Cybersecurity researchers at Zscaler ThreatLabz have uncovered a sophisticated supply chain attack targeting Python developers through a malicious package that leverages DLL sideloading and Windows registry manipulation for persistent system compromise.
The attack, discovered on July 22, 2025, demonstrates how threat actors are weaponizing legitimate-looking Python packages to establish long-term access to victim systems.
Multi-Stage Attack Chain Through PyPI Packages
The attack begins with a seemingly benign Python package named termncolor, which appears to provide terminal color utilities for developers.
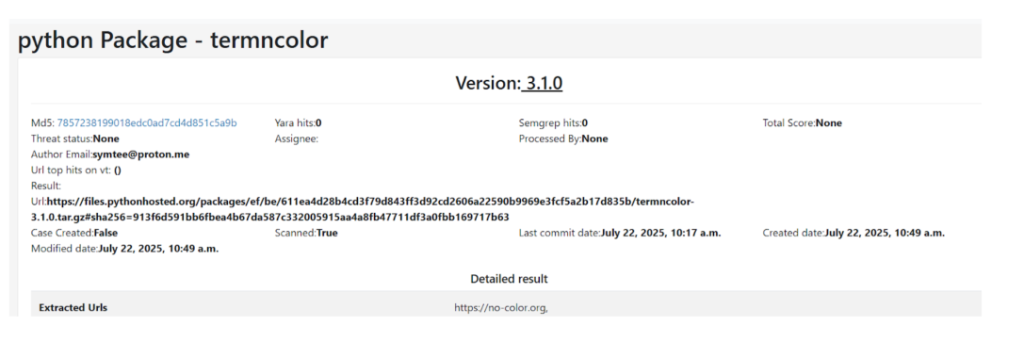
termncolorHowever, the package imports a malicious dependency called colorinal that serves as the initial infection vector. Upon installation, the malware executes a file named unicode.py that uses Python’s ctypes library to load a malicious DLL called terminate.dll.
The malware employs AES encryption in CBC mode to decrypt its payload, using the UTF-8-encoded key “xterminalunicode” provided by the Python script.
Once decrypted, the payload drops two critical files into the victim’s %LOCALAPPDATA%\vcpacket directory: a legitimate signed executable vcpktsvr.exe and a malicious component libcef.dll.
This approach enables DLL sideloading, where the legitimate executable unknowingly loads the malicious DLL, allowing the malware to execute with the appearance of legitimacy.
Registry Persistence and Command-and-Control Operations
To maintain persistence across system reboots, the malware creates a registry entry named pkt-update under the Windows Run key (HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run).
This ensures automatic execution of vcpktsvr.exe at system startup, establishing a persistent foothold on compromised systems.
The second-stage payload, executed through libcef.dll, conducts comprehensive system reconnaissance, collecting computer names, usernames, and operating system versions.
The malware then communicates with its command-and-control server using HTTPS traffic disguised as legitimate Zulip team messaging platform communications, making detection significantly more challenging for traditional security tools.

Cross-Platform Threat with Custom Obfuscation
The attack extends beyond Windows systems, with researchers identifying a Linux variant using terminate.so files for Unix-like operating systems.
The malware employs custom API hashing algorithms to obfuscate DLL and API names, utilizing ASCII values, multiplication, and bitwise operations to evade detection mechanisms.
Analysis of the threat actor’s infrastructure reveals the use of the email address [email protected] and user ID 937950 on the Zulip platform.
The C2 infrastructure showed significant activity from mid-July 2025, with over 90,000 messages exchanged before going offline.
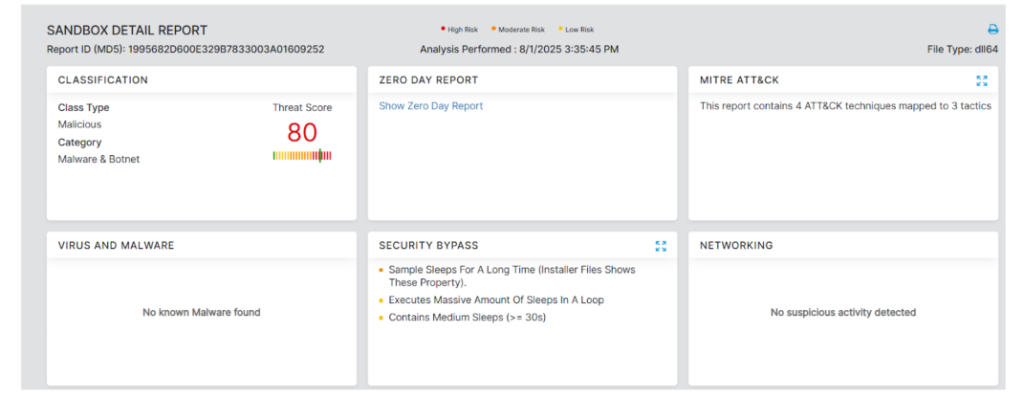
Both malicious packages have been removed from the Python Package Index (PyPI), but the attack highlights the ongoing risks of supply chain compromises in open-source ecosystems.
Organizations should implement comprehensive package scanning and monitoring solutions to detect such threats before they can establish persistence on critical systems.
Indicators Of Compromise (IOCs)
| MD5 | Name |
|---|---|
| 381022e5fd0cede7146f9922e1ed30a3 | libcef.dll |
| 9267d9a72207df3217014f206ba18560 | vcpktsvr.exe |
| 1995682d600e329b7833003a01609252 | terminate.dll |
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates