Microsoft is urging enterprises to harden Microsoft Teams as threat actors increasingly weaponize its native collaboration features, chat, meetings, voice/video, screen sharing, and app integrations for initial access, persistence, lateral movement, and data exfiltration.
While Microsoft’s Secure Future Initiative has tightened defaults, durable defense requires actively tuning identity, endpoint, data/app, and network controls aligned to real-world attacker behaviors observed across multiple campaigns.
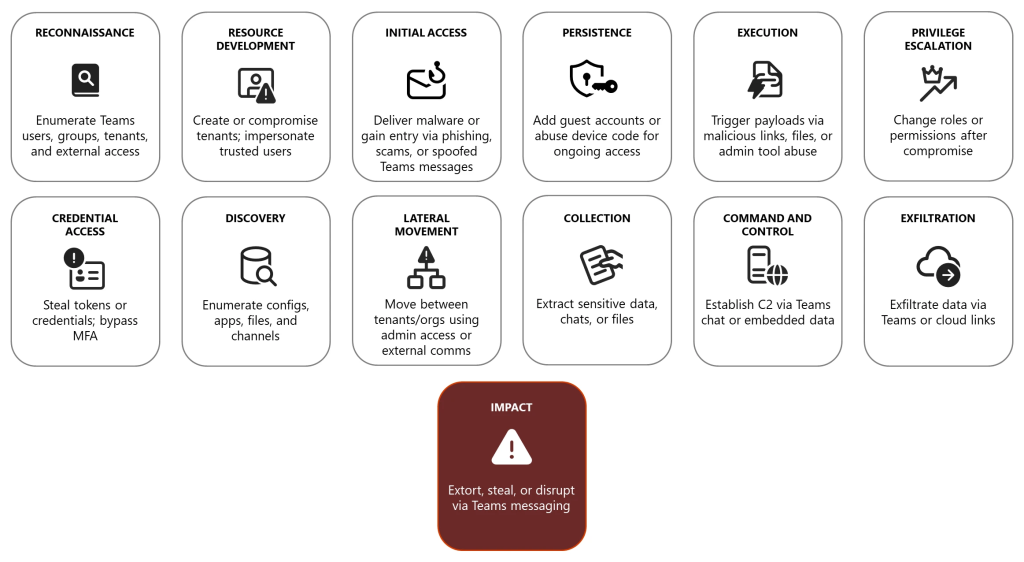
Adversaries initiate reconnaissance by enumerating users, teams, channels, tenant configurations, app permissions, and cross-tenant policies using Microsoft Graph and open-source tooling.
Excessive presence visibility, permissive external access, multi-tenant collaboration, and guest/anonymous settings expose rich signals when privacy and federation restrictions are lax.
Actors map relationships, privileges, and cross-tenant trust to craft targeted social engineering and phishing lures.
Resource development increasingly leverages legitimate Entra ID tenants, custom domains, and branded assets to impersonate help desks or IT, pairing private Teams meeting invites, voice/video, and screen sharing with phone-based vishing to amplify credibility.
Initial Access, Persistence, and Lateral Movement
Initial access commonly hinges on social engineering through Teams chat and meetings, distributing remote monitoring and management tools, steering users to drive-by download sites, or pushing payloads under the guise of IT support.
Recent campaigns echo this playbook with spoofed IT workflows, fake automated notifications, and Teams-themed branding to deliver credential theft, RATs, and loaders used in ransomware operations.
Malvertising has also pushed fake Teams installers carrying info-stealers. Attackers exploit adaptive auth gaps and MFA fatigue, enroll alternate factors, or hijack tokens via device code phishing to maintain session access.
Persistence has been observed through startup shortcuts, accessibility features, and adding guest users or credentials to Teams accounts.
With valid refresh tokens, actors impersonate users over Teams APIs, request OAuth tokens, enumerate apps/files/conversations, and pivot across OneDrive/SharePoint-linked data.
Lateral movement can follow from compromised admin roles or abuse of external communications and tenant trust, including impersonation of IT staff across organizations to expand control.
Collection focuses on Teams chats, channels, and linked SharePoint/OneDrive artifacts, with tooling capable of exporting conversation context at scale.
Command-and-control can be hidden in Teams messages, adaptive cards, or webhook flows, and piggyback on legitimate remote access for interactive control.
To reduce blast radius, organizations should tighten conditional access and network-layer restrictions, continuously audit privileged role assignments, and narrow federation and guest policies.
Proactive monitoring for Teams-specific signals suspicious meeting invites, rapid unsolicited chat patterns, unexpected bot/app activity, anomalous presence access, and atypical OAuth consent flows, can disrupt campaigns before material impact.
Teams-targeting campaigns frequently rely on identity/app abuse and social engineering; CVEs below reflect adjacent Microsoft 365/Office and installer surfaces commonly paired with Teams-themed lures.
| CVE | Affected Product/Component | Impact | Exploit Prerequisites | CVSS 3.1 |
|---|---|---|---|---|
| CVE-2024-38112 | Microsoft Office/HTML handling | User opens a malicious file delivered via chat or link | User opens malicious file delivered via chat or link | 7.8 |
| CVE-2024-30088 | Windows MSHTML Platform | Remote code execution | Drive-by download/social engineering | 8.8 |
| CVE-2024-30080 | Microsoft SharePoint Server | Elevation of privilege/data access | Authenticated foothold or stolen tokens | 8.0 |
| CVE-2024-38100 | Microsoft Identity/OAuth scope | Token abuse/privilege escalation | App consent abuse/social engineering | 7.5 |
Cyber Awareness Month Offer: Upskill With 100+ Premium Cybersecurity Courses From EHA’s Diamond Membership: Join Today