Cybersecurity researchers have uncovered a sophisticated campaign targeting the upcoming FIFA tournaments, with threat actors registering hundreds of malicious domains to exploit the global excitement surrounding the 2025 FIFA Club World Cup and the 2026 FIFA World Cup.
PreCrime Labs, the threat research division of BforeAI, identified 498 suspicious domains containing FIFA, football, and World Cup-related brand terms, revealing cybercriminals’ strategic preparation for large-scale fraud operations.
The investigation exposes a troubling trend: attackers are employing long-term domain aging strategies, registering domains up to two years in advance to avoid detection systems.
Researchers discovered domains already registered for FIFA tournaments scheduled for 2030 and 2034, demonstrating the sophisticated planning behind these cybercriminal operations.
Strategic Domain Registration Patterns
The analysis reveals that cybercriminals concentrated their efforts during a five-day window from August 8 to 12, 2025, when approximately 299 domains were registered.
The domains exploit multiple attack vectors, including 56 merchandise stores selling counterfeit goods, 55 fake streaming platforms promising free match access, and 32 betting sites operating in regulatory gray areas.
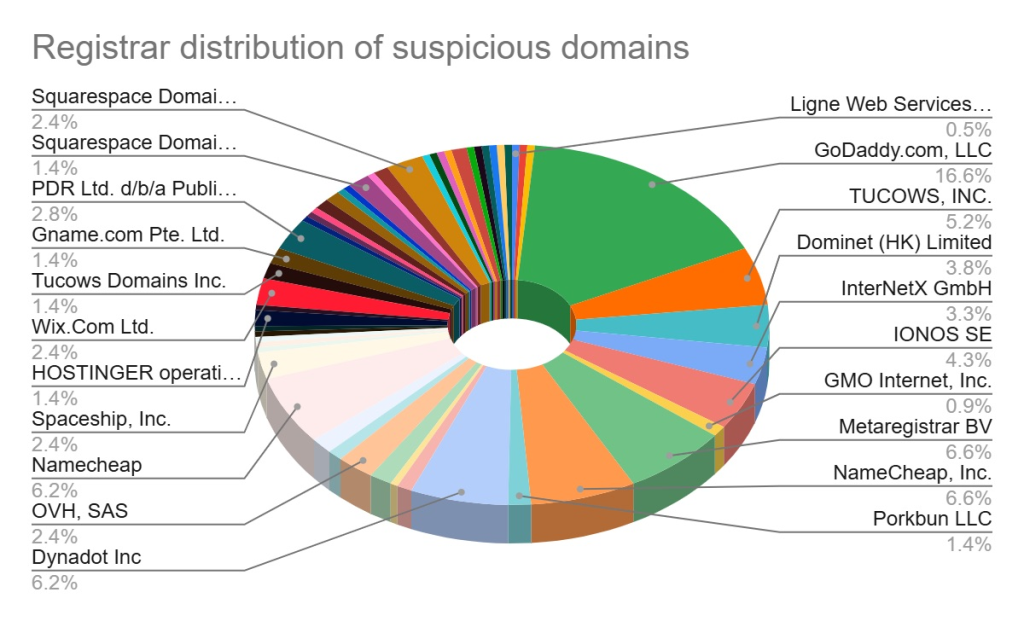
GoDaddy, Namecheap, and Gname emerged as the top registrars used by threat actors, with .com domains comprising 58.9% of registrations.
The prevalence of low-cost top-level domains, such as .online, .xyz, and .shop, indicates disposable infrastructure tactics designed to maximize reach while minimizing investment.
Geographic targeting shows sophisticated market analysis, with 23 domains specifically referencing U.S. host cities, including Dallas, Atlanta, Kansas City, and Philadelphia. Examples include “fifawcdallas[.]com” and “kansascityunitycup2026[.]com,” designed to target local fans and travelers.
Technical Sophistication and Multilingual Threats
The campaign employs advanced social engineering techniques, including Mandarin Chinese-language sites that target Asian audiences with fake streaming services and cryptocurrency scams.
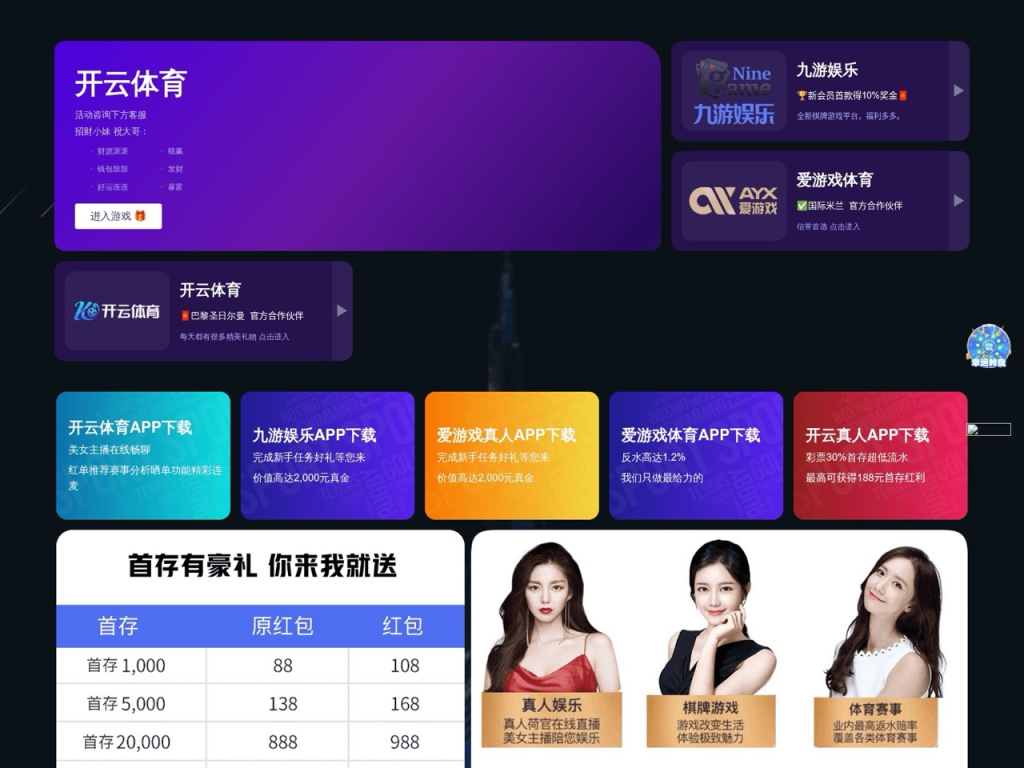
One notable domain promoted a fraudulent “FIFA coin” initial coin offering (ICO), displaying fabricated statistics that claimed $18 million had been staked across 421,000 wallets.
Typosquatting remains a primary tactic, with domains like “fifaworldcupstadiucom” (missing the ‘.com’) designed to capture mistyped traffic. Credential phishing attempts utilize domains such as “fifaworldcup-login[.]com” and “fifaworldcup-register[.]com” to harvest user authentication data.
Emerging Threat Landscape
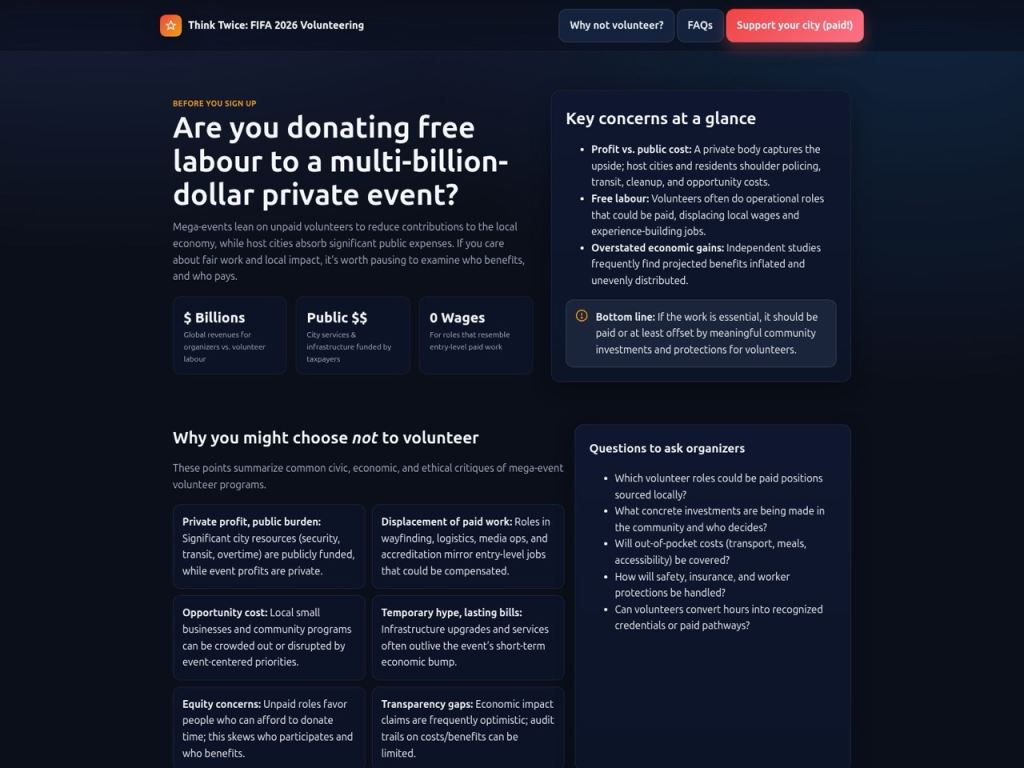
The research identifies novel attack vectors, including fake business directories targeting electric vehicle charging stations for World Cup travelers, and influence operations disguised as social activism criticizing FIFA’s volunteer programs.
These sophisticated campaigns blend legitimate-looking content with malicious intent, making detection more challenging.
Security experts recommend proactive monitoring of event-specific keywords, which combine city names with tournament years, as well as the implementation of pattern-based domain detection systems and enhanced user education about official FIFA channels.
As the 2026 World Cup approaches, organizations can expect intensified registration waves and increasingly sophisticated social engineering attacks that leverage tournament excitement to bypass traditional security measures.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates