The North Korean-aligned threat group APT37, also known as ScarCruft, Ruby Sleet, and Velvet Chollima, has expanded its malware arsenal with sophisticated new tools targeting South Korean individuals connected to the North Korean regime and human rights activists.
Security researchers at Zscaler ThreatLabz have uncovered a coordinated campaign utilizing a Rust-based backdoor dubbed Rustonotto alongside established PowerShell and Python-based malware variants.
Advanced Multi-Language Malware Campaign
APT37’s latest operations demonstrate the group’s evolution toward modern programming languages and refined attack techniques.
The campaign orchestrates three primary malware components through a single command-and-control server: Rustonotto, the newly identified Rust-compiled backdoor active since June 2025; Chinotto, a well-documented PowerShell backdoor operational since 2019; and FadeStealer, a comprehensive surveillance tool first discovered in 2023.
Rustonotto represents the first known instance of APT37 leveraging Rust-based malware against Windows systems. The lightweight backdoor executes Windows commands received in Base64-encoded format and returns results using the same encoding method.
Despite its simplistic functionality, the malware’s use of the Rust programming language signals the group’s ongoing adoption of modern development frameworks, potentially supporting multi-platform attacks.
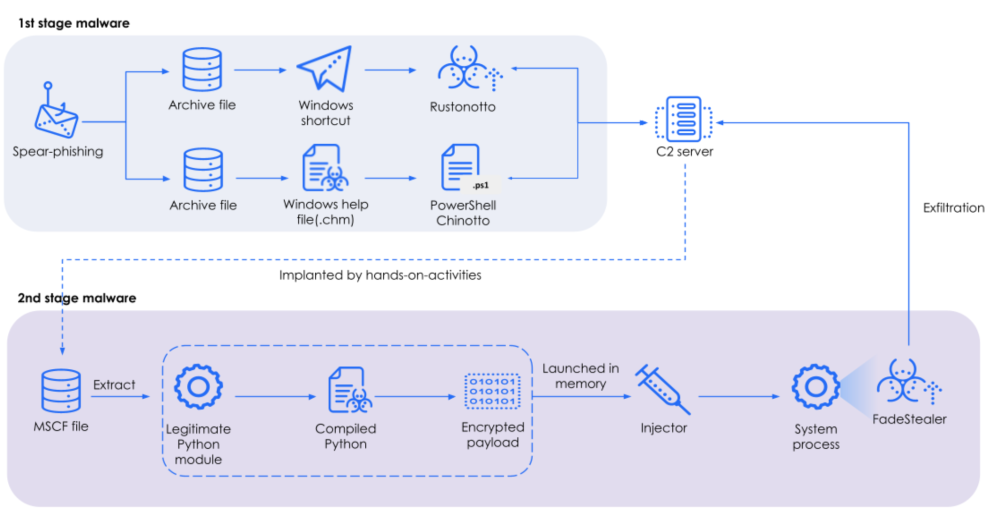
The attack chain begins with Windows shortcut files or Compiled HTML Help (CHM) files delivering the initial payload. When victims execute the malicious shortcut, a PowerShell script extracts embedded decoy documents and payloads using predefined markers.
The system creates a scheduled task named “MicrosoftUpdate” that executes the Rustonotto payload every five minutes, establishing persistent access to compromised systems.
Sophisticated Surveillance and Data Exfiltration
FadeStealer operates as the campaign’s primary surveillance component, implementing comprehensive data collection capabilities including keystroke logging, screenshot capture, audio recording, and monitoring of connected USB devices and MTP-enabled devices.
The malware compresses collected data into password-protected RAR archives using the hardcoded password “NaeMhq[d]q” before exfiltration to the C2 server.
The threat actors employ advanced code injection techniques, specifically utilizing Transactional NTFS (TxF) and Process Doppelgänging to inject malicious code into legitimate Windows processes stealthily.
A Python-based loader implements this sophisticated injection method, creating memory sections from transacted files before rolling back transactions and mapping payloads into suspended legitimate processes.
APT37’s C2 infrastructure utilizes compromised web servers running lightweight PHP scripts that manage communication between threat actors and malware implants through Base64-encoded exchanges.
The server maintains parent and child arrays for storing command results and pending instructions, providing centralized control over the entire malware ecosystem.
Zscaler’s multilayered cloud security platform detects this threat cluster with multiple signatures, including Win32.Backdoor.Chinotto, Win32.Trojan.Apt37.LZ, and Win32.Downloader.FadeStealer.
The campaign targets explicitly South Korean individuals involved in North Korean political affairs or diplomatic activities, consistent with APT37’s historical targeting patterns and strategic intelligence objectives.
Indicators Of Compromise (IOCs)
| MD5 | File name |
|---|---|
| b9900bef33c6cc9911a5cd7eeda8e093 | N/A |
| 7967156e138a66f3ee1bfce81836d8d0 | 3HNoWZd.exe.bin |
| 77a70e87429c4e552649235a9a2cf11a | wonder.dat |
| 04b5e068e6f0079c2c205a42df8a3a84 | tele.conf |
| d2b34b8bfafd6b17b1cf931bb3fdd3db | tele.dat |
| 3d6b999d65c775c1d27c8efa615ee520 | 2024-11-22.rar |
| 89986806a298ffd6367cf43f36136311 | Password.chm |
| 4caa44930e5587a0c9914bda9d240acc | 1.html |
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates