Counter Threat Unit™ researchers have identified a sophisticated cybercriminal operation targeting organizations worldwide through an advanced ransomware campaign.
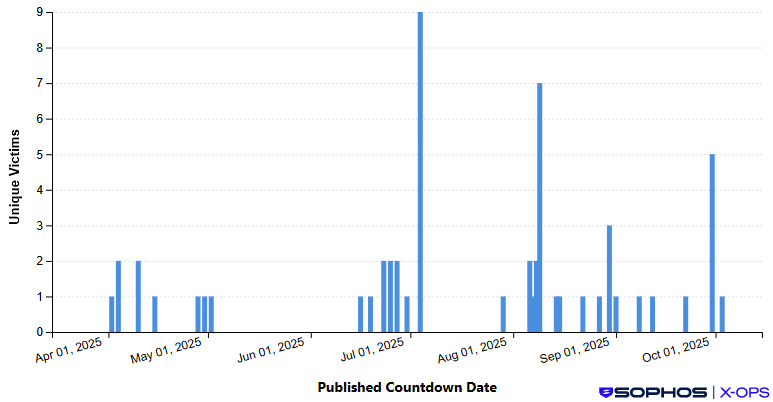
The threat group, known internally as GOLD SALEM and by Microsoft as Storm-2603, has compromised 60 victims since launching its operations in March 2025, positioning itself among mid-tier ransomware operations during this period.
Advanced Exploitation Techniques Target SharePoint Infrastructure
GOLD SALEM demonstrates significant technical sophistication by leveraging the Microsoft SharePoint ToolShell exploit chain for initial network access.
This complex attack sequence combines four critical vulnerabilities: CVE-2025-49704, CVE-2025-49706, CVE-2025-53770, and CVE-2025-53771. The exploitation process results in the deployment of an ASPX webshell, enabling remote command execution through the IIS worker process (w3wp.exe).
The group’s technical arsenal includes advanced evasion techniques, notably employing Bring Your Own Vulnerable Driver (BYOVD) methodology using a compromised Baidu Antivirus driver renamed as googleApiUtil64.sys.
This driver, affected by CVE-2024-51324, allows arbitrary process termination to bypass endpoint detection and response (EDR) systems. Following initial compromise, threat actors deploy Golang-based WebSockets servers for persistent access independent of webshells.
Lateral movement operations utilize established tools, including PsExec and Impacket, for network traversal, while Mimikatz targets Local Security Authority Subsystem Service (LSASS) memory for credential extraction.
The group has also been observed abusing the legitimate Velociraptor digital forensics tool to establish Visual Studio Code network tunnels within compromised environments.
Global Impact and Attribution Challenges
The campaign spans multiple continents, affecting organizations across North America, Europe, and South America, ranging from small government entities to multinational corporations.
Notably, GOLD SALEM listed a Russian engineering services company on September 8, 2025, suggesting operations outside traditional cybercriminal safe havens.
The group operates a Tor-based dedicated leak site (DLS) where 19 of 60 victims (32%) have had their data published. Additionally, threat actors claim to have sold data from 27 victims (45%) to private buyers; however, these figures may be inflated.
Microsoft attributes the group to China-based actors with moderate confidence, though insufficient evidence exists for definitive attribution.
GOLD SALEM’s recruitment efforts on underground forums seeking exploits for enterprise applications like Veeam, ESXi, and SharePoint, along with EDR-killing tools, indicate potential ransomware-as-a-service expansion plans.
The group assigns 12-14 day countdown timers for ransom payments, typical of modern ransomware operations.
Organizations should prioritize aggressive patching policies for internet-facing services, implement comprehensive endpoint monitoring, and maintain robust incident response capabilities to counter this evolving threat.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates