Cybersecurity researchers at Elastic Security Labs have uncovered significant enhancements to the WARMCOOKIE backdoor, revealing ongoing development efforts by threat actors to expand the malware’s capabilities.
Since its initial discovery in summer 2024, WARMCOOKIE has evolved from a basic reconnaissance tool into a more sophisticated payload delivery platform with enhanced execution capabilities.
Advanced Execution Capabilities Expand Attack Surface
The latest WARMCOOKIE variant introduces four powerful new command handlers that significantly expand threat actors’ operational flexibility on compromised systems.
These additions include PE file execution, DLL execution, PowerShell script execution, and DLL execution with Start export functionality.
The new capabilities utilize a unified execution function that creates temporary directories on the victim’s system, writes malicious content to temporary files, and executes it using legitimate Windows processes, such as rundll32.exe or PowerShell.exe.
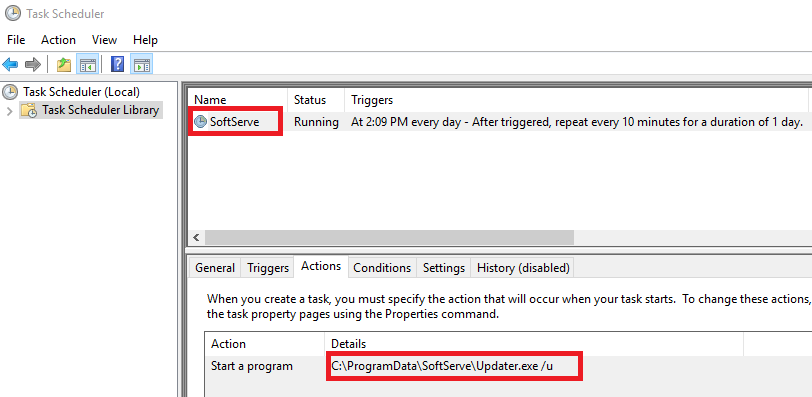
This approach makes detection considerably more challenging as the malware leverages trusted system processes for execution.
The handlers enable operators to deploy various payload types on demand, transforming WARMCOOKIE from a simple backdoor into a versatile delivery mechanism for secondary infections.
Analysis reveals that the most recent builds contain DLL and executable execution functionality, while PowerShell script capabilities appear less frequently across analyzed samples.
Sophisticated Evasion Mechanisms Enhance Stealth Operations
WARMCOOKIE developers have implemented a revolutionary “string bank” system designed to evade behavioral detection systems.
This mechanism dynamically selects legitimate company names for folder paths and scheduled task names during runtime, replacing the previous static installation path with locations that appear authentic to security monitoring tools.
The malware sources these names from actual IT company rating websites, using GetTickCount as a randomization seed for selection.
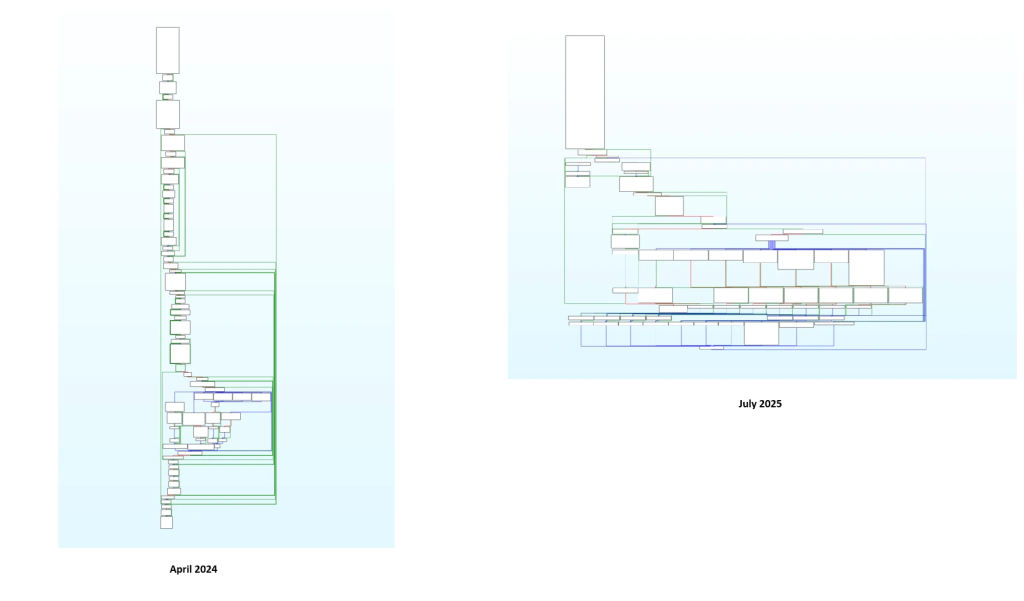
Beyond the string bank implementation, developers have introduced several tactical modifications to break detection signatures.
The command-line parameter changed from /p to /u, while the malware now implements dual GUID-like mutexes for enhanced initialization control and synchronization.
Code optimization efforts have yielded cleaner, more maintainable variants with improved performance characteristics, indicating a potential long-term investment in the malware family’s development.
Infrastructure Analysis Reveals Persistent Campaign Operations
Campaign tracking capabilities have been enhanced through the introduction of campaign ID fields, which provide operators with contextual markers for identifying infection sources.
These identifiers use keywords such as “traffic2,” “bing,” “aws,” “lod2lod,” and “capo,” indicating targeted distribution strategies across different platforms and services.
Research suggests that embedded RC4 keys may serve as operator identification markers, with distinct variants containing unique command handler combinations.
Infrastructure analysis reveals concerning persistence patterns, with threat actors consistently utilizing a default SSL certificate across multiple command-and-control servers.
The certificate (SHA256: 8c5522c6f2ca22af8db14d404dbf5647a1eba13f2b0f73b0a06d8e304bd89cc0) expired in November 2024; however, it continues to appear in new infrastructure deployments, enabling researchers to track operational expansions.
Despite disruption efforts during Europol’s Operation Endgame in May 2025, WARMCOOKIE remains actively distributed through malvertising and spam campaigns, demonstrating the operators’ resilience and commitment to maintaining their malicious infrastructure.
Cyber Awareness Month Offer: Upskill With 100+ Premium Cybersecurity Courses From EHA's Diamond Membership: Join Today