Millions of users install free VPN apps to encrypt mobile traffic, mask IP addresses, and bypass geo-restrictions. Yet a sweeping Zimperium zLabs study of 800 free VPN applications across Android and iOS uncovers systemic security and privacy failures.
Many apps ship with outdated cryptographic libraries, request dangerous permissions, and expose sensitive data, creating enterprise-grade risks for both consumers and organizations embracing bring-your-own-device (BYOD) policies.
Outdated Cryptography and Heartbleed Risk
At the heart of any VPN is its encryption stack. Zimperium’s static analysis revealed three Android VPN clients still link against an antiquated OpenSSL version vulnerable to CVE-2014-0160, the infamous Heartbleed bug.
This flaw permits remote attackers to read arbitrary server memory, exfiltrating TLS session keys, user credentials, and private messages. Despite patches available since 2014, these VPNs continue exposing users’ “encrypted” tunnels to easy compromise.
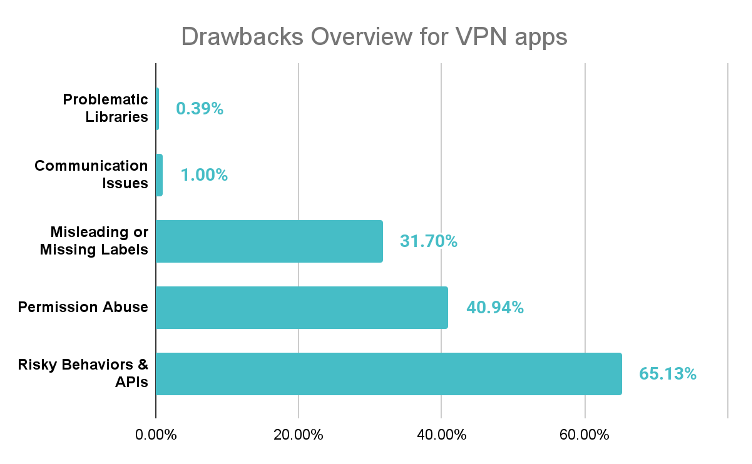
Even more concerning, dynamic testing identified nearly 1% of apps that bypass TLS certificate validation altogether, accepting self-signed or malicious certificates and enabling Man-in-the-Middle (MitM) interception of all traffic.
Permission and Privacy Misuse
Beyond cryptographic shortcomings, permission abuse in free VPN apps is rampant. On Android, dozens of VPNs request AUTHENTICATE_ACCOUNTS and READ_LOGS—privileges usually reserved for system services.
AUTHENTICATE_ACCOUNTS allows an app to add, remove, or alter device accounts and hijack authentication tokens for email or banking apps. READ_LOGS grants system-wide log access, enabling sophisticated keylogging and behavior profiling across all installed apps.
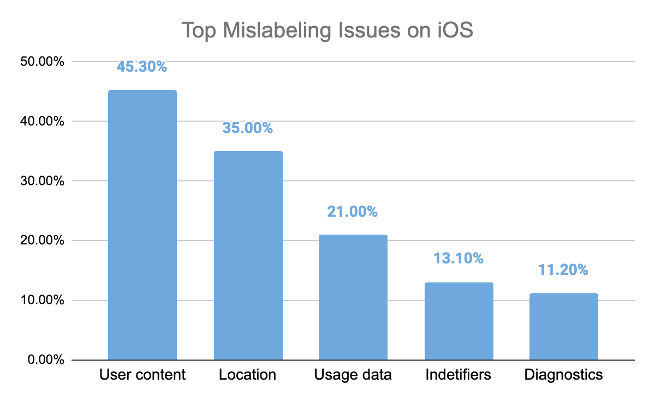
On iOS, over 6% of audited VPN clients sought private entitlements or LOCATION_ALWAYS, enabling persistent GPS tracking and deep OS access far beyond VPN functionality.
In many cases, requested entitlements lack any legitimate justification, indicating either malicious intent or negligent privacy practices.
Enterprise BYOD Risks and App Vetting
For organizations with BYOD policies, vulnerable VPN apps can become corporate Trojan horses.
Zimperium zLabs found numerous apps export activities and content providers without proper permission checks, allowing external applications to query VPN logs, inject malicious configuration profiles, or silently launch UI components to phish user credentials.
Unsecured exported components can even disable encryption on demand, rerouting traffic through attacker-controlled servers. Such behaviors undermine network security controls and expose enterprise credentials, proprietary data, and regulatory-sensitive communications.
Zimperium’s Mobile App Vetting platform addresses these issues by combining advanced static and dynamic analysis to uncover outdated libraries, flag excessive permissions, detect privacy leaks, and identify insecure exported components before apps reach corporate environments.
Continuous monitoring and proactive scanning ensure that only vetted VPN solutions secure an organization’s mobile fleet, closing the door on hidden vulnerabilities and misconfigurations.
In a landscape where “privacy” tools can betray users, rigorous app vetting is no longer optional it’s mission-critical protection for both end users and enterprises.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates