A newly discovered ransomware group called “The Gentlemen” has launched sophisticated attacks targeting enterprise environments across 17 countries, demonstrating advanced capabilities through the abuse of legitimate system components and highly tailored evasion techniques.
Trend Micro researchers identified the campaign in August 2025, revealing a threat actor that systematically adapts its tools based on the specific security solutions encountered in victim environments.
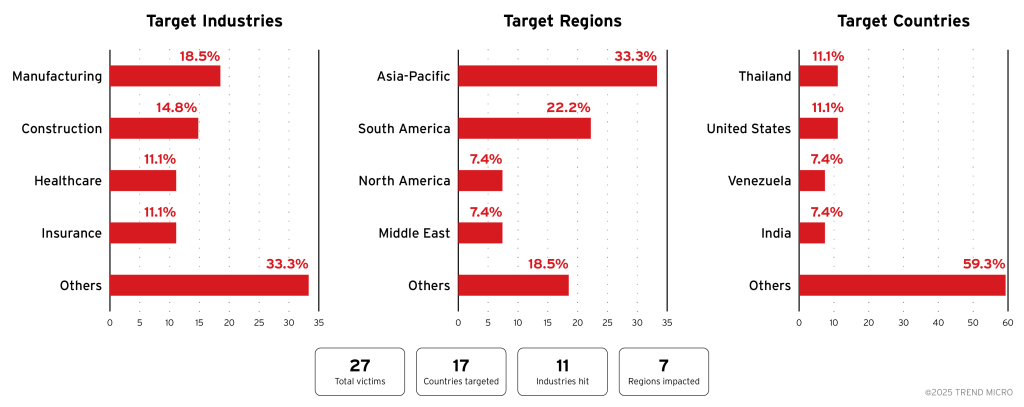
The group primarily targets manufacturing, construction, healthcare, and insurance sectors, with attacks concentrated in the Asia-Pacific region, particularly Thailand and the United States.
Healthcare organizations represent a significant portion of victims, highlighting the group’s disregard for critical infrastructure and potential public safety implications.
Technical Attack Chain and Defense Evasion
The Gentlemen employ a multi-stage attack methodology beginning with the exploitation of internet-facing services, specifically targeting exposed FortiGate servers to gain initial access.
Following network reconnaissance using Advanced IP Scanner, the attackers deploy sophisticated defense evasion techniques centered on legitimate driver abuse.
Their primary evasion tool, “All.exe,” works in conjunction with “ThrottleBlood.sys,” a legitimate signed driver that the attackers exploit to perform kernel-level manipulation.
This technique allows them to terminate protected security processes that would usually be shielded from termination by abusing Windows driver functionality.
When this approach proves insufficient, the group deploys an enhanced variant called “Allpatch2.exe,” specifically customized to neutralize security agent components based on their reconnaissance of the victim’s security infrastructure.
The threat actors demonstrate exceptional adaptability by conducting detailed analysis of endpoint protection mechanisms and modifying their tools mid-campaign.
They leverage PowerRun.exe, a legitimate utility, for privilege escalation while systematically weakening security controls through registry modifications that affect authentication and remote access protocols.
Group Policy Manipulation and Lateral Movement
The Gentlemen exhibit advanced Active Directory knowledge by manipulating Group Policy Objects (GPO) to facilitate domain-wide compromise.
They use Group Policy Management Console tools to deploy malicious configurations across entire domains while executing encoded PowerShell commands to identify Primary Domain Controllers for high-impact operations.
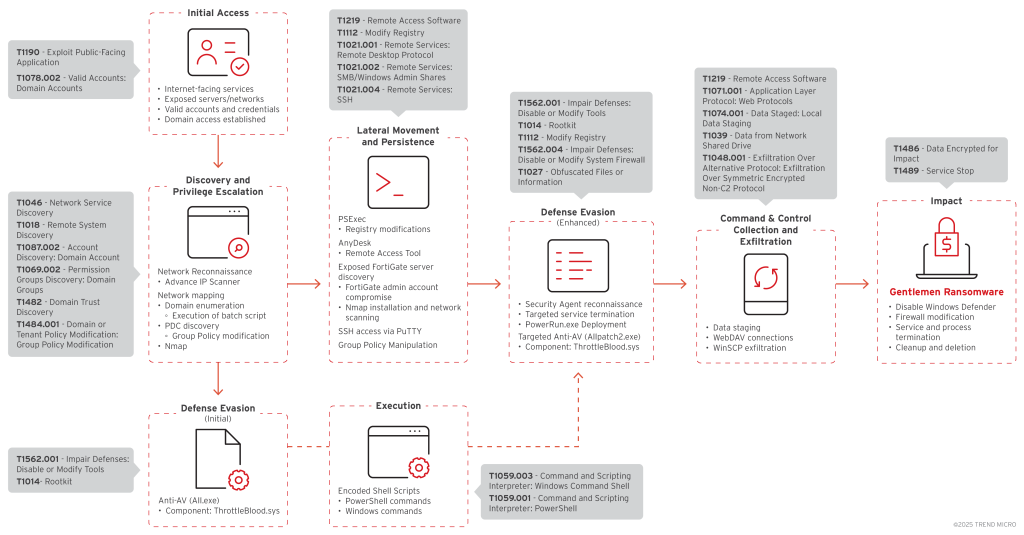
For lateral movement, the attackers utilize PsExec and establish persistent command-and-control access through AnyDesk remote access software.
They maintain operational security by using encrypted channels for data exfiltration via WinSCP and deploy comprehensive network scanning using Nmap for infrastructure mapping.
The ransomware deployment occurs through the domain’s NETLOGON share, ensuring widespread distribution across all domain-joined systems.
The payload requires an 8-byte password parameter and aggressively terminates backup, database, and security services while deleting forensic artifacts, including shadow copies, event logs, and Windows Defender support files, to impede recovery efforts.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates