In early 2025, LummaStealer emerged as a prolific information stealer targeting industries ranging from telecom and healthcare to banking and marketing.
A coordinated law enforcement operation in May briefly disrupted its activities; however, recent months have seen novel LummaStealer variants resurface.
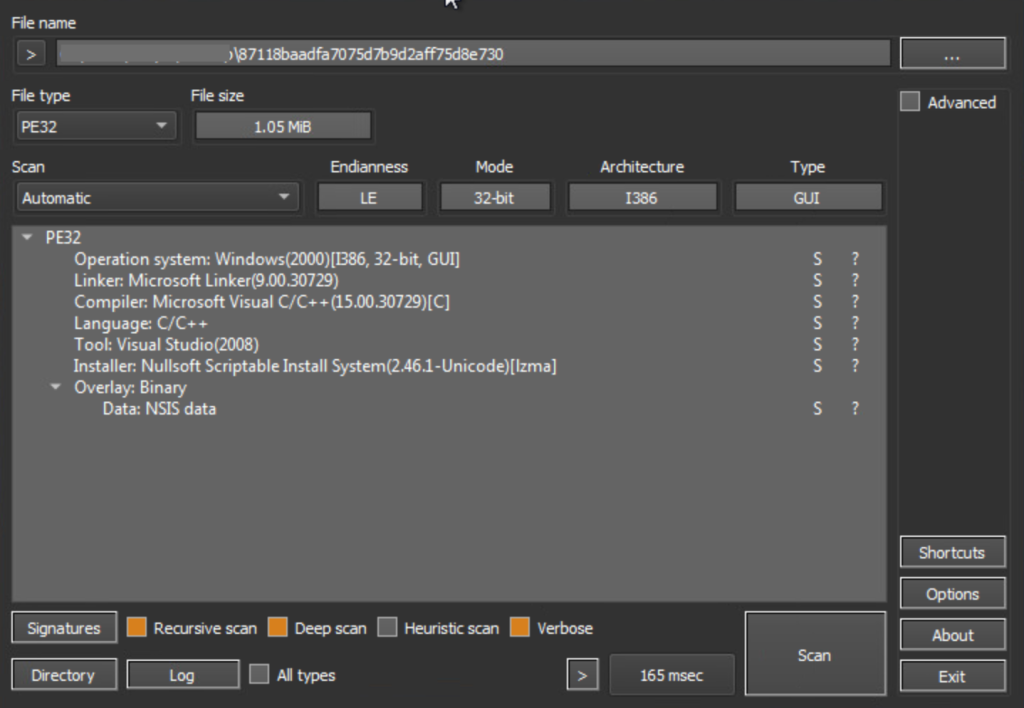
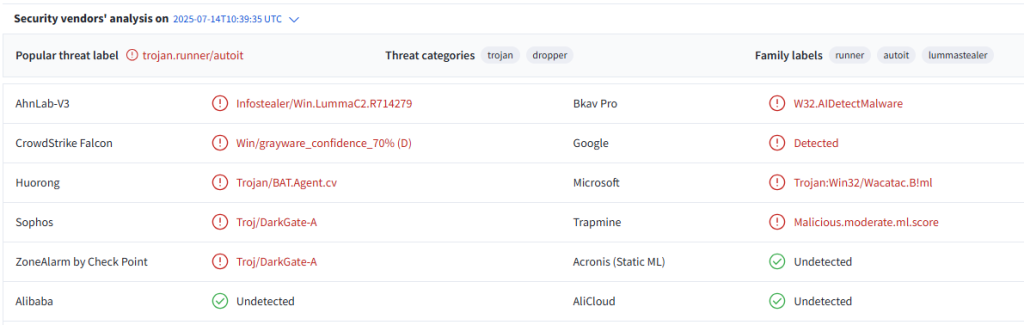
Netskope Threat Labs’ analysis of sample hash 87118baadfa7075d7b9d2aff75d8e730 reveals advanced obfuscation, sophisticated evasion, and robust persistence techniques, showcasing how machine learning can identify even brand-new threats with high confidence.
Obfuscated Installer and AutoIt Payload
The sample masquerades as a Nullsoft Scriptable Install System (NSIS) installer, confirmed by Detect It Easy.
Unpacked via 7-Zip, it yields an obfuscated NSIS script ([NSIS].nsi) and a $TEMP directory containing Parish.m4aan obfuscated batch file, along with additional .m4a blobs for subsequent payload stages.
The batch file extracts and launches autoit3.exe, renamed to evade basic detections. The dropped AutoIt script employs nested while loops and switch-case constructs to conceal its malicious logic, making static analysis challenging and hindering signature-based detection.
LummaStealer’s AutoIt payload incorporates multiple anti-analysis checks. It verifies environment variables, ensuring COMPUTERNAME and USERNAME are not sandbox defaults and scans for virtualization processes like vmtoolsd.exe, VboxTray.exe, and SandboxieRpcSs.exe.
An anti-debugging routine measures API call latency; significant timing discrepancies trigger self-termination.
Additionally, the script attempts to ping a non-existent domain; a successful response (indicative of a monitored sandbox) causes the script to exit immediately, while a failure hides the malware’s tray icon and allows it to proceed.
To neutralize security hooks, the payload restores the original bytes of critical functions in ntdll.dll, effectively unhooking them and thwarting interception by defense software.
Persistence is established via a Windows Internet Shortcut (.url) placed in the Startup folder. On reboot, this shortcut executes a JScript leveraging Wscript.Shell to relaunch autoit3.exe.
In-Memory Decryption and Decompression
Upon execution, LummaStealer separates decryption into two in-memory routines: one reconstructs the key mapping, and the other handles LZ-compressed data.
Utilizing the RtlDecompressFragmentWindows Using the LZ algorithm, the API inflates the compressed blob directly into memory, unveiling a portable executable (PE) file without writing the payload to disk.
This “fileless” technique significantly reduces forensic artifacts and complicates detection by traditional antivirus solutions.
Netskope’s Advanced Threat Protection platform unites static signatures with a cloud sandbox powered by a transformer-based machine learning model.
As the sandbox executes the sample in an isolated Windows environment, it captures process trees, API calls, registry modifications, file operations, and network activity. The model encodes hierarchical embeddings of each process tree node alongside vectors representing runtime behaviors.
By combining these embeddings, the AI flagged the LummaStealer sample with high confidence despite novel obfuscation and evasion tactics, demonstrating the power of ML to detect previously unseen threats at first sight.
IOCs
MD5
87118baadfa7075d7b9d2aff75d8e730
SHA-1
78da004e332be8eaa5e111c34d6db3a28abb9767
SHA-256
ff7a1388fa59a9e1b43c5c88a1ee30e4abcec21a39882812a045aa9d9b865170
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates