In March 2025, Google’s Threat Intelligence Group (GTIG) uncovered a sophisticated cyber espionage campaign attributed to the PRC-linked threat actor UNC6384, also associated with TEMP.Hex (Mustang Panda).
The campaign primarily targeted diplomats and government sectors in Southeast Asia, while also affecting global organizations. According to GTIG, this operation aligns with the strategic cyber intelligence objectives of the People’s Republic of China (PRC).
Advanced Delivery Tactics – Using Captive Portal Hijacks and AitM
The campaign weaponized legitimate browser functionality designed for captive portal detection. Chrome periodically queries a hardcoded domain (www.gstatic.com/generate_204) to verify connectivity.
UNC6384 hijacked this mechanism through adversary-in-the-middle (AitM) attacks on compromised edge devices, redirecting users to attacker-controlled infrastructure.
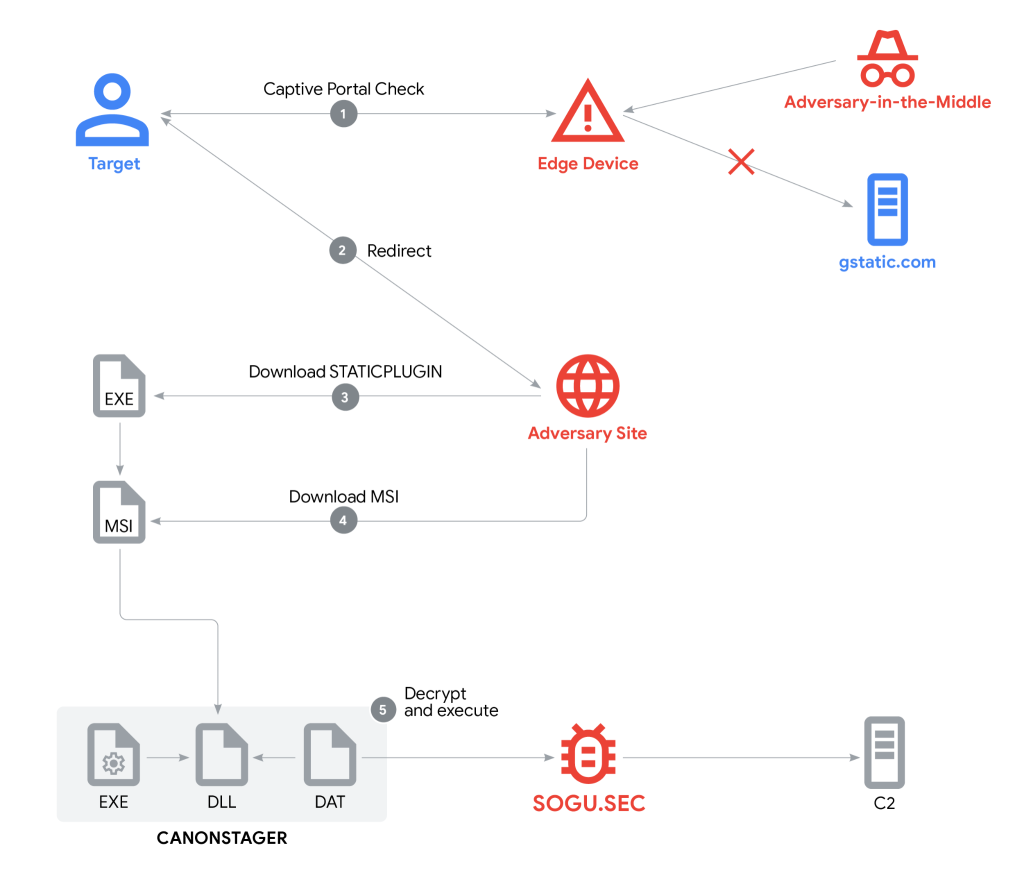
Victims were prompted with a convincing fake update page using HTTPS certificates from Let’s Encrypt to download a malware dropper disguised as an “Adobe Plugin update.”
The executable, tracked as STATICPLUGIN, was seamlessly delivered under the guise of a digitally signed installer. GTIG identified that the signer was Chengdu Nuoxin Times Technology Co., Ltd., raising questions about whether the signing material was stolen or willingly misused.
Multi-Stage Chain Leading to SOGU.SEC Backdoor
Upon execution, STATICPLUGIN masqueraded as a Visual C++ Redistributable installer, leveraging Windows Installer COM objects to download a second-stage MSI package. This package contained three files:
cnmpaui.exe(Canon Printer Assistant Tool)cnmpaui.dll(CANONSTAGER launcher)cnmplog.dat(RC4-encrypted SOGU.SEC)
Through DLL side-loading, CANONSTAGER decrypted and deployed SOGU.SEC entirely in-memory, employing evasive techniques such as Thread Local Storage (TLS) arrays, window procedure callbacks, and Windows message queues.

This indirect execution strategy allowed the malware to evade behavioral detection engines by embedding execution flows inside everyday Windows control routines.
The deployed SOGU.SEC backdoor provided UNC6384 with capabilities to exfiltrate files, execute remote commands, and maintain persistent command-and-control via HTTPS to 166.88.2[.]90.
Broader PRC-Nexus Espionage Trend
UNC6384’s tactics reflect a broader PRC tendency to use digitally signed malware, stealthy loaders, and social engineering for strategic espionage.
GTIG noted overlaps between this campaign and previous PRC-linked operations, particularly in the use of signed binaries, DLL side-loading, and targeting government sectors across Southeast Asia.
Google has since blocked malicious domains, revoked abused certificates, and notified all affected Workspace and Gmail users through its government-backed attacker alerts.
Security teams are urged to enable Enhanced Safe Browsing in Chrome, apply strict certificate monitoring, and hunt for related IOCs via Google SecOps or open-source intelligence sources like VirusTotal.
As UNC6384 demonstrates an evolving arsenal blending legitimate digital signatures, network-level hijacks, and stealthy loaders, defenders are cautioned that conventional trust anchors like HTTPS and code signing are no longer reliable indicators of file legitimacy.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates