Cisco Talos has uncovered a widespread campaign by a Chinese-speaking cybercrime group dubbed UAT-8099.
Since April 2025, UAT-8099 has systematically targeted vulnerable Internet Information Services (IIS) servers in India, Thailand, Vietnam, Canada, and Brazil.
Their operations center on manipulating search engine optimization (SEO) rankings to redirect high-value traffic to unauthorized advertisements and illegal gambling sites, all while exfiltrating sensitive data from prominent institutions.
Reconnaissance and Initial Compromise
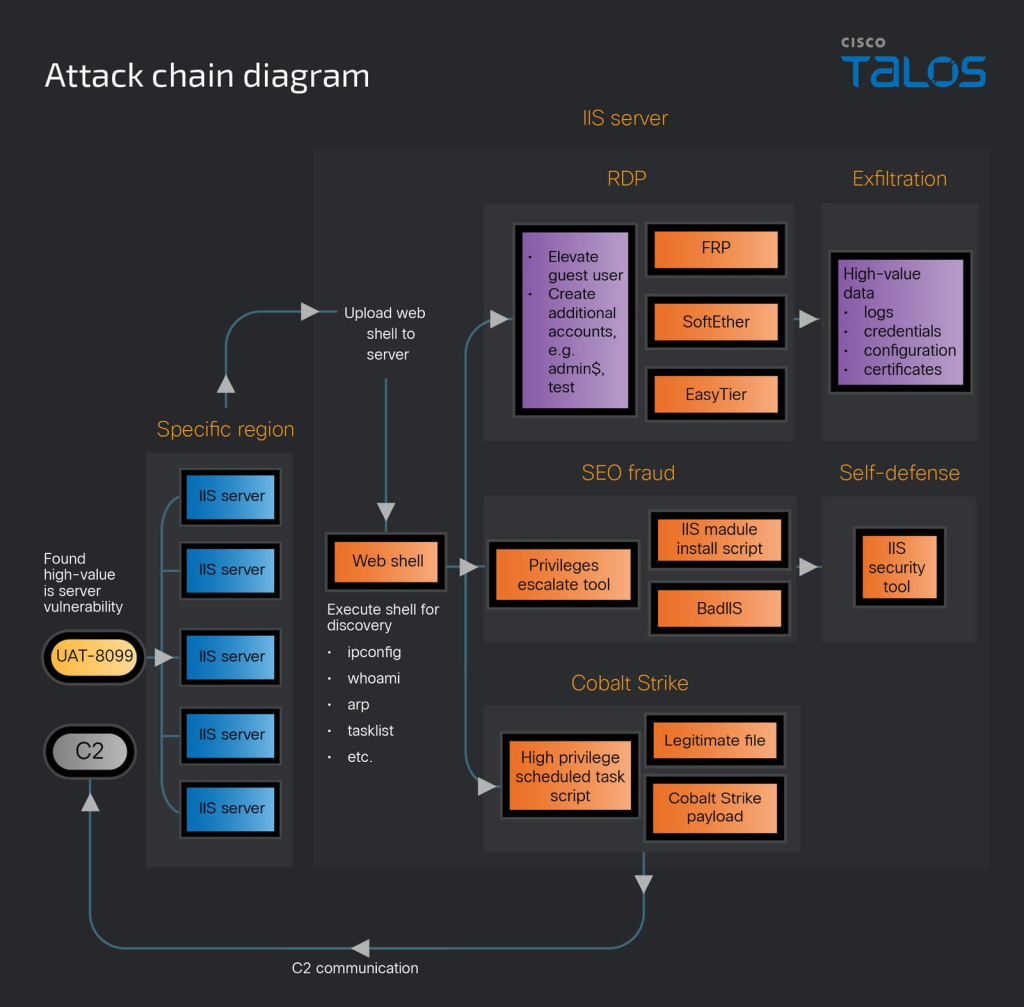
UAT-8099’s campaign begins with automated scans for unpatched IIS servers that permit unrestricted file uploads.
Upon locating a misconfigured server, operators deploy an open-source ASP.NET web shell to execute system commands and harvest environment details.
This foothold allows the creation of a guest user account, which is then elevated to administrator privileges, enabling Remote Desktop Protocol (RDP) access.
Subsequently, the group installs additional web shells and leverages publicly available hacking utilities in conjunction with Cobalt Strike to cement persistence.
During this phase, Talos researchers identified several new variants of the BadIIS malware family.
These variants demonstrate minimal antivirus detection and feature debug messages in simplified Chinese, signaling active development by native-speaking attackers.
To reinforce control, UAT-8099 configures RDP, installs SoftEther VPN and the EasyTier decentralized VPN tool, and sets up FRP reverse proxy tunnels.
Credential dumping via Procdump and data compression with WinRAR follows, while the installation of D_Safe_Manage—an IIS security tool co-opted for malicious purposes checks out competing intruders.
SEO Fraud Techniques and Traffic Diversion
With long-term access secured, UAT-8099 focuses on SEO fraud.
The BadIIS payload manipulates HTTP traffic through two ASP.NET handlers. The OnBeginRequest handler inspects incoming user-agent and referrer headers.
When Googlebot is detected, the handler serves specially crafted backlinks and content tailored to search crawlers, artificially inflating the server’s reputation and boosting ranking for malicious destinations.
Conversely, human visitors redirected from search engines are served injected JavaScript that automatically reroutes browsers to gambling or advertisement portals.
The OnSendResponse handler enhances these efforts by delivering crawler-optimized content before triggering targeted redirects for users encountering error pages.
This dual-mode approach ensures that malicious sites achieve high visibility in search results while unsuspecting users are funneled to revenue-generating platforms.
Mobile users on Android and iOS devices are especially impacted through tailored APK download pages and iOS app landing sites masquerading as legitimate resources.
Cisco Talos urges organizations operating IIS servers to apply the latest security patches without delay and restrict allowable file upload types.
Strong password policies, rigorous account-lockout thresholds, and continuous monitoring of web-server logs are essential defenses against UAT-8099’s techniques.
Deploying endpoint detection solutions with behavioral analytics can help identify anomalous use of web shells and Cobalt Strike beacons.
Talos continues to track the evolution of UAT-8099’s toolkit and recommends regular threat-intelligence updates to stay ahead of emerging BadIIS variants.
Failure to address these vulnerabilities not only jeopardizes organizational operations but also fuels large-scale SEO fraud and credential theft, underscoring the critical need for proactive cybersecurity hygiene.
Cyber Awareness Month Offer: Upskill With 100+ Premium Cybersecurity Courses From EHA's Diamond Membership: Join Today