Detour Dog, a persistent threat actor tracked since February 2020, has executed an unprecedented campaign leveraging server-side DNS TXT record queries to conditionally redirect site visitors and deliver multi-stage malware, most notably Strela Stealer, across tens of thousands of compromised websites worldwide.
This novel use of DNS as both a covert command-and-control (C2) channel and a malware delivery mechanism allows Detour Dog to evade detection, persist on infected infrastructure, and mislead defenders about the true origin of malicious payloads.
Attack Chain Innovation: DNS Powers Multi-Stage Delivery
Starting in Spring 2025, Detour Dog’s website malware evolved from simple scam redirection to sophisticated remote code execution orchestrated entirely via DNS requests initiated from the web server, invisible to the visitor.
Infected sites query actor-controlled DNS name servers using structured subdomains that embed the visitor IP address, randomized identifiers, and device-specific type values.
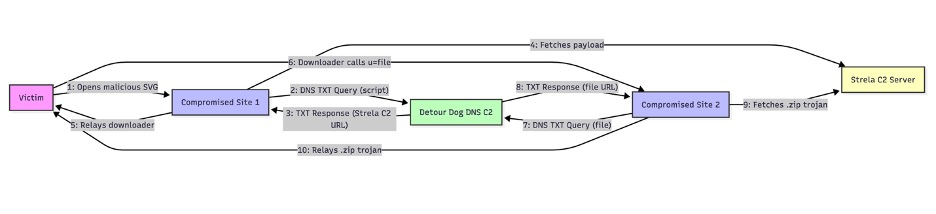
The C2 responds with Base64-encoded TXT records, which are most typically benign but occasionally include a “down” command a trigger for the site to fetch and execute a remote payload using curl, with results delivered to the victim in real-time.
In campaigns observed since June, Detour Dog infrastructure distributed the StarFish backdoor and Strela Stealer infostealer, targeting German and Ukrainian entities via spam emails with malicious SVG attachments.
The attack flow relies on several compromised hosts acting as relays, triggered to download successive payload stages from Strela Stealer C2 servers when DNS TXT responses direct them to endpoints such as script.php or file.php.
IBM X-Force and open-source researchers confirmed Detour Dog domains (e.g., advertipros[.]com, flow-distributor[.]com) hosted both malware and redirects, forging an extensive infrastructure supporting Hive0145’s Strela operations.
Massive Global Footprint, Botnet Propagation, and DNS Defense
Recent sinkholing efforts by the Shadowserver Foundation, targeting Detour Dog’s C2 domains, uncovered over 30,000 infected hosts spanning 584 TLDs, with DNS TXT queries surging to 2 million per hour at peak.
Notably, bot traffic originating from sources such as compromised MikroTik routers (REM Proxy) and the Tofsee botnet dominated the volume, revealing the attacker’s layering of spam-botnet distribution and DNS-powered malware orchestration.
Despite short-lived disruptions, Detour Dog repeatedly transferred control to new C2 domains registered with bulletproof providers.
TXT record logs indicated ongoing adaptation, including commands for download and testing, evolving device-type encodings, and continuous infrastructure expansion.
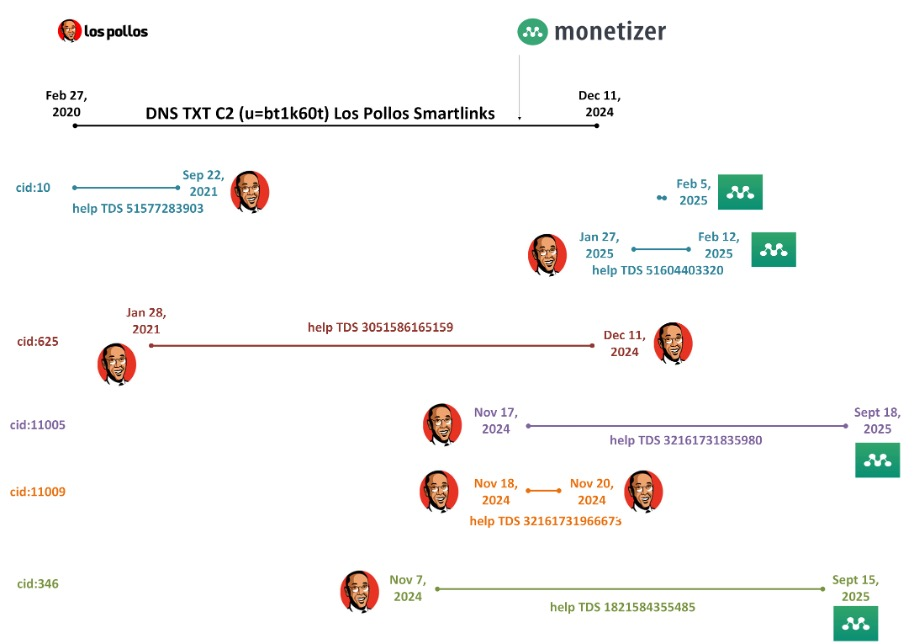
The campaign’s resilience is underpinned by affiliate manipulation of traffic distribution systems (TDS), such as Los Pollos, Help TDS, and Monetizer TDS, which utilize crafted identifiers to mask operations and track flows.
Detour Dog’s DNS-centric malware delivery and traffic redirection model represents a significant advancement in stealthy, persistent cybercrime infrastructure.
Security professionals are advised to monitor DNS TXT queries from web servers for anomalous patterns, leverage IOCs published by threat researchers, and prioritize sinkholing malicious domains to mitigate the broader distribution of infostealer campaigns, such as Strela Stealer.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates