Adversaries are increasingly abusing remote monitoring and management (RMM) tools such as ITarian (Comodo), PDQ Connect, SimpleHelp, and Atera in large-scale phishing campaigns, according to joint research by Red Canary Intelligence and Zscaler threat hunters.
Attackers are repurposing these legitimate IT solutions to establish stealthy persistence mechanisms, evade detection, and deliver secondary malware like info-stealers and ransomware.
Browser Updates and Fake Invitations as Lures
The campaigns rely on tried-and-tested social engineering lures, with fake browser updates being one of the most effective delivery techniques. In one incident, compromised sports and healthcare websites redirected users to fraudulent Chrome update pages.
A sophisticated JavaScript overlay displayed a full-screen iframe, fingerprinted victims, and redirected them to attacker-controlled domains such as chromus[.]icu and mypanelsuper[.]online.
Clicking the “Update Chrome” button initiated the download of an ITarian RMM MSI installer, which executed a malicious payload (DicomPortable.exe) and sideloaded trojanized DLLs, such as Qt5Core.dll and sciter32.dll.
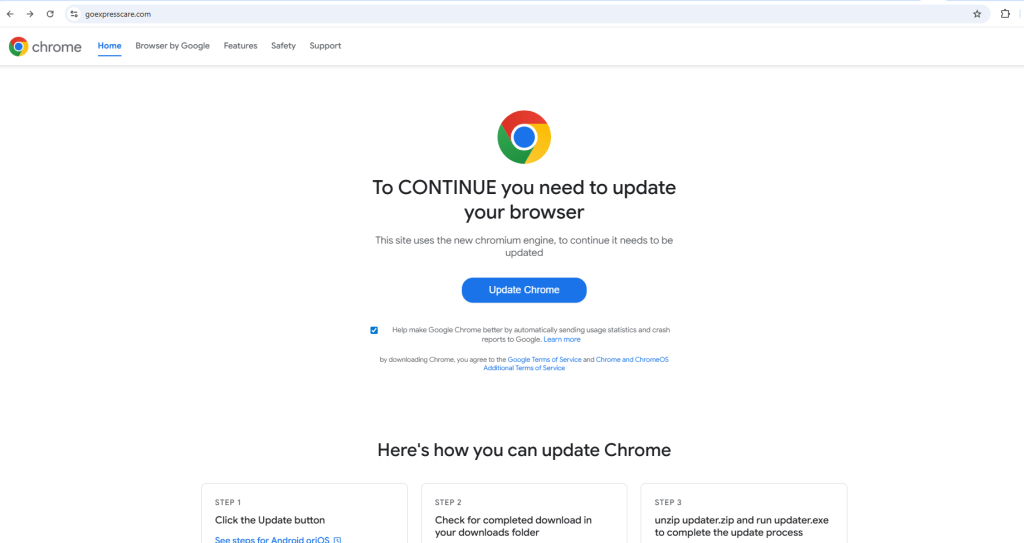
These in turn deployed HijackLoader and DeerStealer, with outbound connections to C2 domains including pianepal[.]com and opalcatacomb[.]pro.
Meeting and party invitations have also emerged as recurring phishing vectors. Adversaries distributed fake Teams and Zoom installers, which in reality dropped PDQ and Atera RMM agents.
In some observed cases, the installers were designed to mimic legitimate meeting software launch behavior, while others leveraged social themes such as e-invites disguised as “Party Card Viewer” applications.
Analysts discovered MSI payloads hosted on Cloudflare R2 object storage (filenames eventbite.msi and meetingevite.msi), demonstrating how attackers exploit trusted cloud services.
Once executed, Atera agents registered with attacker-controlled accounts by embedding the adversary’s email address in the installation command line.
More recently, adversaries delivered SimpleHelp installers under names like einvite.exe and immediately chained them with another RMM, ScreenConnect, to ensure redundant access.
Some of these installations communicated with malicious infrastructure such as pserial[.]us and relay. kaykaysamba[.]xyz.
In government-themed campaigns, fake IRS and Social Security forms led to PDQ Connect or ScreenConnect installations, with lure domains including doc-irs[.]us and secure333[.]servconfig[.]com.
Persistence and Detection Challenges
By abusing legitimate RMM platforms, adversaries gain hands-on keyboard access that blends in with everyday IT administration tasks.
Persistence is achieved through registry modifications and sideloaded DLLs, enabling implants like DicomPortable.exe to survive reboots while exfiltrating browser credentials and system information.
Attackers increasingly deploy multiple RMM tools in tandem, establishing layered access channels resistant to remediation.
Detection opportunities focus on identifying anomalous use of RMM executables such as RmmService.exe, AteraAgent.exe, or renamed SimpleHelp binaries executed by users from suspicious paths.
Organizations are advised to maintain strict baselines of approved RMM usage, monitor for unusual command-line parameters, and restrict downloads from unknown domains.
Enhanced network visibility, detection of newly registered lure domains, and application of browser isolation controls against cloud services are critical in countering this trend.
Indicators
IP addresses
185.80.234[.]36– Malicious SimpleHelp C2
Domains
attendrsvpvite[.]com– Lure domain for party invitego-envitelabel[.]com– Lure domain for party invitearc.dramaticdream[.]com– Malicious ScreenConnect C2tqewam.anondns[.]net– Malicious ScreenConnect C2
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates