereby bypassing traditional security measures and requesting PIN codes through a malicious interface.
Criminal Networks and Global Expansion Risks
Investigation reveals that PhantomCard originates from “NFU Pay,” a Chinese Malware-as-a-Service platform, highlighting the internationalization of cybercriminal operations.
The threat actor “Go1ano developer,” operating as a regional reseller in Brazil, purchased and customized this malware for local distribution.
This reseller model represents a concerning trend where local distributors expand global malware reach by overcoming language and cultural barriers that previously limited international cyber threats.
The malware’s Command-and-Control server contains endpoints specifically referencing Brazil (“/baxi/b” – “baxi” meaning Brazil in Chinese), indicating deliberate geographic targeting.
However, the underlying “NFU Pay” service’s customizability poses significant global risks, as similar region-tailored versions could emerge worldwide.
The “Go1ano developer” also promotes other malware families, including BTMOB and GhostSpy, establishing a pattern of serial reselling that amplifies the threat landscape for financial institutions.
This development continues the alarming trend identified with Ghost Tap attacks, where cybercriminals increasingly leverage NFC relay techniques for fraudulent cash-out schemes.
Financial organizations face unprecedented challenges in detecting these attacks, as transactions appear legitimate while originating from victims’ actual cards with proper PIN authentication, making traditional monitoring systems inadequate against this evolving threat vector.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates