Security researchers at Stripe’s Operations, Legal, and Trust Security Operations Center (OLT SOC) have uncovered a sophisticated spearphishing campaign specifically targeting senior executives and C-suite leadership across multiple industries.
The attack leverages convincing Microsoft OneDrive document-sharing notifications to steal corporate credentials through highly personalized phishing emails.
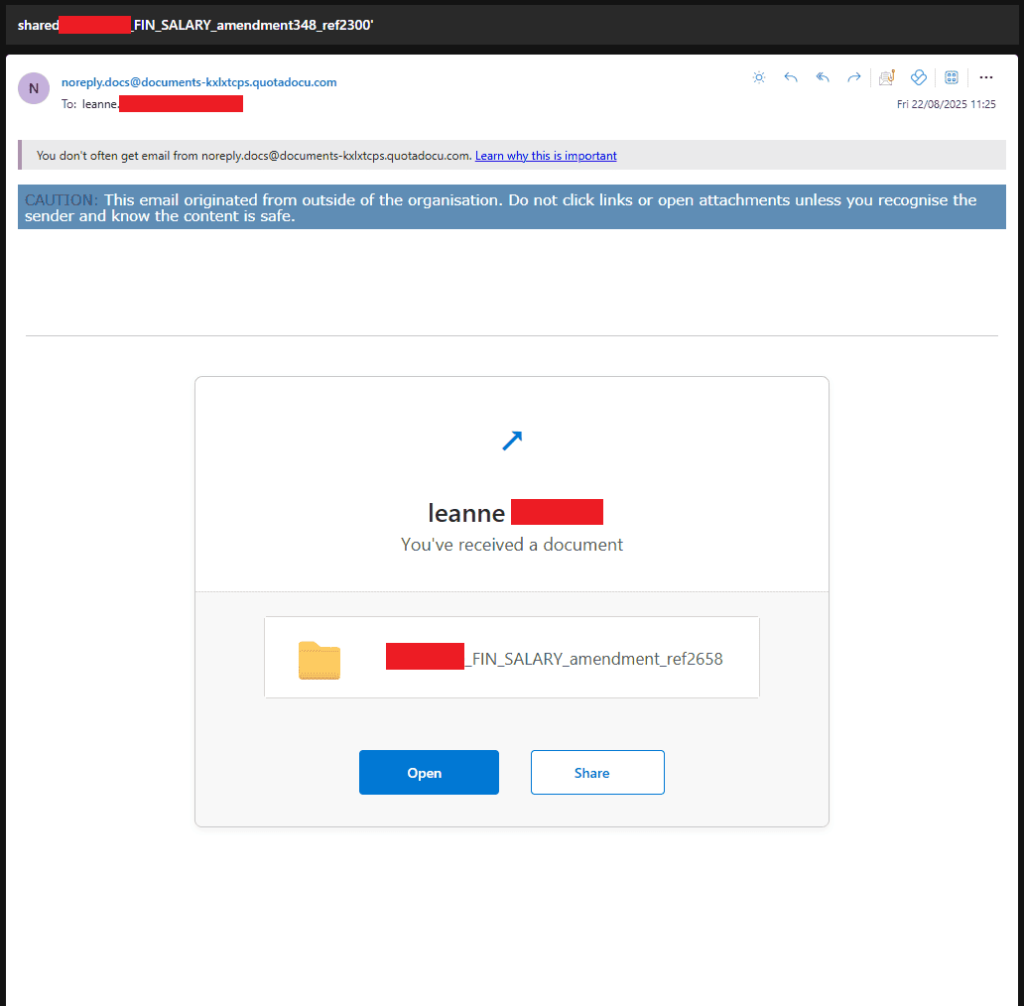
The campaign employs deceptive subject lines such as “Salary amendment” and “FIN_SALARY,” impersonating internal HR communications to establish credibility with high-value targets.
Recipients receive emails that appear to be legitimate OneDrive document-sharing notifications, complete with personalized company details and recipient names to enhance authenticity.
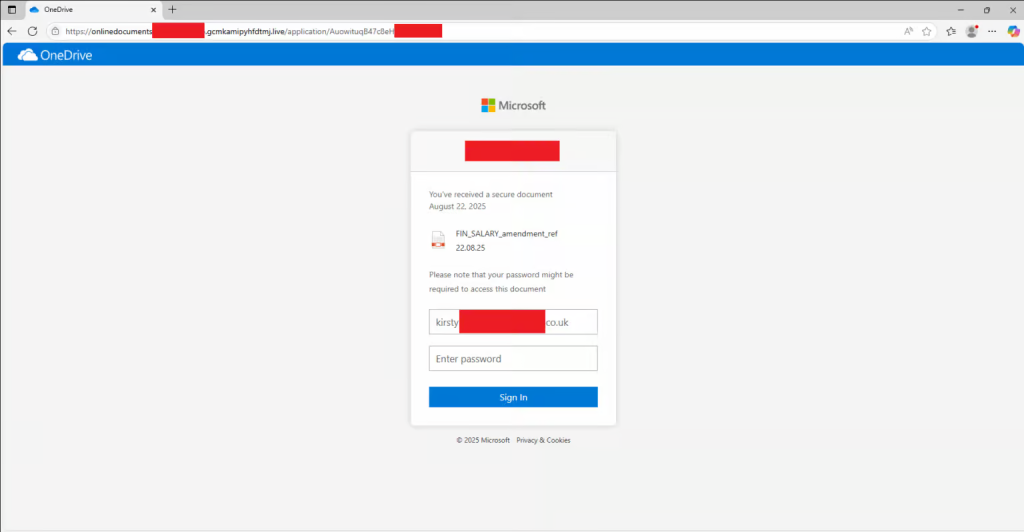
When victims click the malicious links, they are redirected to meticulously crafted credential harvesting pages that closely mimic Microsoft Office and OneDrive login interfaces.
These phishing sites are designed to capture corporate usernames and passwords, potentially granting attackers access to sensitive organizational systems and data.
Advanced Evasion Techniques
The threat actors behind this campaign demonstrate considerable technical sophistication in their approach to evading detection systems.
They utilize Amazon Simple Email Service (SES) infrastructure for email delivery while rotating between approximately 80 different domains and subdomains to avoid security filters and maintain operational persistence.
A particularly notable anti-detection technique involves the use of obfuscated button text that changes its appearance based on the email client’s display settings. When viewed in light mode, buttons appear as standard “Open” and “Share” labels.
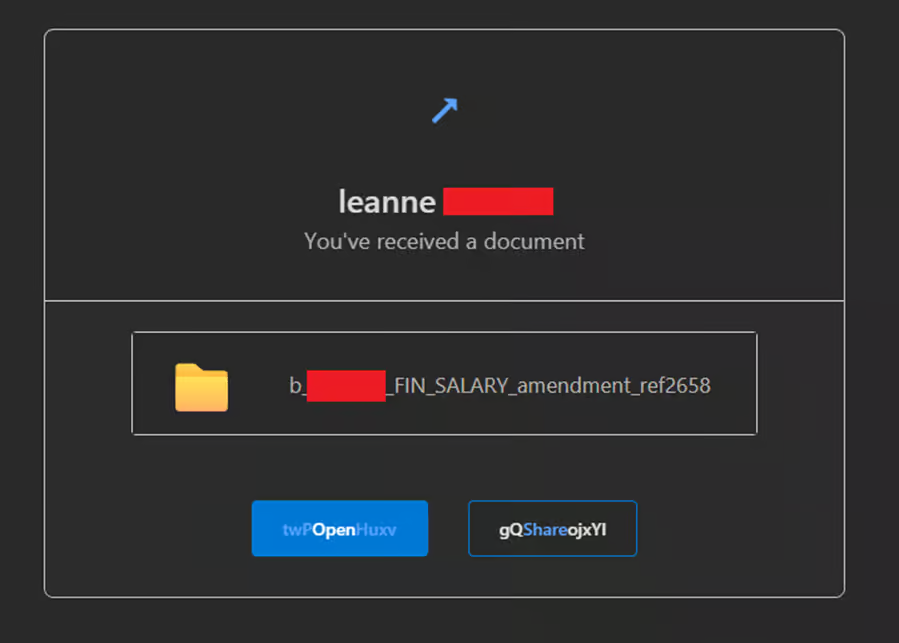
However, in dark mode, hidden padding reveals randomized alphanumeric strings like “twPOpenHuxv” and “gQShareojxYI” that fragment trigger words, effectively bypassing string-based detection rules employed by secure email gateways.
The attackers also implement a “warming up” strategy, sending benign initial emails days before launching phishing attempts to establish sender reputation. Additionally, they employ single-use phishing URLs that self-destruct after access, making forensic analysis more challenging.
Infrastructure Analysis Reveals Multi-Provider Strategy
Technical analysis of the campaign infrastructure reveals a deliberate multi-provider approach designed to complicate takedown efforts.
The attackers primarily utilize Mat Bao Corporation for domain registration, while leveraging Cloudflare for DNS services and Akamai Cloud (formerly Linode) for hosting phishing infrastructure. Additional providers include Web Commerce Communications Limited (WebNic.cc) for domain registration and Luxhost for DNS services.
Security teams are advised to implement comprehensive hunting queries, particularly for monitoring emails containing “FIN_SALARY” subject lines.
Organizations should prioritize executive awareness training and establish apparent incident reporting procedures to mitigate exposure to these sophisticated social engineering attacks.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates