A new ransomware group, Kawa4096, emerged in June 2025, quickly gaining notoriety after targeting multinational organizations across countries, including the United States and Japan.
Unlike many established groups that focus on a specific sector, Kawa4096 shows no industry preference, striking companies in finance, education, and services.
While there is no public confirmation of it functioning as a Ransomware-as-a-Service (RaaS) operation, the group has raised red flags in the security community by executing multiple rapid-fire attacks within weeks of its discovery.
Double Extortion and Organized Operations
Kawa4096 operates via a Tor-based leak site where stolen victim data is published if ransom demands go unmet. The group employs a double extortion model, stealing and encrypting files before threatening to release sensitive data.
Uniquely, it generates dedicated claim URLs for each victim, highlighting its structured negotiation mechanism.
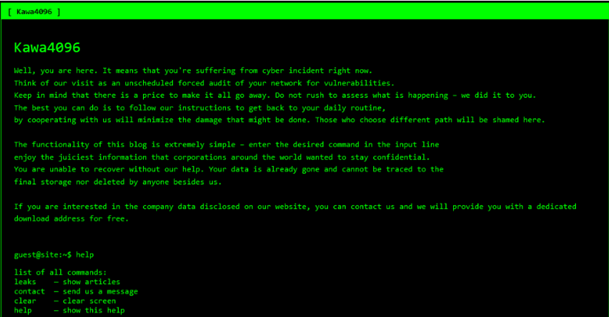
Although ransom amounts and payment procedures remain undisclosed, early ransom notes bear striking similarity to those of the Qilin ransomware, even using the same strategy of listing stolen data categories, such as customer and financial records, to increase pressure on targets.
Technical analysis shows that the ransomware uses a mutex named “SAY_HI_2025”, created via the CreateMutexA API, to prevent duplicate executions on infected hosts.
Its executable reads embedded resource configurations through APIs like LoadResource and FindResourceW, allowing the malware to access encryption rules and process termination lists before initiating encryption.
Technical Breakdown of the Attack
Kawa4096 includes a set of exclusion rules to avoid crippling core system functions and ensure victims remain in a negotiable state. These include skipping extensions such as .exe, .dll, and .sys, omitting critical directories like Program Files, and avoiding files tied to boot processes.
At the same time, it forcefully kills processes such as sqlservr.exe, outlook.exe, and winword.exe to unlock data stores and disrupt business continuity.
The ransomware employs a partial encryption strategy to expedite attacks. For large files, it splits them into 64KB chunks and encrypts only 25% of the data using the Salsa20 stream cipher.
Despite partial locking, files such as databases and documents become unreadable, maximizing damage while reducing runtime. Encrypted files receive new extensions consisting of the original filename, its extension, and nine random alphanumeric characters.
To block recovery attempts, Kawa4096 deletes volume shadow copies, executing commands like vssadmin.exe Delete Shadows /all /quiet and wmic shadowcopy delete /nointerface. This ensures victims cannot easily restore data without paying ransom.
The presence of ransom notes named !!Restore-My-file-Kavva.txt across directories provides Tor-based contact links and QTOX IDs for negotiation. In several instances, leaked customer data has already surfaced on the group’s dark web portals.
Security Community Response
Security vendor AhnLab confirmed active monitoring of Kawa4096, listing recent detections including Ransomware/Win.KawaCrypt and Ransomware/Win.KawaLocker variants between July and August 2025.
Multiple endpoints have flagged their behavioral traits, including ransomware persistence, process manipulation, and encryption attempts.
With its aggressive targeting strategy, partial file encryption scheme, and organized double extortion tactics, Kawa4096 represents one of the fastest-emerging ransomware threats of 2025, raising concerns about whether it will evolve into a larger RaaS ecosystem similar to Conti or BlackCat in the near future.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates