In a significant escalation of cyber extortion tactics, the hacker collective known as Scattered Lapsus$ Hunters has launched a dedicated leak website on the Tor network, demanding ransom payments from victims in exchange for removing their stolen Salesforce data from public exposure.
This cybercriminal supergroup, a fusion of notable entities such as ShinyHunters, Scattered Spider, and Lapsus$, has been under scrutiny for months by cybersecurity experts and journalists tracking their evolving modus operandi.
Early Inroads Through Social Engineering and API Exploitation
The origins of this large-scale data theft trace back to late 2024 when attackers targeted corporate Salesforce environments primarily through social engineering tactics, specifically voice phishing (vishing).
By impersonating trusted personnel, attackers convinced Salesforce users within targeted companies to install malicious integrations within their Salesforce platforms.
This key step granted the attackers API-level access, enabling the extraction of sensitive corporate data. Major corporations, including Google and Cisco, fell victim to this approach.
Between March and June 2025, the threat actors focused on Salesloft, a sales engagement platform that utilizes an AI chatbot, Drift, which integrates extensively with Salesforce accounts.
The attackers compromised Salesloft’s corporate GitHub repository, harvesting credentials and access keys inadvertently stored within code repositories.
This breach facilitated unauthorized access to Salesloft Drift’s AWS cloud environment, where OAuth tokens used by clients to connect third-party services to Salesloft were obtained.
These tokens allowed attackers to bypass traditional login controls and move laterally across integrated systems, expanding their data exfiltration capabilities.
By August 2025, these OAuth tokens were leveraged in mass data extraction campaigns affecting numerous Salesloft Drift customers, initially thought to impact only Salesforce integrations but later found to include various third-party integrations as well.
The Launch and Operation of the Extortionware Portal
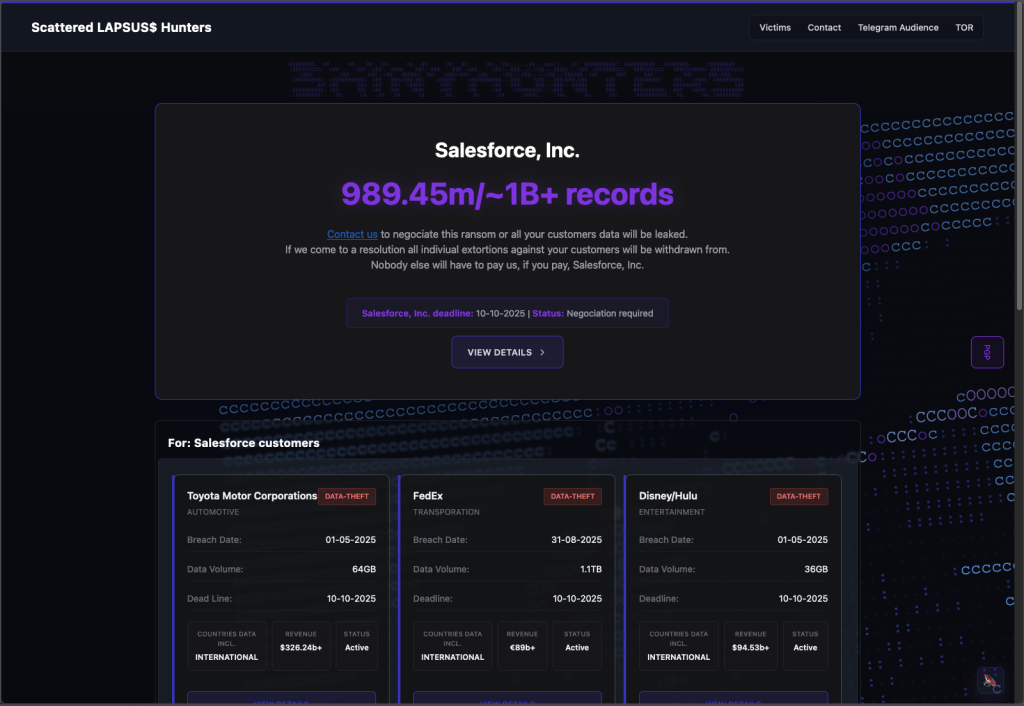
On October 3, 2025, Scattered Lapsus$ Hunters launched their extortionware website, publicly listing affected Salesforce customers alongside claims of the volume of stolen data.
Operating primarily on the Tor Onion network, this portal serves as both a threat vector and a negotiation platform, where victims can potentially pay ransoms to prevent their sensitive business and customer information from being leaked.
The attack group has issued a deadline of October 10 for payments, increasing pressure on impacted organizations and signaling an advanced level of operational coordination.
With this site, the group moves beyond traditional ransomware activities into ransomware-as-a-service territory, potentially enabling others to outsource similar extortion campaigns.
Impact and Lessons on Preventing Similar Attacks
While Salesforce itself clarifies that its core platform was not compromised and that no internal vulnerabilities were exploited, the integration flexibility that makes Salesforce valuable also introduces extensive attack surfaces.
Malicious integrations and OAuth token theft pose significant risks due to their broad access permissions to sensitive CRM data, including customer leads, deal details, and confidential operational information.
The root of these breaches, social engineering and poor credential hygiene, can be prevented through rigorous security hygiene.
Mitigations include enforcing strict controls around API permissions, regularly auditing third-party integrations, employing multi-factor authentication, and sanitizing development repositories to ensure credentials are never stored in code or configuration files.
Security experts emphasize the need to account for user risk vectors in operational security. The Salesloft breach underlines that even indirect access points, such as integrated SaaS applications and cloud environments, require robust protection against social engineering and credential theft to contain such expansive data exposures.
As ransomware and extortion tactics evolve, organizations leveraging Salesforce and connected third-party platforms must bolster defenses against social engineering and integration abuses, or risk falling prey to the increasingly sophisticated ransomware-as-a-service threat landscape presented by groups like Scattered Lapsus$ Hunters.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates