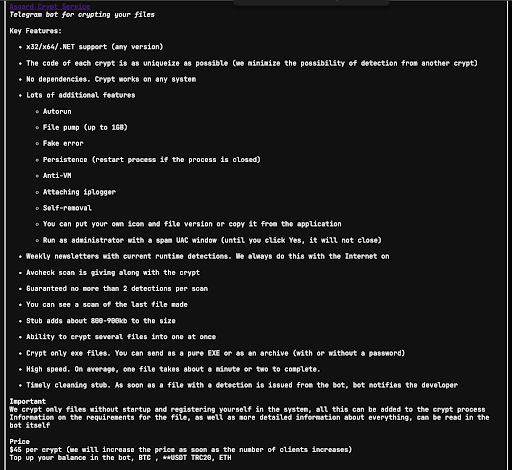
SpyCloud Labs analysts have successfully dissected the complex architecture of Asgard Protector, a sophisticated malware crypter frequently paired with LummaC2 infostealer.
This comprehensive reverse engineering analysis reveals how cybercriminals utilize advanced evasion techniques to circumvent modern security defenses and establish persistent footholds within corporate networks.
Multi-Stage Installation Process Conceals Malicious Intent
Asgard Protector employs a sophisticated multi-stage installation methodology designed to evade static analysis and automated detection systems.
The malware arrives as Nullsoft Scriptable Install System (NSIS) packages, appearing as legitimate software installers while concealing malicious components within self-extracting archive structures.
Upon execution, the NSIS installer extracts multiple files into the Windows %TEMP% directory, including disguised batch scripts bearing mismatched file extensions.
SpyCloud researchers observed instances where critical installation scripts masqueraded as .pst files, such as “Belgium.pst,” deliberately confusing automated analysis tools that rely on file extension-based classification.
The extracted batch script contains heavily obfuscated code that performs multiple security checks before deploying the payload.
These scripts enumerate running processes using tasklist commands, specifically searching for antivirus executables including bdservicehost, SophosHealth, AvastUI, AVGUI, nsWscSvc, and ekrn. If hostile processes are detected, the malware may alter its behavior or terminate execution entirely.
Most remarkably, Asgard Protector reconstructs a functional AutoIt interpreter from constituent binary fragments stored within cabinet files.
The batch script uses extrac32 to extract these components, then employs findstr to locate the PE header offset, concatenating everything beyond that point to create a working autoit.exe binary.
This technique effectively bypasses signature-based detection systems that scan for known AutoIt executables.
Advanced Evasion Techniques Target Sandbox Environments
The reconstructed AutoIt script implements sophisticated anti-analysis mechanisms specifically designed to detect and evade sandbox environments.
One particularly innovative technique involves sending ICMP pings to randomly generated domain names that should not resolve under normal network conditions.
In genuine network environments, these ping attempts would fail silently. However, sandbox systems often intercept and simulate network traffic, providing false positive responses to maintain the illusion of connectivity.
When Asgard Protector receives unexpected ping responses, it immediately recognizes the artificial environment and terminates execution, preventing researchers from observing its actual behavior.
The malware also performs comprehensive process enumeration using targeted tasklist and findstr combinations to identify security software.
Beyond standard antivirus detection, the script searches for specialized security tools, including “opssvc” and “wrsa” services, indicating awareness of enterprise-grade endpoint protection platforms.
Once environmental checks pass, the AutoIt script decrypts an embedded payload using RC4 encryption, then decompresses it using RTLDecompressFragment with the LZNT1 algorithm.
The decrypted payload, most commonly LummaC2 infostealer, is injected directly into explorer.exe memory space, leveraging the trusted system process to avoid behavioral detection systems that monitor suspicious process creation.
LummaC2 Dominates Crypter Usage Statistics
SpyCloud’s comprehensive analysis of over 1,200 Asgard Protector samples from VirusTotal reveals concerning usage patterns that highlight the crypter’s popularity among cybercriminals.
LummaC2 infostealer accounts for more than 69% of all encrypted payloads, reinforcing its position as the dominant commodity malware family.
This statistic aligns with broader threat intelligence, indicating that LummaC2 continues to drive identity exposure risks despite mid-year takedown efforts.
Rhadamanthys represents the second most common payload at approximately 11% of analyzed samples, followed by various other malware families, including ACRStealer, QuasarRAT, Vidar, and Autorun Stealer.
The relatively low percentage of unidentified malware, only four samples out of more than 200 analyzed, demonstrates the crypter’s preference for established, proven malware families rather than experimental or custom-built tools.
Interestingly, many antivirus vendors incorrectly classify Asgard Protector samples as “CypherIT,” likely due to functional similarities between these crypter families.
This misclassification potentially hampers detection efforts and allows Asgard-protected malware to evade security controls calibrated for CypherIT signatures.
For defenders, SpyCloud recommends monitoring for specific command sequences that indicate Asgard Protector activity, including tasklist operations immediately followed by findstr commands targeting security processes, and the use of extrac32 combined with findstr operations to locate PE headers.
These behavioral indicators provide more reliable detection opportunities than static file analysis, given the crypter’s sophisticated obfuscation capabilities.
Cyber Awareness Month Offer: Upskill With 100+ Premium Cybersecurity Courses From EHA's Diamond Membership: Join Today