Late August 2025 saw the discovery of Klopatra, a highly sophisticated Android Remote Access Trojan (RAT) and banking trojan, by Cleafy’s Threat Intelligence team.
Klopatra distinguishes itself through its integration of the commercial-grade Virbox protection suite and extensive use of native C/C++ libraries, a combination rarely seen in mobile malware.
These architectural choices solidify its evasion capabilities, rendering traditional static and dynamic analysis tools largely ineffective.
Evasion Through Virbox and Native Code
Klopatra’s core functionalities, including network communication, payload unpacking, and anti-analysis routines, reside within native libraries protected by Virbox. This multi-layered obfuscation enforces anti-debugging checks, emulator detection, and runtime integrity verification.
By shifting the bulk of its logic from Java to native code, Klopatra drastically reduces its visibility to Android runtime instrumentation frameworks.
Researchers encountered persistent challenges when attempting to unpack or emulate the payload, often requiring manual unpacking of the Virbox wrapper before accessing the underlying logic.
Seamless Overlay Attacks for Credential Theft
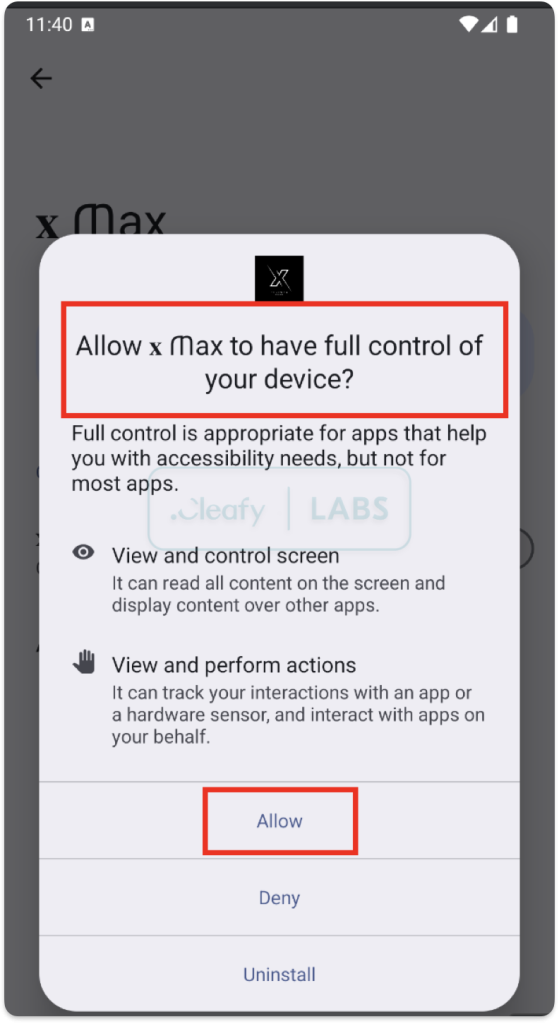
Following initial infection via a dropper disguised as “Mobdro Pro IP TV + VPN,” Klopatra requests REQUEST_INSTALL_PACKAGES and, subsequently, Android Accessibility Services. The latter grants the malware comprehensive control: screen reading, input logging, and UI simulation.
Upon detecting the launch of targeted financial or cryptocurrency apps, the RAT retrieves custom HTML from its C2 server and displays a perfect overlay mimicking the legitimate login interface. Captured credentials are exfiltrated immediately.
In parallel, Klopatra offers two VNC modes: Standard VNC, which mirrors the user’s screen for observation, and Hidden VNC, which overlays a black screen to the victim while giving attackers full, clandestine access to navigate apps and execute transactions undetected.
European Botnets and Turkish-Speaking Operators
Operational telemetry reveals two primary botnets active in Europe: one with over 1,000 infections in Spain and another with approximately 450 devices in Italy, totaling over 3,000 compromised endpoints.
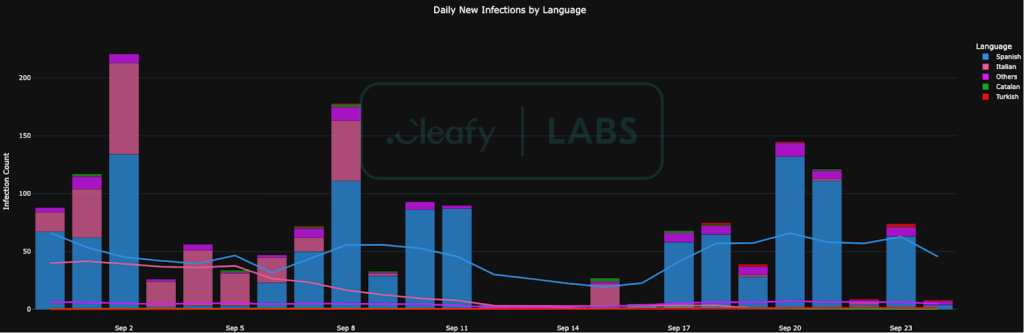
Analysis of C2 field names and code comments terms like “etiket,” “favori_durumu,” and “bot_notu”—alongside vulgar operator notes referencing failed EUR 7,000 transfers and unlock patterns, point conclusively to a Turkish-speaking criminal group.
A smaller staging server with only nine bots spread across the Middle East appears to function as a testing environment, underlining an agile development cycle that has yielded more than 40 distinct builds since March 2025.
Klopatra’s self-preservation mechanisms reinforce its persistence: it auto-grants permissions via Accessibility Services, exempts itself from battery optimizations, and uninstalls known security applications.
This blend of commercial-grade protections, native-code architecture, and real-time remote control marks a significant escalation in the professionalism of mobile malware.
Financial institutions and security teams must advance beyond signature-based defenses to deploy device-level behavioral monitoring and proactive threat intelligence sharing.
Continuous analysis of C2 infrastructure and rapid threat hunting are critical to counter Klopatra’s swift development and deployment cycle.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates