MatrixPDF is a new phishing and malware toolkit turning benign PDFs into weaponized attack vectors. Using overlays, embedded JavaScript, and social engineering, it bypasses email filters and delivers malicious payloads. Learn how attackers exploit Gmail’s PDF handling in technical detail.
A new threat actor tool called MatrixPDF is enabling cybercriminals to weaponize one of the most trusted file formats in corporate communications: PDF documents.
The MatrixPDF toolkit enables attackers to transform ordinary PDFs into highly deceptive phishing and malware lures that can bypass even well-tuned email security gateways, including Gmail.
By blending overlays, clickable prompts, and embedded JavaScript, MatrixPDF turns every opened PDF into a potential compromise point.
MatrixPDF Toolkit: How the Attack Works
MatrixPDF acts as a builder toolkit, allowing threat actors to import a legitimate PDF as bait and then augment it with malicious features.
Attackers can customize the appearance (adding “Secure Document” titles or padlock icons), blur out the actual content, and overlay prompts designed to mimic secure viewing requirements.
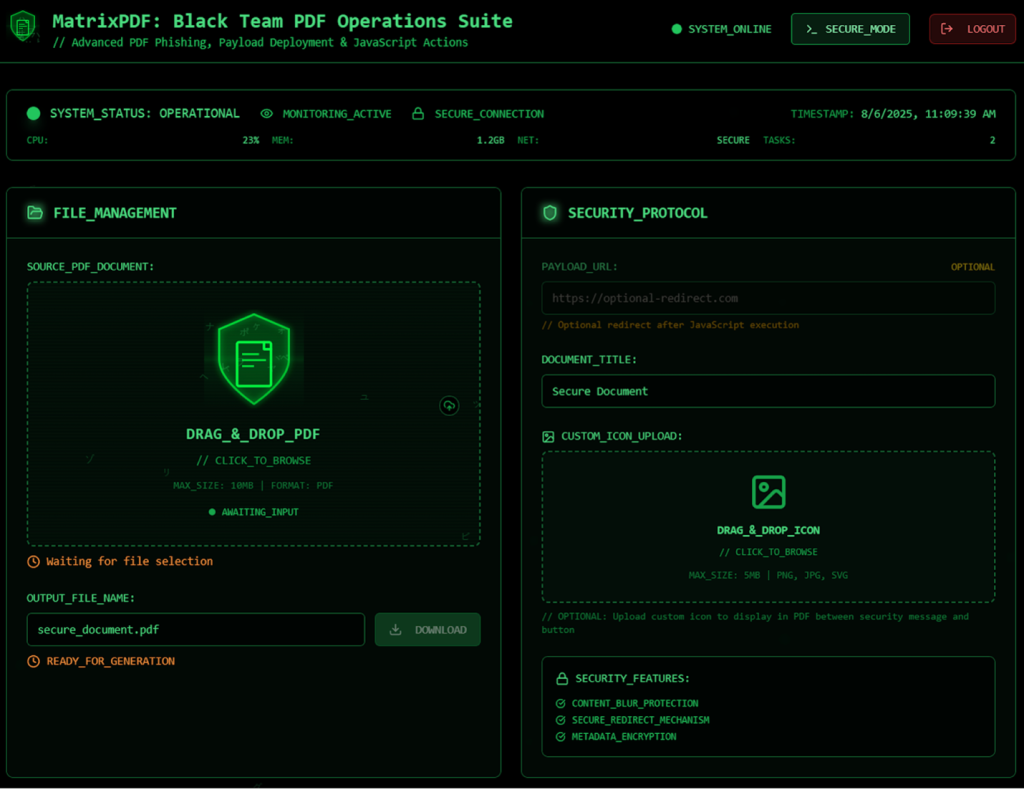
At the heart of the toolkit lies the ability to embed JavaScript into the PDF. This script can trigger actions either upon document open or when a user interacts with a specific button or prompt.
An attacker might configure the PDF to display an “Open Secure Document” button as a phishing lure, redirecting the user to a payload URL. These URLs can lead to phishing sites or serve actual malware, such as trojans disguised as legitimate software installers.
Importantly, MatrixPDF enables attack chains that exploit the fact that most PDF readers and web-based email clients, such as Gmail, don’t execute embedded JavaScript but do allow hyperlinks and button actions.
This enables malicious PDFs to pass through standard email scanners, as no executable content or known malware signatures are present.
Bypassing Email Defenses and Delivering Payloads
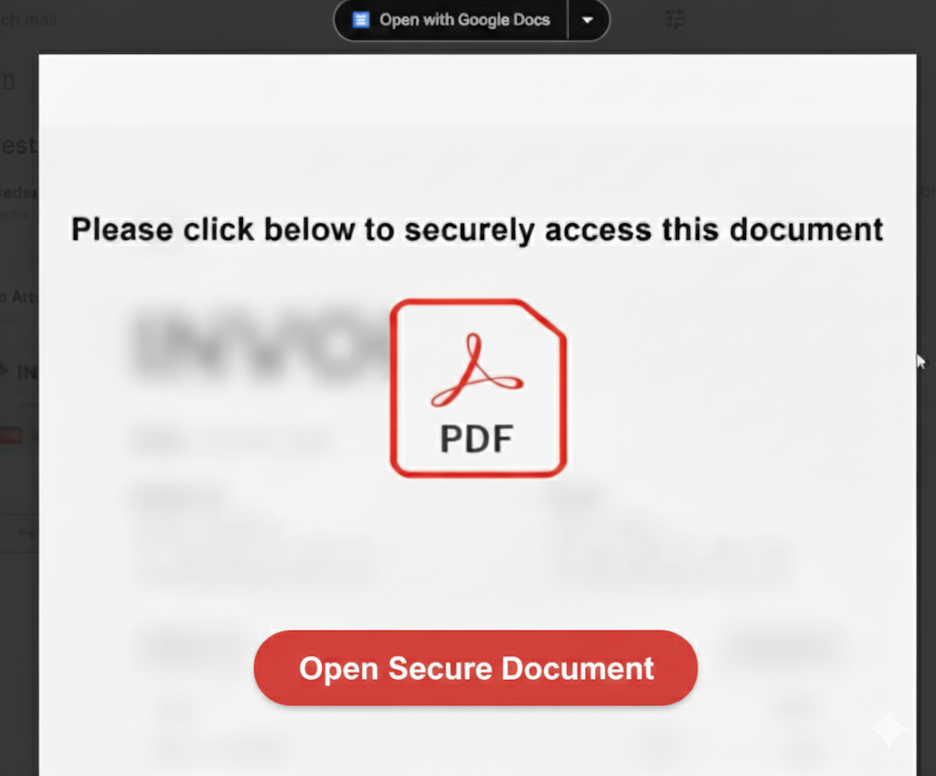
One of MatrixPDF’s most effective strategies is exploiting how email platforms like Gmail handle PDF attachments. In the first method, attackers attach MatrixPDF-generated files to emails. When recipients preview these PDFs in Gmail, the document appears blurred, displaying a fake prompt.
Clicking the prompt redirects the user outside Gmail’s scanning controls to a malicious download site. As this user-initiated action occurs in the browser, any file retrieved bypasses email sandboxing and antivirus filters.
A second method leverages embedded JavaScript within the PDF. If opened in a desktop PDF reader that honors JavaScript (such as Adobe Acrobat), the script attempts to initiate an outbound connection to fetch a payload automatically.
The user may encounter a security dialog, but is likely to grant permission if the document context appears routine, potentially leading to seamless malware delivery.
MatrixPDF highlights a dangerous trend: attackers no longer need to exploit software flaws when they can exploit misplaced trust.
AI-driven email security solutions that analyze attachments for suspicious structures, simulate interactive content in sandboxes, and inspect embedded links are essential for detecting these advanced PDF-based attacks before they reach victims’ inboxes.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates