Cisco has confirmed two critical vulnerabilities affecting its Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) firewalls that are already being exploited in the wild.
Tracked as CVE-2025-20333 and CVE-2025-20362, both flaws allow remote attackers to execute arbitrary code on unpatched devices.
Security advisories from Cisco warn that proof-of-concept exploits are circulating, putting organizations worldwide at immediate risk.
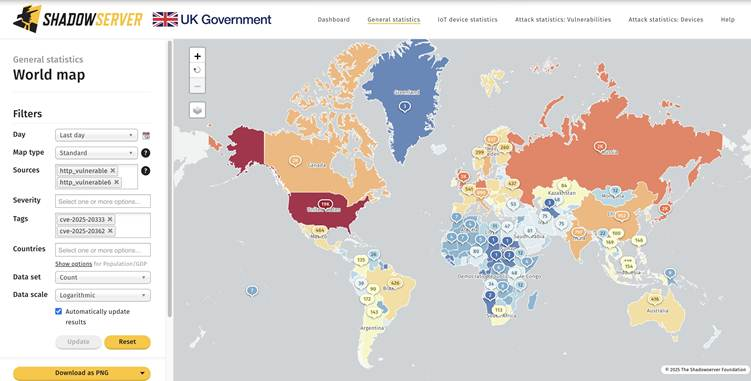
According to Shadowserver Foundation’s daily vulnerable HTTP report, more than 48,800 publicly reachable ASA/FTD instances remain unpatched as of September 29.
The United States accounts for the largest share of exposed hosts, followed by Germany, Brazil, India, and the United Kingdom.
Many small and mid-sized enterprises lack mature patching processes, making them prime targets for intrusion.
These vulnerabilities undermine the firewall’s core function—perimeter defense. An exploited ASA or FTD appliance can permit attackers to bypass network filters, steal sensitive data in transit, or pivot laterally into corporate environments.
Given the high CVSS 3.1 scores and active exploitation, organizations must verify their firewall versions and deploy patches without delay.
Risk Factor Table
| CVE | Affected Products | Impact | Exploit Prerequisites | CVSS 3.1 Score |
|---|---|---|---|---|
| CVE-2025-20333 | Cisco ASA and FTD through 9.18.1.17 | Remote code execution, full OS control | Network access to management interface | 9.8 |
| CVE-2025-20362 | Cisco ASA and FTD through 9.18.1.17 | Privilege escalation, command injection | Valid user credentials | 9.1 |
Organizations still running legacy ASA models or firmware versions before Maintenance Release 9.18.1.18 are most vulnerable.
Cisco’s patches address both issues by reinforcing input validation checks and correcting memory handling routines.
Shadowserver’s live HTTP report publishes updated lists of vulnerable IPs daily, enabling network teams to cross-check their public ranges against known exposures.
Mitigation and Best Practices
- Patch immediately: Download and install ASA/FTD Maintenance Release 9.18.1.18 or later from Cisco’s advisory portal.
- Restrict management access: Limit web and API interfaces to trusted administrative IP addresses only.
- Harden credentials: Enforce multi-factor authentication and strong, unique passwords on all firewall admin accounts.
- Monitor logs: Audit for unusual administrative logins, unexpected configuration modifications, or suspicious traffic flows.
- Network segmentation: Place critical assets behind additional defense layers to contain potential breaches.
The combination of active exploitation, high severity scores, and widespread unpatched installations elevates these 0-days to an urgent security imperative.
Failure to secure ASA and FTD firewalls can result in full network compromise, data exfiltration, and prolonged operational disruption.
Security teams must prioritize patch deployment and implement stringent access controls to close this dangerous gap immediately.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant Updates