Nimbus Manticore, an Iran-linked advanced persistent threat (APT), has intensified a covert campaign targeting defense manufacturing, telecommunications, and aviation sectors in Western Europe.
Check Point Research attributes this activity to the group operating under aliases such as UNC1549, Smoke Sandstorm, and the “Iranian Dream Job” operations. Recent waves have focused on Denmark, Sweden, and Portugal, reflecting an IRGC-driven intelligence collection effort aligned with Tehran’s strategic priorities.
Sophisticated Spear-Phishing and Multi-Stage DLL Sideloading
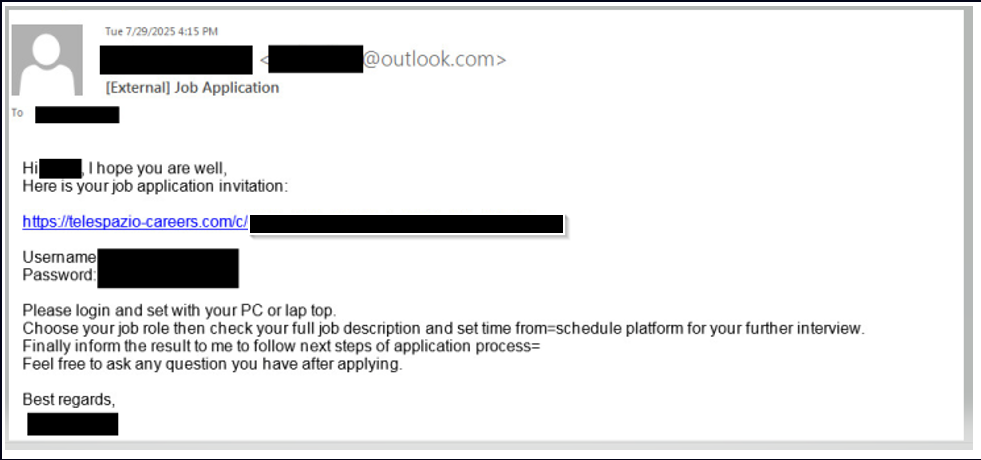
The attack chain begins with tailored spear-phishing emails disguised as recruitment outreach from leading aerospace and defense firms.
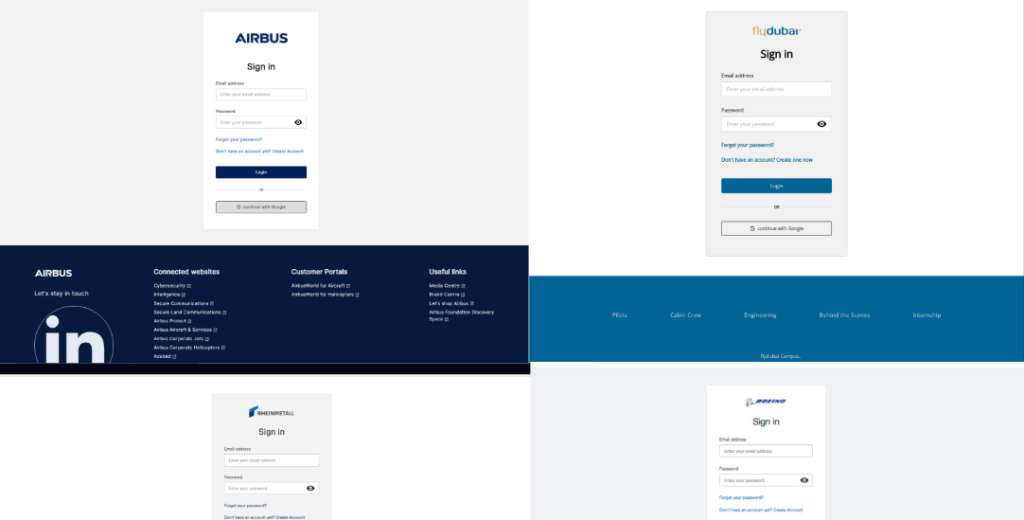
Victims receive unique URLs that host React-based fake career portals for Boeing, Airbus, Rheinmetall, and other companies. Once credentials are entered, a malicious archive is delivered.
A ZIP file often named Survey.zip contains Setup.exe, a legitimate Windows binary that sideloads a malicious userenv.dll. Setup.exe then spawns SenseSampleUploader.exe, a Windows Defender component, which in turn sideloads xmllite.dll using undocumented low-level NT API calls.
By manipulating the RTL_USER_PROCESS_PARAMETERS ‘DllPath’ field, the attacker forces SenseSampleUploader.exe to load xmllite.dll from the archive directory, overriding the default DLL search order.
Persistence is achieved by copying both Setup.exe (renamed MigAutoPlay.exe) and userenv.dll into %AppData%\Local\Microsoft\MigAutoPlay\ and registering a scheduled task.
The core backdoor, dubbed MiniJunk, is a heavily obfuscated derivative of the long-standing Minibike implant. Its DLLMain routine dynamically resolves API imports multiple times and encodes C2 traffic by reversing bytes and wide-string data.
After confirming execution under MigAutoPlay.exe, MiniJunk hooks ExitProcess to maintain stealth and spawns a networking thread that communicates with three to five redundant HTTPS-based C2 domains.
Commands formatted as strings separated by “##” permit file operations, process creation, DLL loading, and system enumeration.
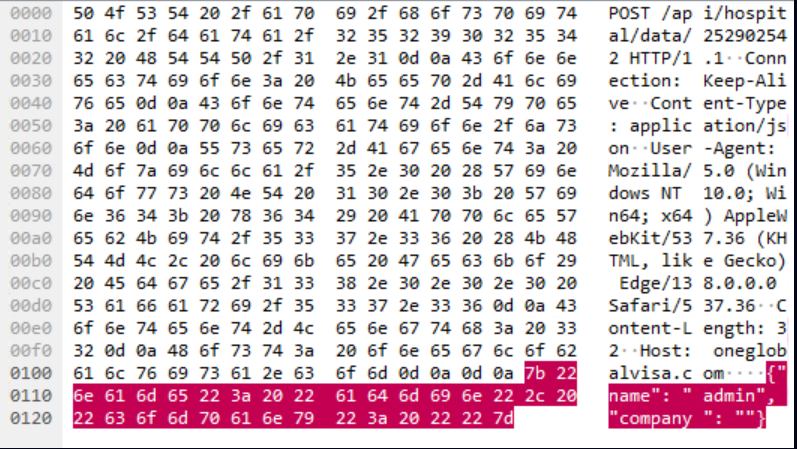
The toolset includes MiniBrowse, a lightweight stealer that injects into Chrome or Edge to harvest saved credentials. MiniBrowse exfiltrates data via JSON payloads over HTTP, requiring non-200 responses to proceed.
Heavy Obfuscation and Stealth Tradecraft
Nimbus Manticore employs custom LLVM-based compiler passes to insert opaque predicates, junk code blocks, and per-string encryption routines.
These techniques inflate binary size to evade endpoint detection timeouts, while digital code signing via SSL.com certificates has driven detections on VirusTotal to zero for many samples.
The actor’s use of Cloudflare-protected domains and Azure App Service for C2 enhances resiliency; unique domain naming patterns (e.g., check-backup-service-179.azurewebsites.net) allow fast rotation in response to takedowns.
Victimology analysis reveals a shift from the Middle East to Western Europe, with satellite providers, airlines, and defense contractors among the newly observed targets.
The campaign continues to leverage realistic recruitment pretexts and robust OPSEC, delivering tailored payloads that demonstrate a mature, well-resourced threat actor capable of conducting persistent and stealthy operations
IOCs
23c0b4f1733284934c071df2bf953a1a894bb77c84cff71d9bfcf80ce3dc4c16- malicious zip
0b2c137ef9087cb4635e110f8e12bb0ed43b6d6e30c62d1f880db20778b73c9a – malicious zip
6780116ec3eb7d26cf721607e14f352957a495d97d74234aade67adbdc3ed339 – malicious zip
41d60b7090607e0d4048a3317b45ec7af637d27e5c3e6e89ea8bdcad62c15bf9 – malicious zip
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates