On August 18, Microsoft Threat Intelligence detected and neutralized a sophisticated credential-phishing campaign that exploited AI-generated code obfuscation techniques to bypass conventional defenses.
Attackers weaponized a compromised small-business email account to deliver a self-addressed phishing message, concealing real targets in BCC fields and masquerading as a file-sharing notification.
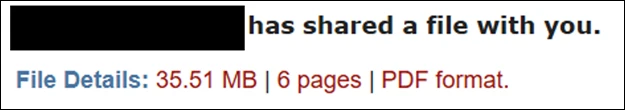
The email included an attachment named “23mb – PDF- 6 pages.svg,” a deceptive SVG file engineered to look like a PDF, yet containing embedded JavaScript designed to redirect victims to a phishing landing page.
AI-Generated Obfuscation Tactics Revealed Through Microsoft Analysis
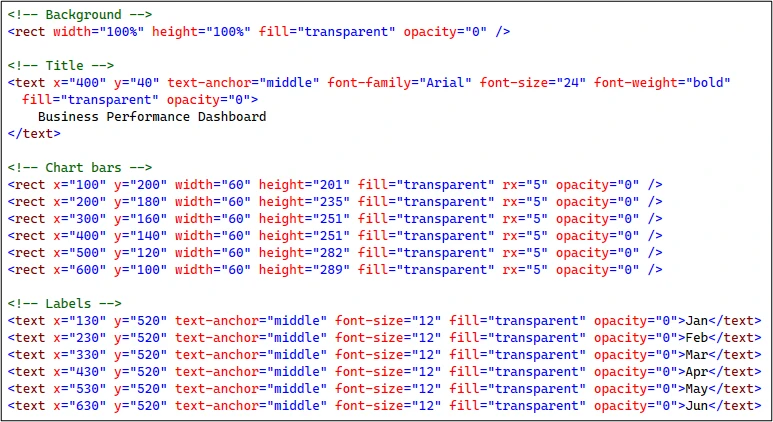
Analysis of the SVG payload revealed an unusual obfuscation strategy: instead of employing standard encryption or packing algorithms, the attackers structured the file to mimic a business analytics dashboard.
Invisible chart bars, month labels, and data tables were rendered fully transparent, serving as a decoy to mislead cursory inspections.
A hidden <text> element carried a long string of concatenated business terms, such as “revenue,” “operations,” “risk,” and “shares” encoded within a custom data analytics attribute.
Embedded JavaScript parsed these benign-looking metadata tokens and mapped them through a series of transformation routines to reconstruct the malicious functionality.
Microsoft Security Copilot’s assessment concluded that this layered, verbose code was highly likely to have been generated by a large language model (LLM).
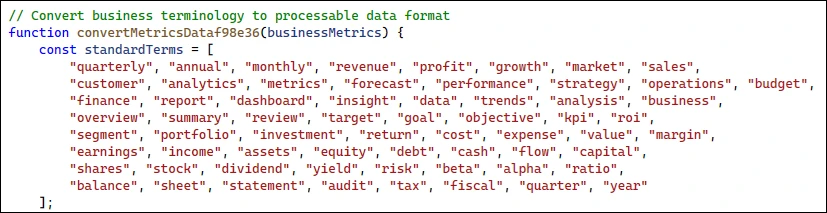
Indicators included descriptive function and variable names appended with pseudo-random hexadecimal suffixes (e.g., processBusinessMetricsf43e08, initializeAnalytics4e2250), overly modular and repetitive logic blocks for data mapping and offset correction, and formal, generic comments describing each transformation step.
The presence of both an XML declaration and CDATA-wrapped script sections elements is unnecessary for a functional SVG attack, further suggesting that the content was AI-generated and mirrored documentation examples rather than handcrafted code.
Despite the advanced obfuscation, Microsoft Defender for Office 365’s AI-powered protection successfully identified multiple detection signals.
The self-addressed email tactic with BCCed recipients, the atypical SVG file name, and the redirect to a previously flagged phishing domain triggered infrastructure and contextual heuristics. Behavioral analytics flagged the CAPTCHA gate and subsequent session tracking routines.
Critically, the very artifacts introduced by AI’s verbose naming conventions and formulaic encoding of business terms emerged as novel detection features, reinforcing defenders’ capacity to adapt to AI-driven attacks.
Although this campaign targeted predominantly US-based organizations and was limited in scope, it exemplifies a broader trend: threat actors are rapidly integrating generative AI into their toolkits to craft more convincing lures, automate payload obfuscation, and evade static signature-based defenses.
However, as Microsoft’s response demonstrates, AI can serve both sides of the cybersecurity battle. By leveraging machine learning across message context, infrastructure patterns, and behavior analysis, defenders can surface anomalies that transcend the sophistication of individual payloads.
Organizations are encouraged to adopt AI-augmented email security solutions, monitor for self-addressed campaigns, scrutinize unusual file types, and analyze scripts for synthetic code artifacts.
As AI continues to evolve, so too must defensive strategies to ensure that malicious innovation never outpaces detection capabilities.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates