On May 9, 2024, a heavily obfuscated JavaScript file masquerading as a W-9 tax form marked the start of a nearly two-month intrusion attributed to the Lunar Spider group.
Delivered via a phishing lure, the script downloaded an MSI installer that deployed the Brute Ratel loader, which in turn injected the Latrodectus downloader into the explorer.exe process.
This “single-click” vector granted attackers initial foothold and immediate command and control (C2) access through multiple Cloudflare-proxied domains.
Disguised JavaScript and Brute Ratel Delivery
The malicious JavaScript named Form_W-9_Ver-i40_53b043910-86g91352u7972-6495q3.js contained extensive filler comments to evade detection.
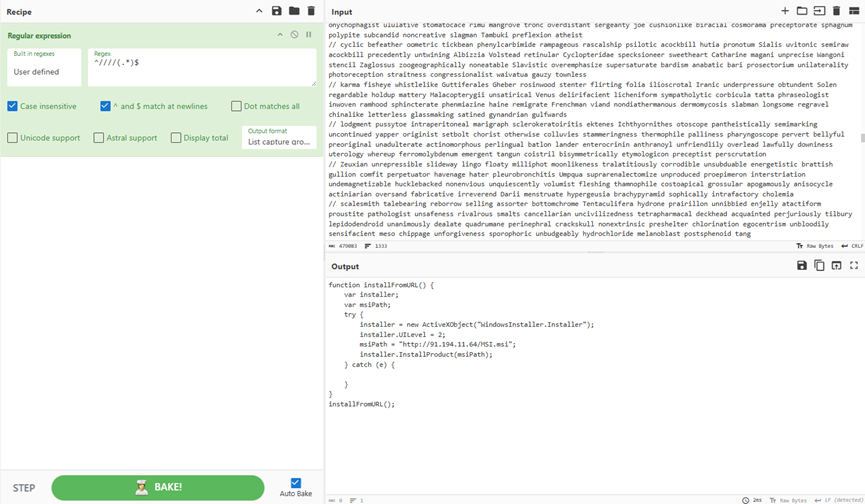
Upon execution, it fetched MSI.msi from hxxp://91.194.11[.]64, triggering a custom action in the installer that ran upfilles.dll via rundll32.exe and resolved APIs with a bespoke hashing algorithm.
An XOR-encrypted intermediary payload decrypted into the Brute Ratel C4 implant (BRC4), establishing persistent C2 channels.
Within hours, Latrodectus was process-injected to retrieve a stealer module, enabling credential harvesting.
Using command ID 21, the explorer.exe injection downloaded fxrm_vn_9.557302425.bin, which targeted Chromium-based browsers, Firefox, Internet Explorer, and Outlook configurations.
Extracted data, including passwords, cookies, and SMTP/IMAP credentials, was base64-encoded in shared memory for exfiltration.
Six hours post-infection, attackers launched a BackConnect session, deploying VNC for interactive access. On day 3, they leveraged a Windows Answer file (unattend.xml) containing plaintext domain admin credentials to escalate privileges.
Day 4 saw the deployment of Cobalt Strike beacons via PsExec, authenticated with the stolen domain admin account. Active Directory reconnaissance with AdFind preceded lateral movements to domain controllers, file servers, and backup systems.
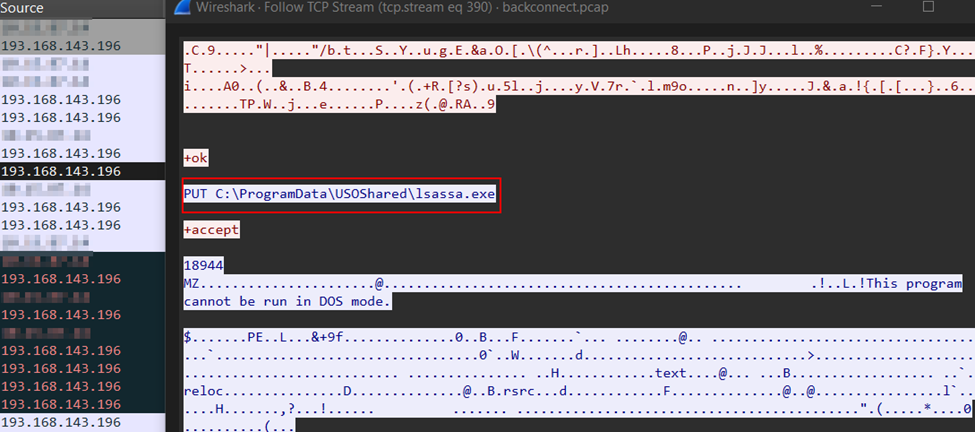
A custom .NET backdoor dubbed lsassa.exe provided additional persistence, creating a scheduled task named “SchedulerLsass” under %ALLUSERSPROFILE%\USOShared\lsassa.exe. This backdoor polled its C2 every 250 seconds, executing remote commands silently.
Long-Term Persistence and Data Exfiltration
Brute Ratel components were periodically refreshed via registry Run keys and scheduled tasks. On day 20, malicious scripts executed a renamed rclone binary to exfiltrate terabytes of data over FTP during a ten-hour window.
Further reconnaissance and credential dumping from Veeam backup software occurred on day 26, using the publicly available Veeam-Get-Creds.ps1 to harvest additional plaintext passwords.
Despite intermittent dormancy, C2 callbacks persisted for nearly two months as the threat actor toggled between Brute Ratel, Cobalt Strike, and BackConnect modules. Attempts to exploit Zerologon (CVE-2020-1472) and Metasploit lateral tools failed, but their diverse toolkit ensured continued access.

This intrusion underscores the potency of obfuscated JavaScript delivery and multi-stage loaders, such as Brute Ratel, in evading defenses. Organizations should:
- Enforce strict email filtering and sandboxing for script files.
- Monitor for anomalous MSI downloads and rundll32 invocations.
- Audit Answer files and remove embedded plaintext credentials.
- Deploy endpoint detection rules for Brute Ratel and Latrodectus patterns.
- Limit use of high-privilege service accounts in provisioning scripts.
By integrating these defenses and maintaining vigilant threat hunting, security teams can disrupt similar long-lived campaigns before extensive data loss occurs.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates