In a novel twist on the ClickFix social engineering formula, threat actors have adopted cache smuggling to deliver malicious payloads without explicitly downloading any files, significantly reducing detection risk.
The campaign employs a phishing lure masquerading as a VPN compliance checking tool, exploiting browser caching to implant a malicious ZIP archive disguised as an image.
This technique avoids typical file downloads and network communications, enabling the malware to bypass security products that flag web requests or scanned downloads.
Phishing Lure Masquerades as VPN Compliance Checker
The attackers hosted a deceptive webpage, formerly reachable at fc-checker[.]dlccdn[.]com, purporting to be a Fortinet VPN Compliance Checker.

By mimicking Fortinet’s branding and user interface, the page duped corporate employees into believing they were executing a legitimate network share executable. Clicking either the file path textbox or the “Open File Explorer” button automatically copied an overly long string to the clipboard.
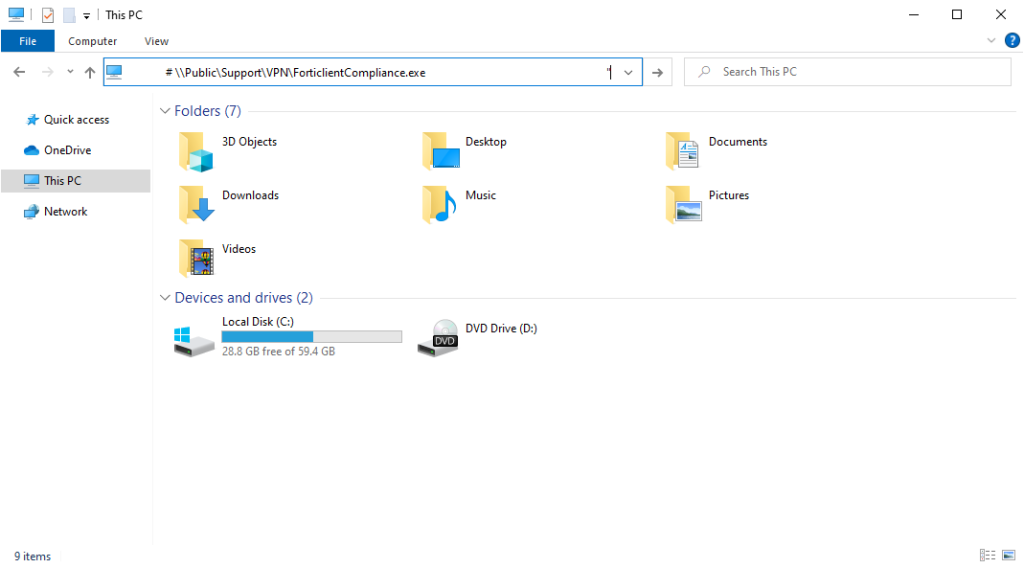
To the user, the only visible portion was the UNC path “\Public\Support\VPN\ForticlientCompliance.exe”, preceded by 139 spaces, which led them to believe that the file already resided on their network.
In reality, the hidden portion launched conhost.exe In headless mode, run a PowerShell script that orchestrates the malicious actions.
Technical Breakdown of Cache Smuggling Delivery
Upon loading the phishing page, obfuscated JavaScript executes a fetch("/5b900a00-71e9-45cf-acc0-d872e1d6cdaa") call, retrieving a fake image with a Content-Type: image/jpeg header.
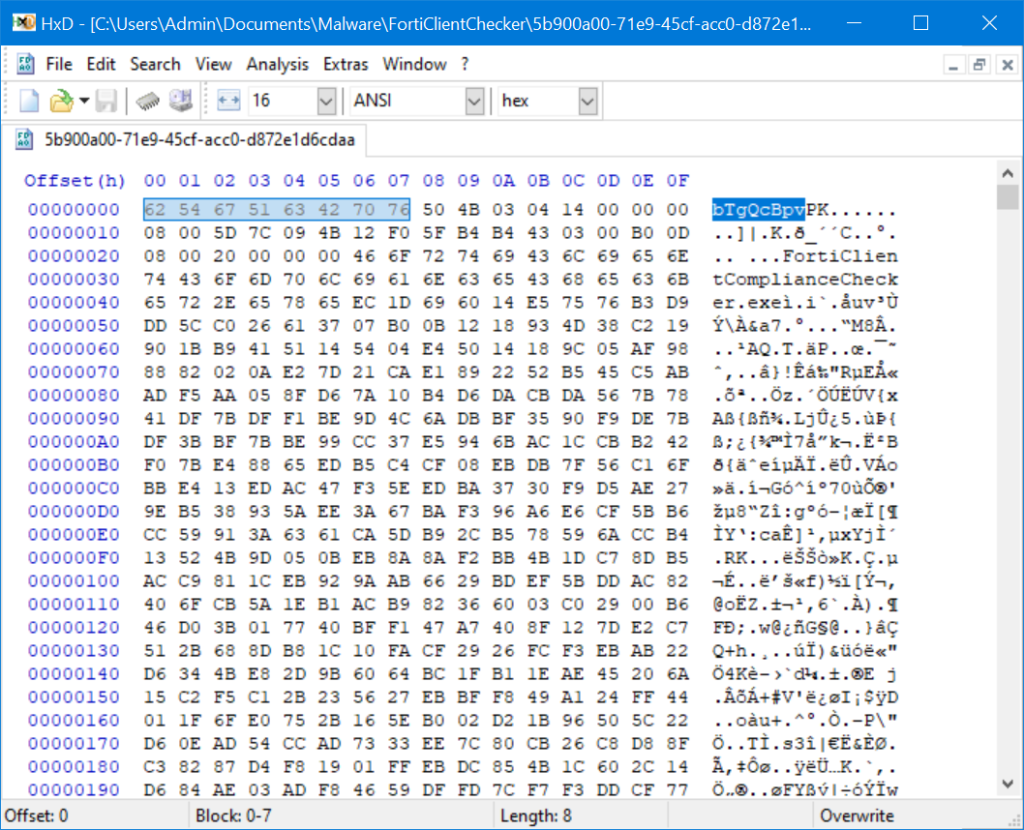
The data, however, lacks any JPEG header and instead contains base64-encoded segments wrapped by unique markers (bTgQcBpv and mX6o0lBw). The browser dutifully caches this “image,” storing the arbitrary data within a cache file alongside genuine assets.
The embedded PowerShell script, executed invisibly, reads the cached blob via a regular expression matching the markers ((?<=bTgQcBpv)(.*?)(?=mX6o0lBw)), extracting the intervening data.
Directly following the opening marker is a ‘PK’ ZIP header, indicating that the extracted payload is a compressed archive. Rather than downloading or communicating externally, the script writes the raw ZIP data from the cache into a file named ComplianceCheck.zip, then extracts and executes its contents.
By leveraging cache smuggling, a technique previously documented but rarely seen in the wild, the attackers evade security tools that monitor network traffic for downloads and flag PowerShell scripts with web-access functions.
Because no network request occurs during script execution, and the file originates from the browser cache, traditional defenses may not register the activity as malicious.
Cache smuggling enables attackers to bypass standard detection mechanisms and covertly implant payloads by exploiting innocuous browser behavior. Organizations should implement the following defenses to mitigate this innovation:
Restrict PowerShell usage to privileged administrators and monitor for headless or hidden PowerShell processes accessing browser cache directories. Deploy secure web gateways or DNS filtering to block access to newly registered or suspicious domains, such as the fc-checker subdomain.
Educate users about ClickFix-style social engineering, emphasizing the importance of skepticism when following instructions to paste long, hidden commands.
By coupling process monitoring with user awareness, security teams can disrupt this advanced cache-based delivery method before it is executed.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates