Since at least 2019, the Chinese state-backed APT group Salt Typhoon has executed a highly targeted espionage campaign against global telecommunications networks, extracting critical signals intelligence and subscriber metadata.
Aligned with China’s Ministry of State Security (MSS) and bolstered by pseudo-private contractors such as i-SOON (Anxun Information Technology Co., Ltd.), Salt Typhoon employs custom firmware implants, living-off-the-land binaries, and stealthy router rootkits to maintain persistent, covert access within major telecom environments across the United States, United Kingdom, Taiwan, and the EU.
State-Sponsored Espionage and Persistent Access
Salt Typhoon initiates operations by scanning for and exploiting known CVEs in network edge devices routers, VPN concentrators, and firewalls often combining automated brute-force methods with unpatched software vulnerabilities.
Upon gaining entry, the group deploys resilient, firmware-level implants that survive routine updates, embedding encrypted HTTPS-based command-and-control (C2) channels within legitimate management protocols.
These implants beacon at irregular intervals and blend with normal network management traffic, effectively evading detection by security monitoring tools.
Through these long-dwell footholds, Salt Typhoon exfiltrates vast quantities of telecom intelligence, including VoIP configurations, session metadata, call detail records (CDRs), lawful intercept logs, and SS7 routing information. A 2024 breach of multiple U.S.
carriers, such as AT&T and Verizon, resulted in terabytes of stolen metadata, while a concurrent compromise of several state National Guard VPN gateways yielded network diagrams, administrator credentials, and incident response playbooks assets that can facilitate both real-time surveillance and battlefield preparation.
A notable tradecraft feature is Salt Typhoon’s use of bulk-registered domains under fabricated U.S. personas.
By registering dozens of English-language domains via ProtonMail and provisioning commercial DV certificates from GoDaddy and Sectigo, the group crafted seemingly benign SaaS portals.
However, recurring name servers like irdns.mars.orderbox-dns.com and registrant aliases such as “Shawn Francis” and “Monica Burch” created distinctive attribution signatures that defenders have leveraged to cluster and map the actor’s infrastructure.
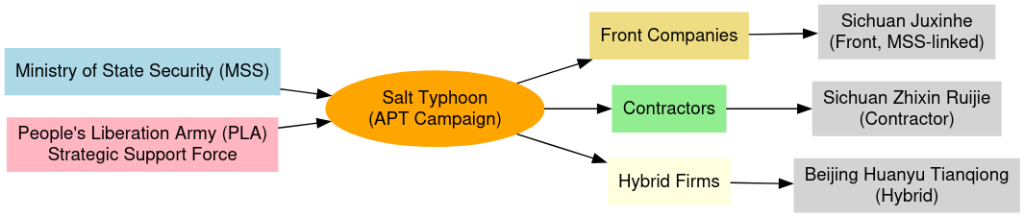
Underpinning this infrastructure are front companies and contractors based in Chengdu and Beijing Sichuan Juxinhe, Beijing Huanyu Tianqiong, and Sichuan Zhixin Ruijie disguised as legitimate cybersecurity firms.
These entities operate domain registration pipelines, host C2 servers, and supply covert tooling under the veneer of commercial services.
The 2024 i-SOON GitHub leak revealed automated scripts for domain provisioning and ProtonMail-based OPSEC wrappers, capabilities that Salt Typhoon continues to employ.
Security agencies now advise that proactive monitoring of passive DNS data, SSL certificate patterns, and registrant overlaps is essential for early warning.
Telecom operators should enforce multi-factor authentication for all administrative interfaces, restrict remote management to isolated networks, and rigorously audit firmware integrity on edge devices to detect unauthorized implants.
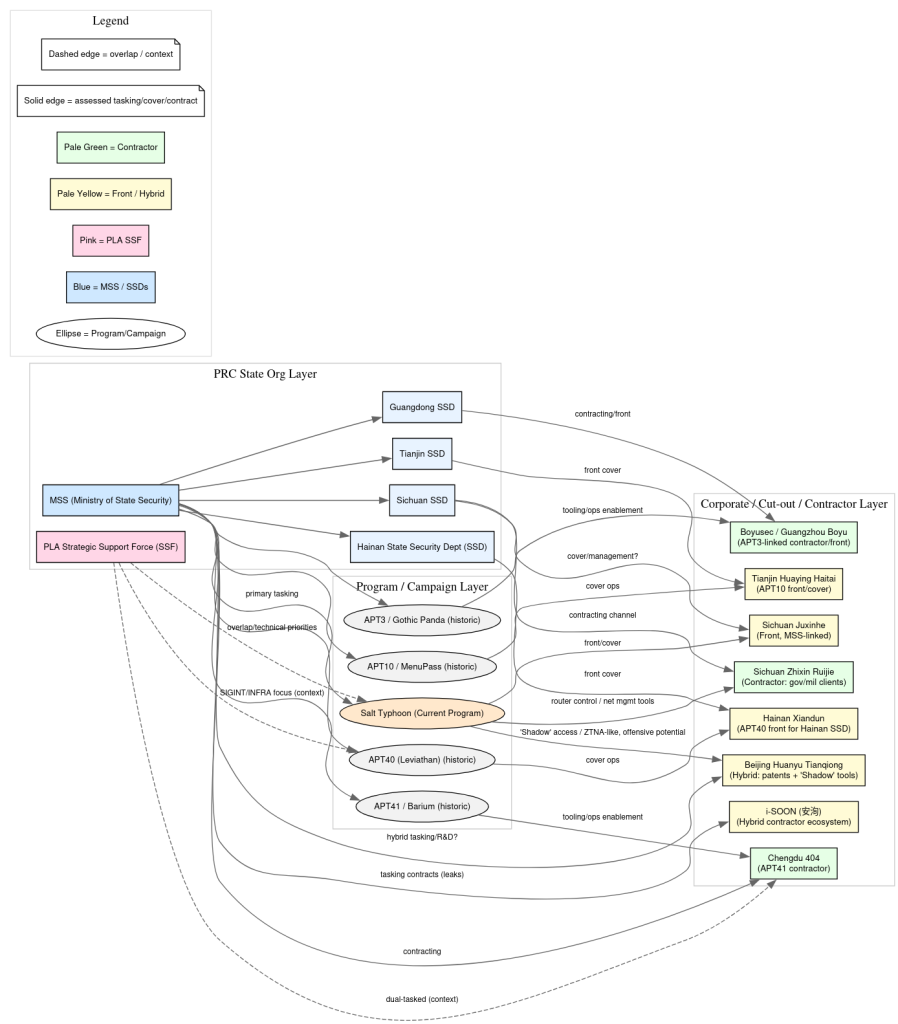
Salt Typhoon’s contractor-driven, dual-use espionage model represents the next evolution in China’s offensive cyber strategy, blending state-directed objectives with commercial execution to achieve scalable, deniable operations.
While their semi-industrialized approach yields occasional OPSEC lapses, the group’s advanced capabilities in firmware persistence and metadata harvesting underscore the urgent need for telecom providers to adopt robust endpoint security and continuous threat hunting to counter this sophisticated SIGINT threat.
Indicator of Compromise (IOCs) – Salt Typhoon Telco Campaigns
Name Server Hosts/IPs:
- irdns.mars.orderbox-dns.com
- ns4.1domainregistry.com
- ns1.value-domain.com
- earth.monovm.com, mars.monovm.com
IP Cluster:
- 162.251.82.125, 162.251.82.252, 172.64.53.3
SSL Certificate Indicators:
- Common Names (CN):
- *.myorderbox.com
- www.solveblemten.com
- Issuers:
- GoDaddy Secure CA – G2
- Sectigo RSA DV CA
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates