RedNovember, the Chinese state-sponsored threat activity group formerly tracked as TAG-100 and overlapping with Storm-2077, has conducted a year-long global campaign compromising perimeter appliances of high-profile government and private sector organizations.
Between June 2024 and July 2025, the group leveraged open-source PoC exploits against firewall, VPN, and email server appliances to deploy the Go-based backdoor Pantegana and Cobalt Strike Beacon payloads, expanding its espionage operations.
Recorded Future’s Network Intelligence identified RedNovember’s persistent use of Pantegana, a multi-platform Go backdoor, to establish encrypted HTTPS C2 channels that support file transfers, system fingerprinting, and command execution.
The group supplemented this with Cobalt Strike Beacon payloads delivered via the LESLIELOADER Go-based loader and SparkRAT modules, enabling in-memory execution on both Windows and Linux hosts.
RedNovember also employed ExpressVPN and, more recently, Warp VPN to obscure administration of its C2 infrastructure.
Targets spanned multiple critical sectors. Insikt Group detected successful compromises of at least two US defense contractors and a European engine manufacturer, where SonicWall SSL VPN and F5 BIG-IP appliances were used for initial access.
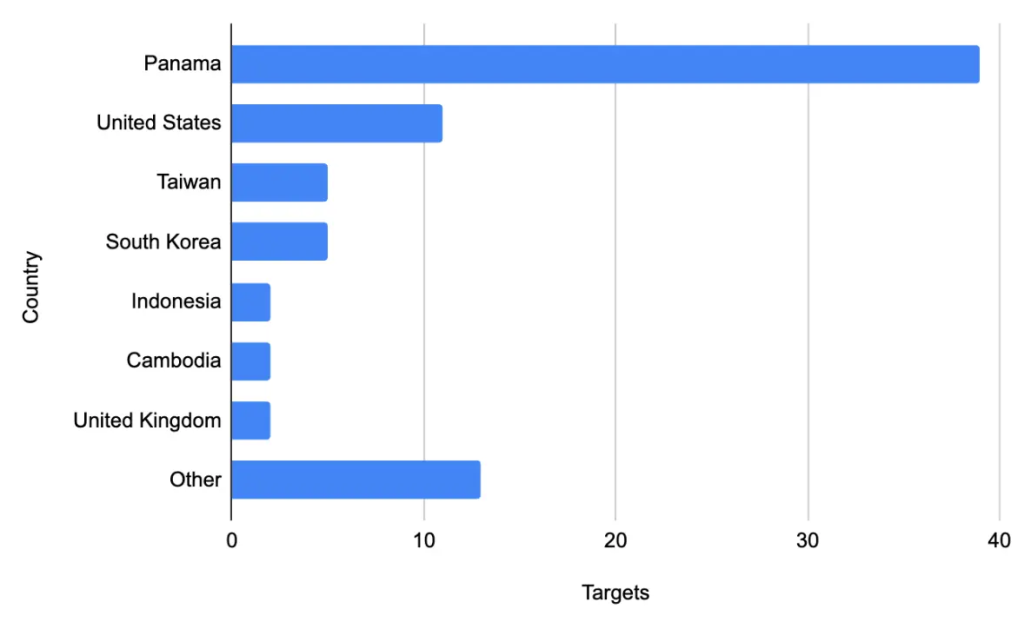
A trade-focused intergovernmental body in Southeast Asia, a central Asian foreign ministry, and a state security organization in Africa also fell victim to VPN and firewall exploits.
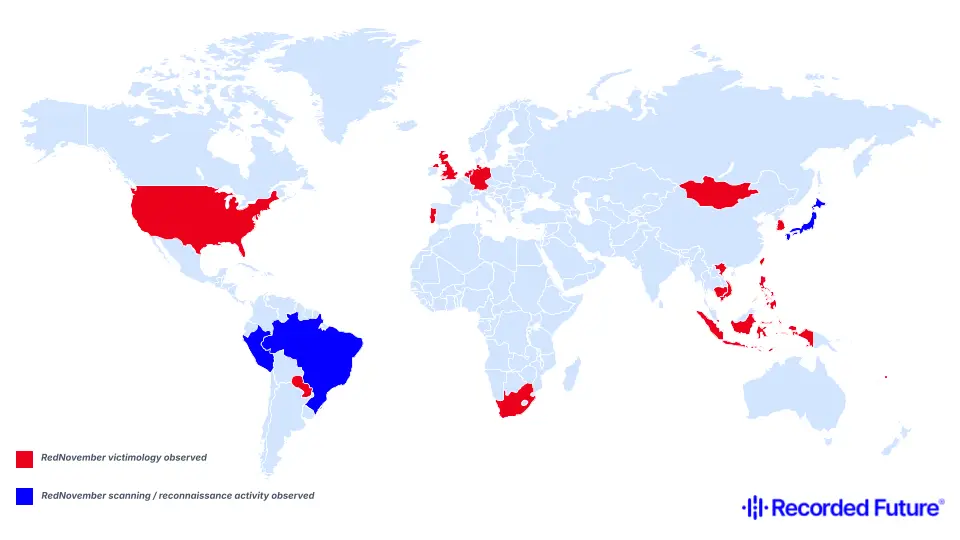
Reconnaissance activity against Ivanti Connect Secure (ICS) VPN infrastructure in April 2025 involved a major US newspaper and a US engineering and military contractor, although a full compromise was unconfirmed.
Surge Targeting Reflects Geopolitical Priorities
RedNovember’s activity often aligned with geopolitical events. In December 2024, Pantegana C2 communications targeted a Taiwan Air Force base and semiconductor R&D site concurrently with large-scale Chinese military exercises around the island.
The group’s April 2025 scans of over thirty Panamanian government bodies followed high-profile US defense diplomacy and Belt and Road Initiative developments.
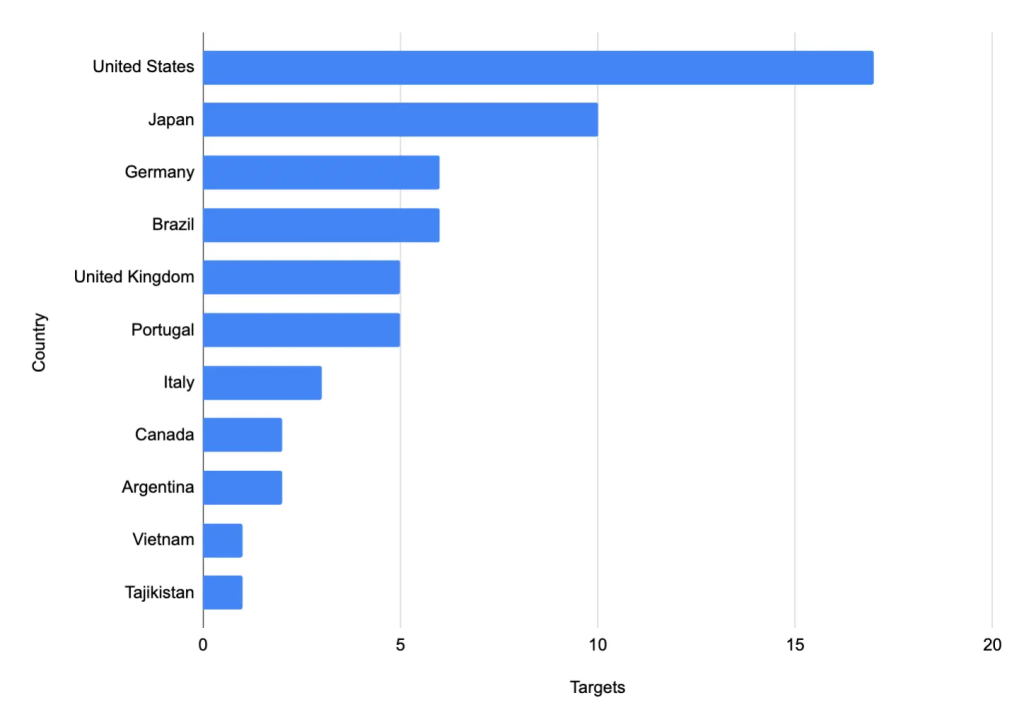
Similar opportunistic probing of Check Point VPN gateways occurred days after public release of the CVE-2024-24919 PoC exploit, affecting organizations across Brazil, Germany, Japan, Portugal, the UK, and the US.
(Source: Recorded Future)
Beyond government and defense, RedNovember expanded to law firms, energy companies, and aerospace research centers.
A Taiwanese IT company tied to semiconductor development and multiple Fijian institutions, including finance, transportation, and media, were also targeted via Outlook Web Access and Sophos SSL VPN portals.
This breadth underscores the group’s strategic focus on edge-device vulnerabilities, which often have limited logging and detection capabilities.
Organizations are urged to adopt intelligence-led patching prioritization for externally facing appliances, implement multi-factor authentication, and enhance network segmentation.
Real-time blocking of known Pantegana, SparkRAT, and Cobalt Strike C2 domains via Threat Intelligence modules can mitigate ongoing risks.
Recorded Future anticipates RedNovember will maintain its high-tempo exploitation of newly disclosed vulnerabilities in perimeter devices, capitalizing on publicized PoC code to scale operations.
Continuous monitoring of device logs and proactive threat hunting for unusual external communications remains critical to countering this persistent espionage threat.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates