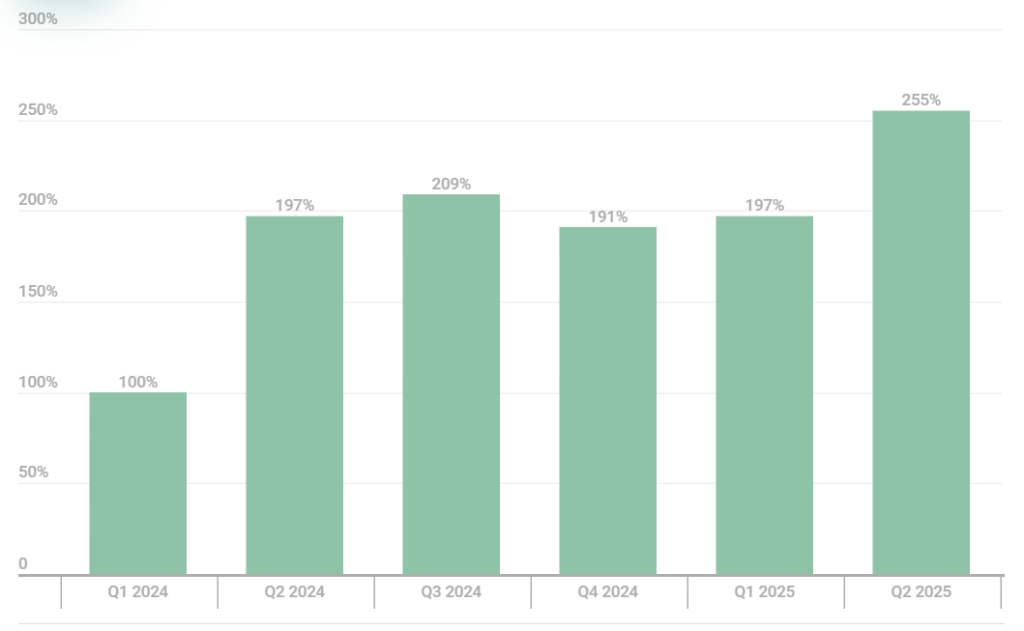
Cybersecurity experts are sounding the alarm after a surge of vulnerabilities was registered in Q2 2025, threatening the integrity of every central computer subsystem from UEFI firmware to operating systems and web browsers.
This spike in security flaws underscores how threat actors continue to exploit weaknesses for real-world attacks, compromising user systems worldwide.
Windows and Linux Under Fire
Attackers predominantly targeted Microsoft Office products plagued with unpatched vulnerabilities, repeatedly exploiting remote code execution risks in the aging Equation Editor component, specifically CVE-2018-0802 and CVE-2017-11882 alongside CVE-2017-0199 in WordPad, enabling system control through malicious documents.
WinRAR, too, came under fire, with CVE-2023-38831 and the newly registered CVE-2025-24071 allowing credential theft and arbitrary file operations while exploiting improper archive handling.
Additionally, CVE-2024-35250 in the ks.sys driver enabled attackers to execute arbitrary code, intensifying post-compromise activities.
On Linux systems, exploits for CVE-2022-0847 (“Dirty Pipe”) were widespread, allowing for privilege escalation and control over applications.
Legacy issues, such as CVE-2019-13272 and heap overflow vulnerabilities like CVE-2021-22555, threatened kernel subsystems, allowing attackers to exploit memory manipulation primitives for persistence and elevated privileges.
Data reveal that the number of users encountering exploits continues to rise, especially as more devices run Linux.
Inside the Hack: C2 Frameworks and Advanced Persistent Threats
Sophisticated malware campaigns in the first half of 2025 leveraged popular command-and-control (C2) frameworks—Sliver, Metasploit, Havoc, and Brute Ratel C4.
These tools provide attackers with ready-made exploit modules supporting reconnaissance, command execution, and persistence capabilities. Metasploit’s default library alone streamlines initial access, while other frameworks require tailored modifications to maximize the damage potential.
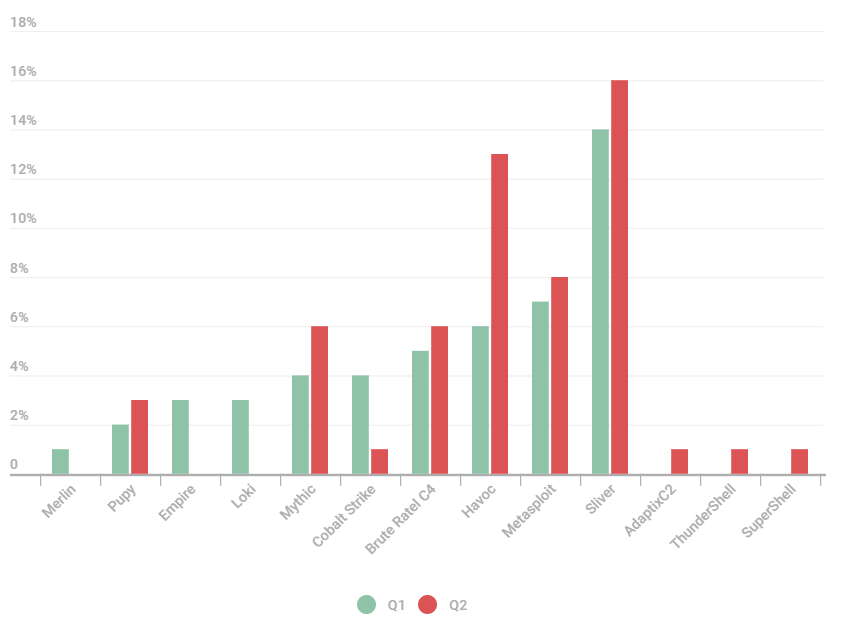
Highlighting the technical depth of recent APT attacks, researchers identified a crop of vulnerabilities weaponized by C2 agents, including SAP’s Visual Composer Metadata Uploader (CVE-2025-31324), ConnectWise ScreenConnect (CVE-2024-1709), and vulnerabilities in the CHAOS remote administration tool (CVE-2024-31839, CVE-2024-30850).
Notably, CVE-2025-33053 exploited improper directory handling in Windows, underscoring the reliance of attackers on both newly discovered and persistent legacy bugs.
Conclusion: Defending Against an Evolving Threat Landscape
The relentless growth in newly registered security flaws underscores the urgent need for enterprises and users to install updates and deploy robust endpoint protection solutions rapidly.
Organizations are advised to automate patch management and monitor network perimeters continuously to detect threats, including C2 framework agents.
Proactive measures, including vulnerability management platforms that can simulate attack scenarios and automate incident response, have become necessary in a world where the boundary between novel and familiar exploits rapidly blurs.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates