The latest analysis of KorPlug, a persistent malware family tied to espionage operations, reveals how its operators deploy advanced compiler-level obfuscation to conceal second-stage functionality.
Building on earlier research that documented DLL side-loading as the initial entry point, this installment focuses on the methods used to disguise execution and how researchers reconstructed the underlying behavior.
Unconventional Execution Flow
Unlike conventional malicious DLLs that rely on the Windows loader, the examined sample (SHA-256 hash b6b239fe0974cf09fe8ee9bc5d0502174836a79c53adccdbb1adeb1f15c6845c) redirects execution via the EnumSystemGeoID API.
This shellcode-style approach allows the malware to bypass security mechanisms tied to standard DLL entry points, delivering control directly to the custom Initialize function.
Analysts quickly discovered that this function’s structure bore the hallmarks of O-LLVM, an obfuscation framework derived from the LLVM compiler infrastructure.
O-LLVM employs compiler-level transformations designed to resist analysis. Control flow flattening conceals decision-making inside dispatcher-driven state machines, bogus branches lead disassemblers astray, and instruction substitution replaces straightforward code with convoluted constructions.
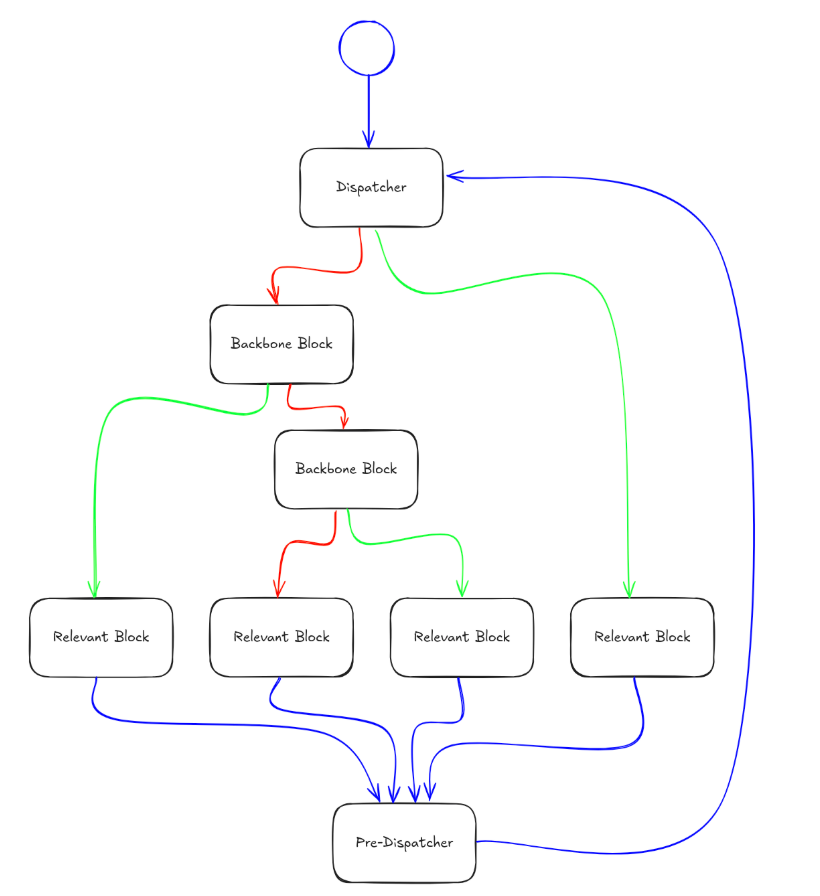
The result is a control flow graph that appears artificially complex, masking the actual payload logic within a maze of dispatcher and backbone components.
Mapping the Control Flow Graph
To navigate this obfuscation, researchers used the angr binary analysis framework to classify the function’s basic blocks systematically.
Pre-dispatcher and dispatcher components controlled the manipulation of a central state variable, which governed execution transitions.
Backbone blocks enforced conditional jumps based on this variable, while the relevant blocks operated as the actual containers of malicious functionality, including persistence tasks and command execution logic.
A final set of tail blocks contributed nothing to functionality, serving only to expand the graph’s complexity.
Once mapped, analysts were able to deconstruct the obfuscation. By enumerating state assignments within relevant blocks and correlating them with conditional checks in backbone components, they reconstructed the intended execution chain.
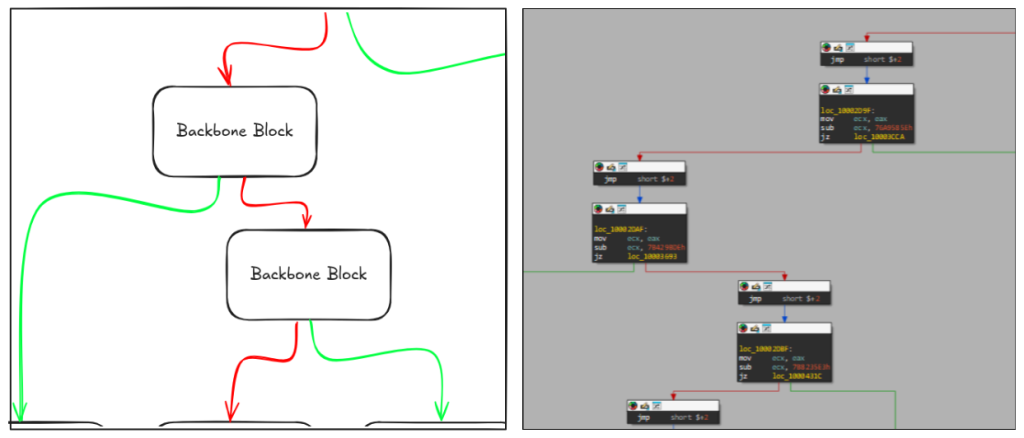
Binary patching then replaced dispatcher-driven indirect jumps with direct transitions, removed redundant blocks, and restored a simplified flow that revealed the malware’s actual behavior.
Indicators and Broader Implications
The examined DLL, with a file size of 624 kilobytes, underscores how adversaries increasingly rely on compiler-level tools to shield malware. KorPlug’s approach not only complicates static and dynamic analysis but also sidesteps heuristics that assume standardized Windows DLL loading behavior.
The methodology used in this investigation highlights that automation-driven workflows for control flow graph reconstruction are now essential for malware analysis.
While this sample required manual adjustment to supplement existing tools like MODeflattener, the approach demonstrates how obfuscation can be systematically unraveled.
As malware families continue to evolve, defenders must adapt their reverse engineering strategies to keep pace with adversaries skilled in compiler-assisted concealment.
IOCs
| SHA-256 | Description |
| b6b239fe0974cf09fe8ee9bc5d0502174836a79c53adccdbb1adeb1f15c6845c | The content of the analyzed sample, identified by its SHA-256 hash |
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates