Impact Solutions is the latest turnkey phishing toolkit designed to empower low-skill cybercriminals to launch highly convincing email-based attacks.
Promoted on underground forums as a comprehensive payload delivery framework, the platform offers a graphical user interface that walks an attacker through crafting weaponized attachments, complete with icon spoofing, staged payload support, and built-in evasion techniques.
Organizations face a growing threat as social engineering payload delivery moves from niche malware authorship into the hands of virtually any actor.
User-Friendly Payload Creation with Advanced Evasion
At its core, Impact Solutions features modules for generating three primary file types: Windows shortcut files (.lnk), self-contained HTML pages, and script-embedded SVG images.
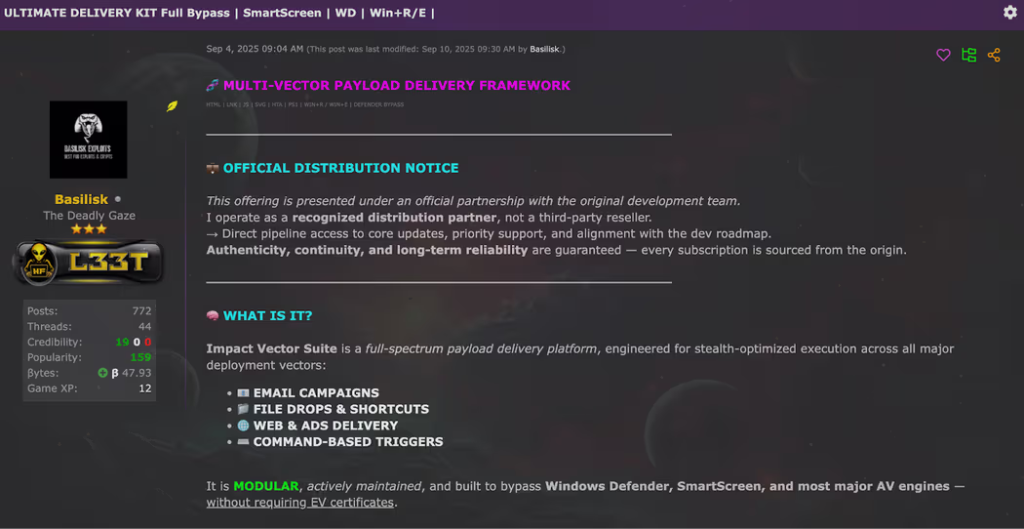
Through simple point-and-click options, an attacker can select a target filename such as “Invoice12345.pdf” and choose a matching icon to mask the true nature of the file.
The shortcut builder can embed a decoy document, so when the victim opens the attachment, a genuine PDF appears, while the hidden executable link silently launches the malicious payload.
Under the hood, each shortcut can include parameters to trigger staged downloads from remote URLs, retrieve second-stage malware, and execute from a stealth location such as %AppData%.
The toolkit also automates several evasion maneuvers, implementing UAC bypass routines to suppress Windows User Account Control prompts, performing anti-virtual machine checks to detect sandbox environments, and leveraging Microsoft SmartScreen bypass techniques, all without requiring the attacker to supply a code-signing certificate.
Persuasive Social Engineering Lures and Browser Spoofs
Beyond file-based attacks, Impact Solutions excels at crafting deceptive HTML smuggling campaigns. Attackers can generate a single HTML file that masquerades as a secure invoice viewer or login portal.
When opened, the page prompts the user to click a button or permit a local file access request; these actions trigger the automatic launch of embedded malware.
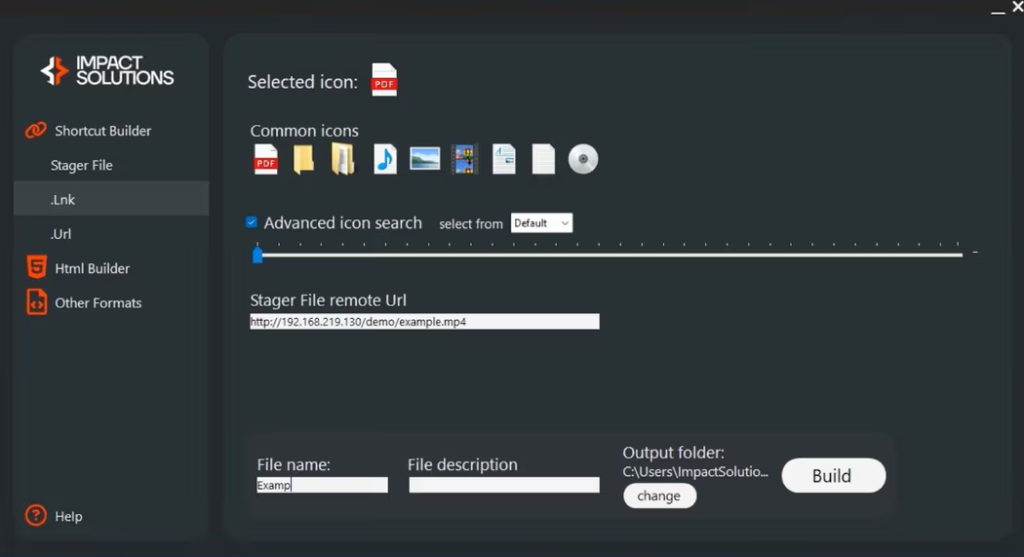
One template even mimics Cloudflare’s “Checking your browser…” screen, instructing victims to press Win+R and paste a Base64-encoded PowerShell command that the page has preloaded onto the clipboard.
This clever trick convinces non-technical users to execute malware under the guise of a routine security check.
The toolkit’s ability to produce SVG images embedded with obfuscated JavaScript further diversifies attack vectors. SVGs are increasingly whitelisted by email gateways, allowing attackers to deliver malicious code with minimal filtering.
Combined with familiar invoice themes and corporate branding, these lures exploit human trust rather than relying on exploitable software bugs.
Defending Against Next-Generation Phishing Threats
Traditional signature-based antivirus and gateway filtering struggle to detect Impact Solutions’ outputs, as each file variant appears unique and legitimate.
Instead, security teams must adopt behavioral analysis to identify suspicious communication patterns and delivery methods.
Platforms leveraging AI-driven behavioral threat detection, such as those that monitor email context, sender anomalies, and user interaction sequences, can flag deviations from typical organizational workflows.
By focusing on the orchestration of the attack rather than static file signatures, defenders can intercept Impact Solutions-generated phishing campaigns before they land in employee inboxes.
As phishing toolkits become more accessible, organizations should reinforce security awareness training, enforce application whitelisting policies, and deploy email security solutions that incorporate behavioral AI.
Only by anticipating the evolving blend of social engineering and technical subterfuge can defenders stay one step ahead of the democratized threat posed by Impact Solutions.
Cyber Awareness Month Offer: Upskill With 100+ Premium Cybersecurity Courses From EHA's Diamond Membership: Join Today