In late August 2025, cybersecurity firm Cyfirma discovered Inf0s3c Stealer, a Python-based grabber that targets Windows hosts and exfiltrates data via Discord.
The 64-bit Portable Executable is first compressed with UPX and then packaged using PyInstaller, creating dual-layer packing that thwarts signature detection and complicates reverse engineering.
Upon execution, the malware reconstructs embedded Python bytecode from its PyInstaller overlay and creates a workspace under the %TEMP% directory.
In the first stage, it harvests system details by running native Windows commandssysteminfo and getmac and invoking APIs such as OpenProcessToken, GetTokenInformation, and GetEnvironmentVariableW to capture host identifiers, CPU specifications, product keys, and network parameters.
Next, it traverses user directories (Desktop, Documents, Pictures, Music, Videos, Downloads) using FindFirstFileW, WriteFile, and the tree /A /F command to generate hierarchical listings. Simultaneously, it captures desktop screenshots via GDI+ APIs and, if granted permission, webcam images.
The final collection phase focuses on credential theft: the stealer parses browser profiles to extract cookies, autofill entries, and browsing history; queries the registry for Wi-Fi passwords; and targets session files and tokens for applications such as Discord, Telegram, cryptocurrency wallets, and gaming platforms, including Roblox, Minecraft, and Epic Games.
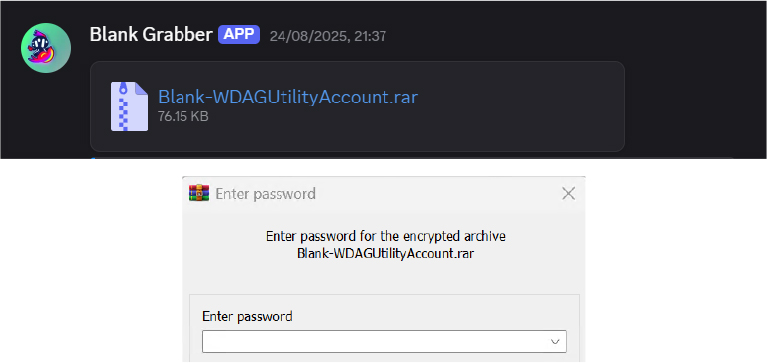
Once all data is gathered, the malware organizes the files into System, Directories, and Credentials folders before invoking rar.exe to create a password-protected archive named Blank-WDAGUtilityAccount.rar, secured with the hardcoded password blank123, preventing straightforward forensic analysis.
Persistence, Exfiltration, and Defense
Instead of traditional command-and-control servers, Inf0s3c Stealer abuses the Discord API by uploading the encrypted archive to a malicious webhook labeled “Blank Grabber,” masking exfiltration within legitimate HTTPS traffic.
For persistence, it copies its executable into the Windows Startup folder with a .scr extension and leverages the ConvertStringSecurityDescriptorToSecurityDescriptorW API to bypass User Account Control.
The malware performs anti-analysis checks by inspecting BIOS strings for virtual environments and uses QueryPerformanceFrequency timing routines to detect debugging.
It can also disable antivirus services by intercepting security service endpoints and is capable of self-deletion (“melt”) after completing its mission to erase evidence.
To mitigate this threat, organizations should deploy behavior-based endpoint protection capable of unpacking PyInstaller executables and detecting anomalous use of compression tools.
Enforcing strict egress filtering to block unauthorized Discord webhooks and monitoring HTTP traffic for atypical file attachments will hinder data exfiltration.
Comprehensive logging of PowerShell and command-line activity will reveal suspicious commands like systeminfo, getmac, tasklist, and tree.
Implementing least-privilege policies, auditing registry changes and startup folder modifications, and maintaining up-to-date YARA rules, such as Cyfirma’s, Inf0s3c_Grabber_Malware enhances detection of emerging variants.
Complement these measures with network segmentation, offline backups, and regular employee training on phishing and safe handling of unknown executables to reduce organizational risk.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates