A cybersecurity researcher has disclosed multiple high-severity vulnerabilities across McDonald’s digital ecosystem, ranging from client-side validation bypasses to unauthorized access to executive systems.
The vulnerabilities, which affected everything from the mobile app to internal corporate platforms, were discovered through extensive reconnaissance and required unconventional reporting methods to reach McDonald’s security team.
Mobile Application and Rewards System Compromise
The initial discovery began with the McDonald’s mobile application, where the researcher identified a client-side validation vulnerability in the rewards system.
The application failed to perform server-side verification of reward point balances, allowing users to potentially claim free food items regardless of their actual point totals.
This fundamental authentication bypass highlighted inadequate input validation controls within the mobile payment infrastructure.
The researcher’s attempts to report this vulnerability through conventional channels proved unsuccessful, ultimately requiring direct contact with software engineering personnel to achieve remediation.
Design Hub Authentication Failures
McDonald’s Feel-Good Design Hub, serving brand assets to teams across 120 countries, initially employed client-side password protection—a critical security anti-pattern.
After the researcher’s disclosure, McDonald’s implemented a multi-tier authentication system with separate login paths for employees and external partners.
However, the implementation contained a severe authorization bypass.
By modifying the URL endpoint from /login to /registerUnauthorized users could create accounts and access confidential marketing materials.
The registration process exposed system architecture through verbose error messages, and successful registrations resulted in plaintext password transmission via email—a violation of fundamental password security principles.

JavaScript-Exposed API Credentials
Static analysis of the Design Hub’s client-side code revealed hardcoded Magicbell API keys and secrets.
These credentials enabled unauthorized access to user enumeration functions and notification systems, creating potential vectors for social engineering attacks using McDonald’s branding infrastructure.
Employee Data Exposure Through Search Systems
The researcher discovered exposed Algolia search configurations containing personally identifiable information (PII) of users requesting system access.
This data exposure included names, email addresses, and access request details, creating significant privacy compliance risks.
Privilege Escalation in Corporate Systems
Perhaps most concerning was the discovery that basic crew member credentials could access executive-level systems through OAuth misconfigurations.
The TRT (trt.mcd.com) platform, intended for corporate use, allowed crew members to search for any McDonald’s employee globally, including C-suite executives, and access associated email addresses.
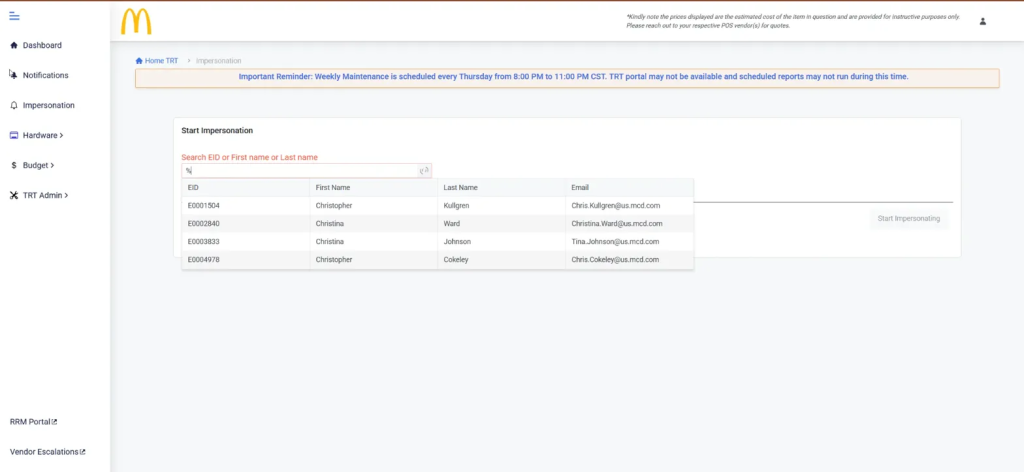
The system included an “impersonation” feature accessible to unauthorized personnel, representing a severe privilege escalation vulnerability.
Administrative Panel Security Failures
The GRS (Global Restaurant Standards) panel contained unauthenticated administrative endpoints, allowing arbitrary modification of HTML content without proper access controls.
This represented a complete absence of authentication mechanisms for critical business functions.
| System | Vulnerability Type | Impact Level | Status |
|---|---|---|---|
| Mobile App | Client-side validation bypass | Medium | Fixed |
| Design Hub | Authentication bypass | High | Partially Fixed |
| JavaScript APIs | Credential exposure | High | Fixed |
| Algolia Search | Data exposure | Medium | Reported |
| TRT Platform | Privilege escalation | Critical | Unknown |
| GRS Panel | Missing authentication | Critical | Unknown |
The researcher encountered significant obstacles in vulnerability disclosure, as McDonald’s had removed their security.txt file shortly after implementation.
This forced unconventional reporting methods, including cold-calling corporate headquarters and leveraging LinkedIn reconnaissance to identify security personnel.
McDonald’s addressed several reported vulnerabilities but terminated an employee who assisted in the research for “security concerns from corporate,” raising questions about their approach to security research collaboration.
Recommendations for Enterprise Security
This case study highlights the crucial importance of established vulnerability disclosure programs and well-maintained security contact channels.
The researcher’s findings underscore the importance of server-side validation, proper authentication mechanisms, and secure credential management in large-scale digital infrastructures.
McDonald’s has since implemented fixes for the most critical vulnerabilities, though some systems may remain exposed.
The incident highlights the ongoing challenges in coordinating responsible disclosure with organizations lacking formal security research engagement protocols.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates